Embark on a virtual heist with the OverTheWire Bandit challenge! Your mission, should you choose to accept it, is to breach the security layers of the Bandit system. Compile a concise report detailing your progress, strategies, and any lessons learned. This hands-on exercise will make you proficient in the Linux command line.
Table of Contents
Level 0 Bandit
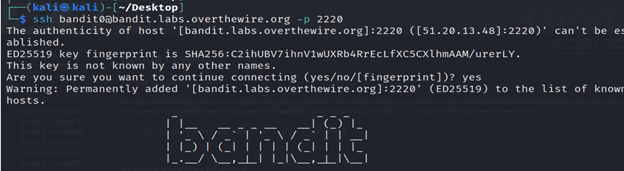
The goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org, on port 2220. The username is bandit0 and the password is bandit0.
- Connect by using the command ssh and the password given(bandit0) through the given port.
- For this we type the command ssh [email protected] –p 2220
Level 0-level 1 Bandit
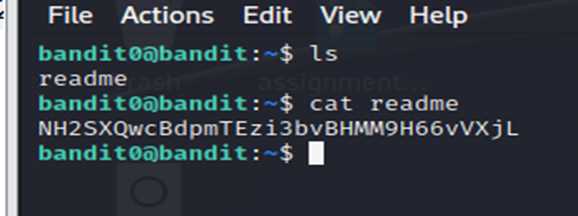
The password for the next level is stored in a file called readme located in the home directory. Use this password to log into bandit1 using SSH.
- List all the files in the directory by the command ls command.
- Now simply use cat readme to display the contents of this file.
Level 1-level 2 Bandit
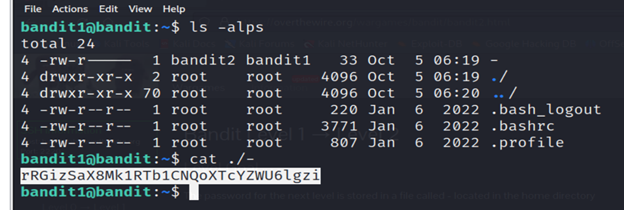
The password for the next level is stored in a file called – located in the home directory
- ssh [email protected] .org -p 2220
- Enter the password found.
- Now, List all the files in the directory by the command Ls -alps.
- ls command lists files and directories within the file system.
- We can see that the file is in a dashed format so for opening a dashed file we use the following command cat ./-
- Exit from the level using exit command.
Level 2-level 3 Bandit
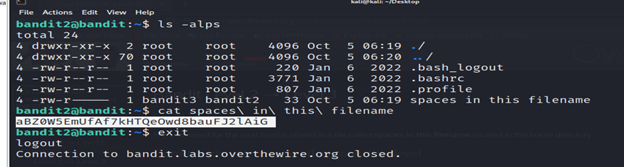
The password for the next level is stored in a file called spaces in this filename located in the home directory
- ssh [email protected] .org -p 2220
- Enter the password found.
- Now, List all the files in the directory by the command Ls -alps.
- ls command lists files and directories within the file system.
- For opening a file having spaces in between we use the command
- cat spaces\ in\ this\ filename
- Exit from the level using exit command.
Level 3-level 4 Bandit
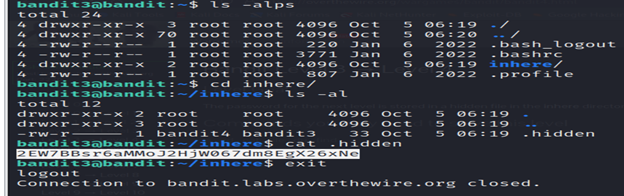
The password for the next level is stored in a hidden file in the inhere directory.
Go to desktop in kali terminal.
- ssh [email protected] .org -p 2220
- Enter the password found.
- Now, List all the files in the directory by the command Ls -alps.
- ls command lists files and directories within the file system.
- Go to the inhere file using cd command.
- list all the sub-files and folders using ls –al command.
- You will find a hidden file. Read that file using the cat command.
- Exit from the level using exit command.
Level 4-level 5 Bandit
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
- ssh [email protected] .org -p 2220
- Enter the password found.
- The password for the next level is stored in the only human-readable file in the inhere directory.
- Go to the inhere file using cd command.
- Now, List all the files in the directory by command Ls.
- ls command lists files and directories within the file system.
