
A Blockchain is a decentralized network where nodes are running consensus protocols to agree on the state of the blockchain. PBFT consensus protocol is one of the oldest consensus protocols that is not only used in crypto but is already implemented in computer networks and other computer science Domains. In this article, we are going to see the basics of practical byzantine fault tolerance, PBFT consensus protocol, BFT protocol variants, its applications and disadvantages.
Table of Contents
PBFT Consensus Protocol in Crypto
PBFT and BFT belong to a family of consensus protocols which are based on a majority voting scheme. Generally, there are two types of consensus protocol families.
Consensus Protocol families.
- Nakamoto Consensus. In this family, the leader is elected through some form of a lottery scheme. Proof of work proof of stake algorithms fall in this category.
- Majority Voting Schemes. In these protocols leader is elected through multiple rounds of lottery scheme.
Why Consensus Protocol is needed in Crypto and Blockchains?
Bitcoin Blockchain introduced the world to a whole new concept of unforgeable distributed ledgers. Bitcoin Implemented PoW , Proof of work (Hash Puzzle based lottery) consensus algorithm where a leader is chosen with a lottery scheme which then mines a block. Other nodes validate the Block and Transactions and vote in favor of the block by extending the chain by creating a new block by referring to the previous one. If the consensus could not be achieved over previous block, chain will be forked and ultimately the longest chain will be accepted.
So a consensus protocol help reach a consensus on the final state of blockchain. A consensus protocol has three basic properties.
- Termination: All non-faulty nodes/processes eventually decide on the final value. There is no disagreement in the network about the final value. The consensus protocol must be able to terminate itself.
- Agreement: All Nodes and processes eventually decide on the same value without any disagreement
- Validity: The value selected in the end must have been proposed by some participant or node i.e if all processes propose the same value ‘v’ then the algorithm reach at the consensus on “v”.
So, the consensus protocols help to decide on the final values state of blockchain.
BFT and PBFT Consensus Protocol
Most of the current consensus algorithms have been developed for crypto and blockchains. PBFT and BFT algorithms have been long into existence and are also used for other applications. Although PBFT is efficient than PoW, yet it can only tolerate 33% of malicious nodes.
PBFT is being used in Hyperledger fabric which is a private blockchain and supports a variety of services like financial, healthcare and industrial. In addition, PBFT is considered to be an expensive algorithm in terms of bandwidth requirement and the number of messages required to reach at a consensus.
For example, For m faulty nodes the consensus algorithm requires 3m+1 total nodes, 2m+1 communication paths connecting each node and m+1 round of messages q It is obvious that with an increase in the number of faulty nodes, the number of total nodes, required number of communication paths connecting each node and the number of rounds of messages for validation will significantly increase.
PBFT Practical Byzantine Fault Tolerance Algorithm
The basis of Byzantine Fault tolerance Algorithm is Byzantine Generals problem which was explained at Microsoft Research in 1982.
Imagine that several divisions of the Byzantine army are camped outside an enemy city, each division commanded by its own general. The generals can communicate with one another only by messenger. After observing the enemy, they must decide upon a common plan of action. However, some of the generals may be traitors, trying to prevent the loyal generals from reaching an agreement. The generals must decide on when to attack the city, but they need a strong majority of their army to attack at the same time. The generals must have an algorithm to guarantee that (a) all loyal generals decide upon the same plan of action, and (b) a small number of traitors cannot cause the loyal generals to adopt a bad plan. The loyal generals will all do what the algorithm says they should, but the traitors may do anything they wish. The algorithm must guarantee condition (a) regardless of what the traitors do. The loyal generals should not only reach agreement, but should agree upon a reasonable plan.
LESLIE LAMPORT, ROBERT SHOSTAK, and MARSHALL PEASE
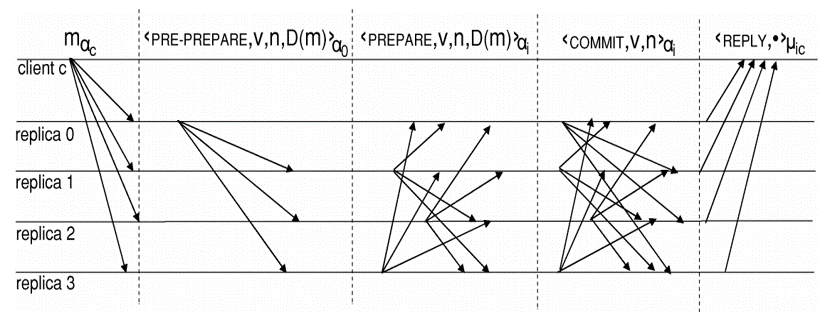
PBFT introduces multiple rounds of voting, so that even if we have some faulty nodes, we may be able to achieve at a consensus. We have already discussed that number of messages in PBFT increases significantly. We are going to see an example of PBFT which is implemented in a computer network protocol.For 1 client and 4x replicas(1x primary,3x secondary), the number of messages required to reach a consensus can be counted as:-
- 4x messages round-1 where client sends messages to all four replicas.
