
The tutorial will cover the best free data acquisition tools that can be used in windows as well as Linux environments. Data acquisition is the first step for digital forensics and it is necessary to take image of the hard drive or USB drives to avoid tempering with the digital evidence. The best practice for digital forensics is to have multiple tools to take multiple images.
Table of Contents
Best Data acquisition tool for Windows
MINI-WINFE is the best data acquisition tool for windows. It is able to create images from windows environments and supports the best forensics tools in the market like FTK imager and X-ray forensics.
WinFE (Windows forensic Environment) is a forensically sound, bootable Windows operation system that was created from a miniature version of windows WinPE by Troy Larson.
Mini-WinFE provides an easy mechanism to build a bootable window. The WinBuilder can be used for customizing WinPEs for different projects but our focus will be to build Mini-Winfe for data acquisition
There are various versions of Mini-WinFE available online and not all may work for you. In this tutorial, we are going to use a 2017 Build with a 64-bit windows 10 kernel and 64-bit FTK Imager. This combination will help us to take images from most of the systems.
The full documentation of the project can be found here.
Why Use Mini-WinFE
There are many commercial tools as well as Linux tools available for data acquisition. However, with secure boot enabled in many systems, these tools may not be allowed to run by your target hardware. Secure boot checks the signature of the OS before loading it. Mini-WinFE uses actual windows kernel so it is able to bypass the safe boot option and it can easily be used to take disk image.
Data acquisition with Mini WinFe
There are a few steps that we need to follow to take image with Mini-WinFE
- Build a Mini-WinFE ISO
- Make a bootable USB with Mini-WinFE
- Boot with Mini-WinFE and take an image of the target drive with FTK Imager.
For the tutorial, we will take an image of a USB to another USB while booted in Mini-WinFE.
Build a Mini-WinFE ISO
To build a working Mini-WinFE ISO we need a few things ready with exact versions. The tutorial has been designed to avoid any problems. So exact versions are being mentioned as not all versions work well.
1. Windows 10
You need an official windows ISO image in extracted format. Fo the tutorial, we are using Windows 10 ISO image. If you don’t have a windows image, download windows 10 64 bit the latest image with the windows media creation tool. Mount the ISO on your windows with a double click which will open the image as a drive on your Windows machine.
2. FTK Imager 64 bit
FTK Imager has been updated but to work with the Mini-WinFE, we need the particular version. So, Download FTK Imager 4.2.0 from the official access data website.
3. Mini-WinFE Builder
Now download the Mini-WinFE builder from the official website. (http://reboot.pro/files/file/375-mini-winfe/)
4. Rufus
We will be using Rufus to make a bootable USB. So, download Rufus.
Building Mini-WinFE Image
- Install FTK Imager 4.2 on your PC.Go to windows in your windows/system32 folder. Search for all files with the following names and copy them to the FTK installation folder in your program files.
a. Mfc*
b. Msvcp*
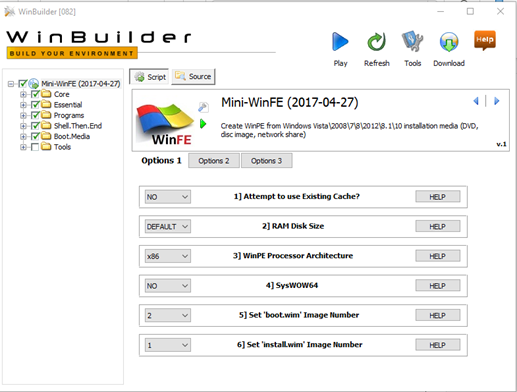
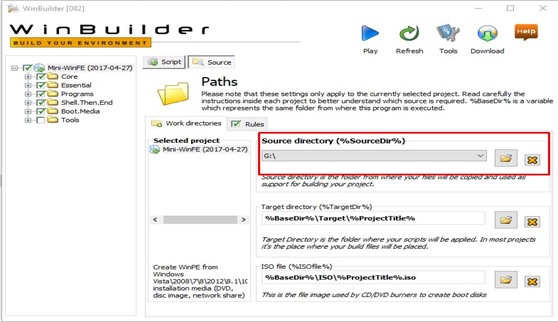
c. Vcruntime*- Open the Mini-winFE package ”win builder”. Go to the Source tab and select the source of the windows 10 drive which we have already mounted.
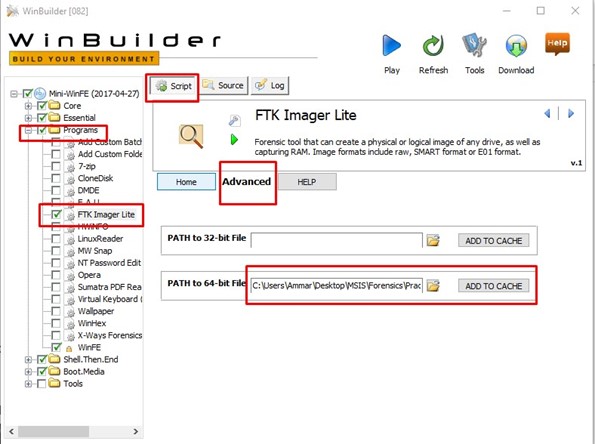
- Now select programs from the left section. Select FTK imager and click on the script tab. Now give the path for the FTK imager 64-bit executable file. Click on add to the cache.
- Once done click on play. Now your file as an ISO image will be generated and will be available in the working directory.
Make a Bootable USB with Mini-WinFE Image
Now, we need to write the ISO image to a bootable USB. Open Rufus and select the image file. Select partition type as GPT as target system as UEFI. Then click create.
Boot with Mini-WinFE and take USB image with FTK Imager
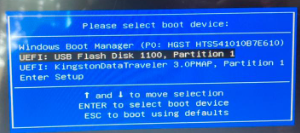
Now boot from USB. You may need to press the escape, F12, F8 keys to open up the boot menu on your PC. You must connect the target USB(where the image will be stored) and the source USB(whose image is to be taken) before booting up the Mini-WinFE.
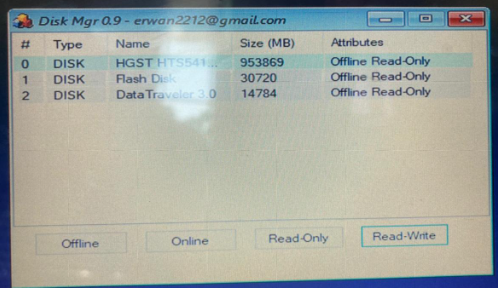
- Once Mini-WinFE loads, you will see a menu with all your drives. Now you can select what you want to do with your drives. Select offline read-only mode for evidence drive. Select online read/write mode for the target drive where you will be storing your image.
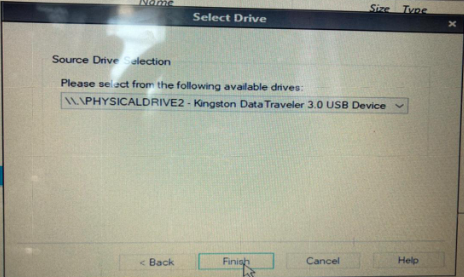
- Now right click on the desktop, and a menu will appear. Click on FTK Imager, FTK Imager will start.
- Now go to the file, take an image, and select the drive, image type and destination. Click start to take the image. After the process is completer, you can see the MD5 and SHA hash to confirm that image has been taken successfully.
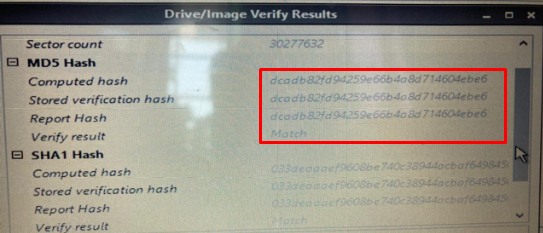
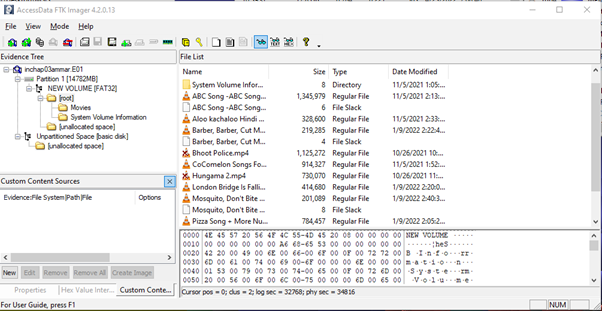
Now you can remove the target USB drive and can open it on any other PC on FTK image or autopsy to verify the contents of the image.