- 3x messages round-2, where the first replica sends messages to the rest of 3x replicas.
- 9x messages round-3, where the three replicas will send messages to each other and also replica 0.
- 12x messages round-4, where the first replica also gets involved again and again every replica sends messages to each other.
- 4x message round-5, where all replicas forward the results to the client.
PBFT Disadvantages.
The major disadvantages of PBFT are as under:-
- PBFT network can tolerate only 33% of faulty nodes.
- The network is not scalable as the number of communication paths increase manyfold with an increase in nodes.
- PBFT algorithm requires a lot of exchange of messages increasing bandwidth requirement.
- PBFT is vulnerable to DOS attacks.
- Special mechanisms are required to mitigate the Sybil attack.
PBFT VS POW
PBFT and POW consensus algorithms(which is implanted in Bitcoin and Ethereum) can be compared as under:-
| Features | POW | PBFT |
| Goal | Totally order transactions on a distributed ledger i.e Blockchain | State Machine Replication Protocol |
| Consensus Latency | One hour | low |
| Energy Consumption | High | low |
| Vulnerability to Sybil Attack | No | Yes |
| Vulnerability | Vulnerable to 51% Attack or >= 25% computing power acquired by an adversary | More than 33% faulty nodes |
| Throughput | Low (7 TPS) | High (tens of thousands TPS) |
| Scalability (Number of nodes in a network) | Support thousands of clients | Support thousands of clients |
| Consensus Finality | PoW does not guarantee consensus finality, once a block is mined. The block can be orphaned and only the chain with longest PoW is accepted. Therefore, a TX confirmation takes 6 x Blocks generation time | After end of the protocol, all the correct nodes agree or not agree on the order of transactions |
| Limitations | High computation power, high energy requirement, size of Blockchain, latency in TX confirmation | High communication overhead, less faulty node tolerance, subject to DoS attack (due to network latency), vulnerability to Sybil attack, suitable only for small network with 10-100 nodes |
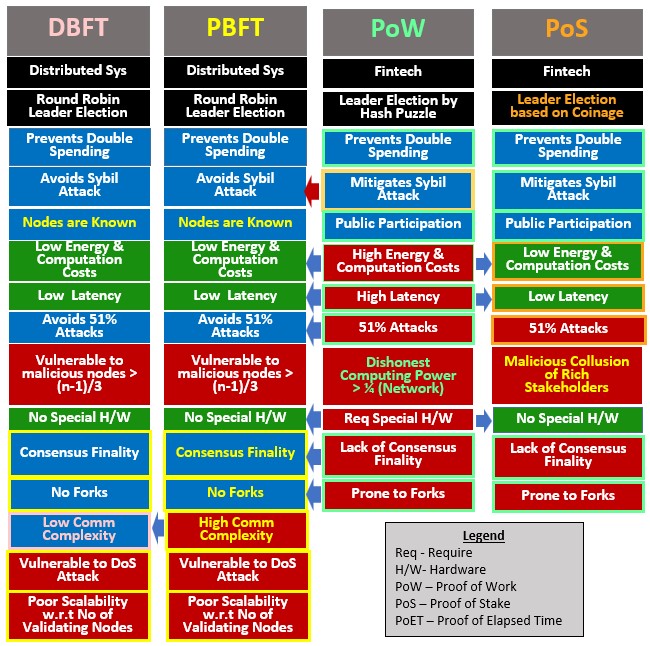
Performance PBFT VS BFT VS PoW vs PoS
While each consensus protocol has some limitations, each provides some distinct set of advantages that can be used in specific applications of Web 3.0. The performance and requirements of major consensus protocols can be summed up in the following figure.
FAQ
Why PBFT was not implemented in Bitcoin as a consensus protocol for achieving agreement on the order of transactions?
BFT protocol’s agreement process is vulnerable to Sybil attacks. To counter Sybil Attack, Bitcoin implements PoW based consensus mechanism. That is computation power-based voting instead of one entity one vote system. However, PoW pays an enormous price in terms of low throughput and Tx latency
What is the major disadvantage of PBFT and BFT algorithms?
The major disadvantage of PBFT, BFT algorithms is that they require a greater exchange of messages which in turn requires greater bandwidth. There are also not scalable and prone to Sybil attacks.
Where PBFT is used in crypto?
PBFT is used in the Hyperfiber ledger which is a permissioned private blockchain.