Best Data Acquisition tool for Linux
Linux is your best friend if you are low on the budget in cyber security or the digital forensics domain. The newer versions of Linux automatically mount a drive. So, it can modify the evidence.
Best Linux Distros for Forensics and Data Acquisition
There are many linux based distros that mount the drives as read only. So, they can be used for forensic tools. Some of the most popular ones are as under:-
- Penguin Sleuth Kit
- CAINE
- Deft
- Kali Linux
- Knoppix
- SANS Investigative Forensic Toolkit (SIFT)
Best tools for data acquisition on Linux
There are two popular tools that are totally free and can be used to take a drive or logical image.
- DD (Data Dump)
- DCFLDD
Data acquisition with DD command
DD is an inbuilt command in Linux. The dd command was intended as a data management tool and is not designed for forensics acquisitions. However, it does the job well.
Setting up Linux Distro
- Boot from a forensic distro. I am using kali in forensic mode. Better is to use it in root sudo mode { sudo -i}. This will save from typing the sudo command over and over again.
- Now give the command “lsblk”. It will list down all devices attached. I have two USBs connected to my virtual machine. You can see both (sdb and sdc). Both are not mounted which confirms it is in forensics mode.
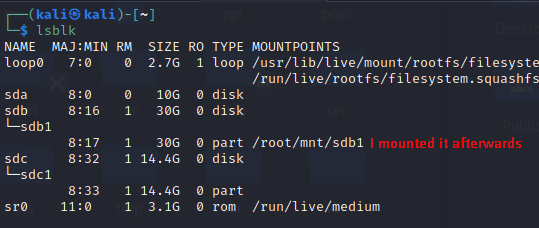
Mounting the target drive
Now we need to mount our target drive. It will be usb disk which we will be using to save the image. Check the location of drives.
Sudo fdisk -l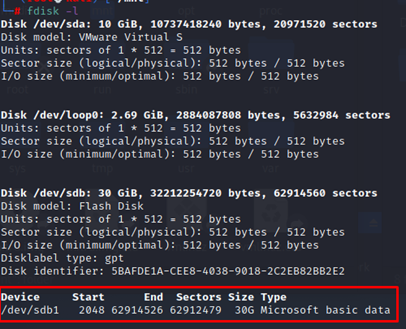
Make the folder/directory where USB will be mounted. Now Mount the USB to the directory you made. you can check if it is mounted correctly with “Lsblk” command
Sudo mkdir -p ~/mnt/sdb1
Mount -o rw /dev/sdb1 ~/mnt/sdb1
Lsblk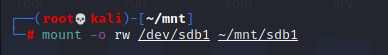
Taking USB image with DD command
Change to the target directory and then use the command.
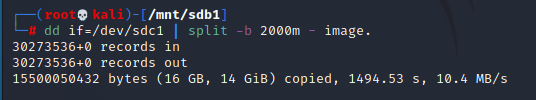
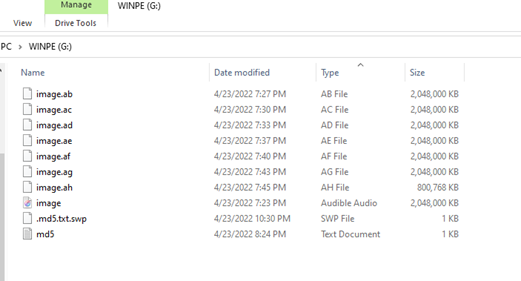
dd if=/dev/sdb | split -b 650m – image.Now the command takes the mounted image from the input field “if=/dev/sdb” and makes its image as split files of 650 MB in the current directory. Note that the image has a period in the end that will make sure that there will be a period between the name and extension of created image files.
Verify the integrity of USB image
Now list all files with following command.
Ls -l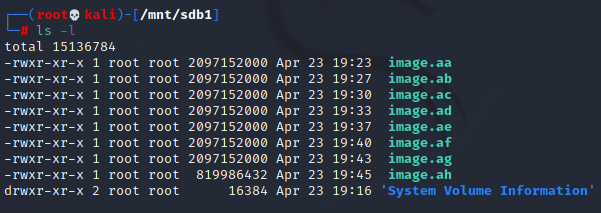
Now, we need to check the hashes whether we have obtained a good image or not. Run the following commands to generate hashes.
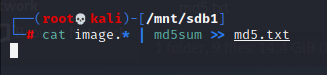
Md5sum /dev/sdc1 >md5.txt
Cat image.* | md5sum >> md5.txt
The first command will take the image of USB drive and save it into md5.txt file. The second command will concatenate the image files into one file and then take the hash and pend it to the existing file.
Now open the text file and compare them.
Nano md5.txt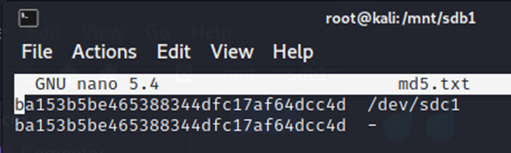
Now if the hash matches, it means we have taken a good image. You can open the image in any forensic tool to verify the image on the forensic workstation.
Data acquisition with DCFLDD
DCFLDD command has various additional features which are:
- Specify hex patterns or text for clearing disk space
- Log errors to an output file for analysis and review
- Use several hashing options
- Refer to a status display indicating the progress of the acquisition in bytes
- Split data acquisitions into segmented volumes with numeric extensions
- Verify acquired data with original disk or media data
We are going to consider the same methodology to prepare our target drive and mounting images. After the sane setup, we need to change only the command.
Installing dcfldd command on kali Linux
First, if the command is not available, install it with the following command.
apt-get install dcfldd
Data acquisition with dcfldd command
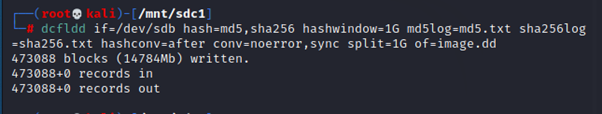
Now run the following command to create the image. You must follow the same steps as mentioned above to mount the target drive first.
Dcfldd if=/dev/sdb hash=md5,sha256 hashwindow=1G md5log=md5.txt sha256=sha256.txt hashconv=after conv=noerror,sync split=1G of=image.ddThe command will take the input field”dev/sdb” create its hash by md5 and sha256 save it in mentioned files and create image.dd in a split of 1GB files.
Verify the Image with dcfldd
You can manually calculate hash as discussed above or use the verify “vf” flag with dcfldd command to verify the images.
If it’s a split file, use the first command to verify the file. If it’s a single file use the second command.
Cat image.dd.* | dcfldd vf=/dev/sdb
Dcfldd vf /dev/sdb image.dd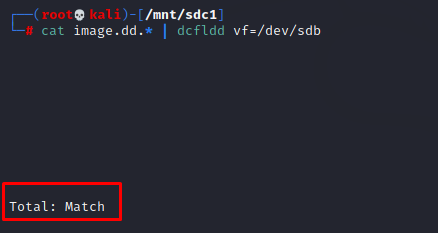
FAQ
What is the best window based tool for data acquisition?
Mini-Winfe is the best tool for data acquisition in a windows environment. It supports a variety of forensic tools like FTK imager, X-ray forensics.
What is the difference in dd and dcfldd command?
dd command was designed as a disk management utility. dcfldd is enhanced version of dd which is used to take forensically sound data acquisition and image. dcfldd supports more advanced hashing and capturing techniques.
What are the free tools for data acquisition?
Mini-WinFe is windows based tool whereas dd and dcfldd commands can be used for taking disk image in a Linux environment.