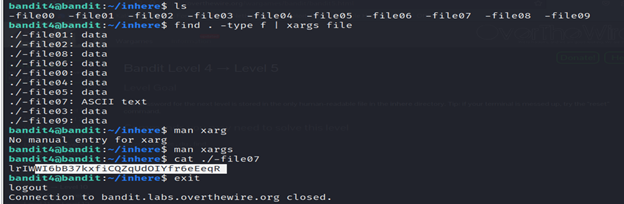
- Run the command find . -type f | xargs file
- find . -type f: This part of the command uses the find command to locate all files (-type f) starting from the current directory (.). It searches for regular files only.
- |: The pipe (|) symbol is used to redirect the output of the find command as input to the next command.
- xargs file: The xargs command is used to pass the list of file names obtained from find as arguments to the file command. The file command is then used to determine the type of each file.
- You will find an ASCII file which is the only human-readable file. Read that file using the cat command.
- Exit from the level using exit command.
Level 5-level 6 Bandit
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
- human-readable
- 1033 bytes in size
- not executable
- ssh [email protected] .org -p 2220
- Enter the password found.
- Now, List all the files in the directory by the command Ls -alps.
- ls command lists files and directories within the file system.
- Go to the inhere file using cd command.
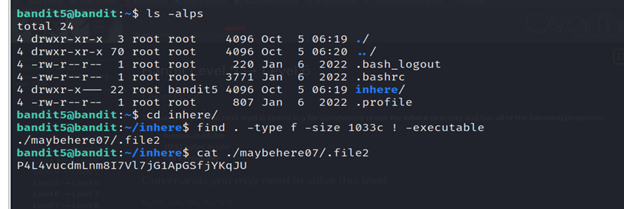
- Run the command find . -type f -size 1033c ! -executable
- -type f: Specifies that the search should include regular files only, not directories.
- -size 1033c: Specifies that the files should have a size of exactly 1033 bytes.
- ! -executable: Specifies that the files should not be executable.
- You will find a file of name ./maybehere/.file2. Read that using the cat command.
- Exit from the level using exit command.
Level 6-level 7 Bandit
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
- ssh [email protected] .org -p 2220
- Enter the password found.
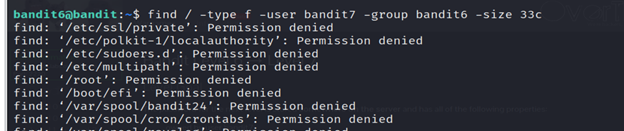
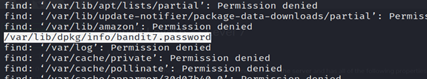
- Run the command find / -type f -user bandit7 -group baandit6 -size 33c
- find /: Initiates the find command, starting the search from the root directory (/).
- type f: Specifies that the search should include only regular files, not directories.
- -user bandit7: Filters the search to include only files owned by the user “bandit7.”
- -group baandit6: Filters the search to include only files belonging to the group “baandit6.”
- -size 33c: Filters the search to include only files with a size of 33 bytes.
- You will find bandit7.password file.
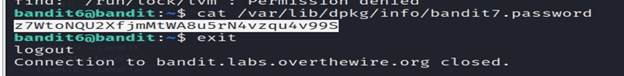
- To view the contents of the file, you can use a command-cat /var/lib/dpkg/info/bandit7.password
- Exit from the level using exit command.
Level 7-level 8 Bandit
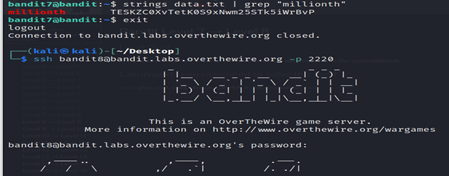
The password for the next level is stored in the file data.txt next to the word millionth
- ssh [email protected] .org -p 2220
- Enter the password found.
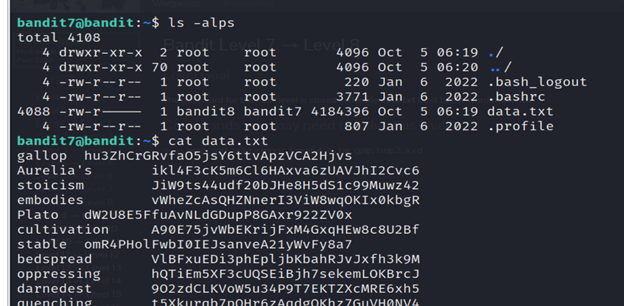
- Now, List all the files in the directory by the command Ls -alps.
- ls command lists files and directories within the file system.
- Read the data.txt file using the cat command.
- The command strings data.txt | grep “millionth” is used to search for the string “millionth” within the contents of the file data.txt
- Exit from the level using exit command.
Level 8- level 9 Bandit
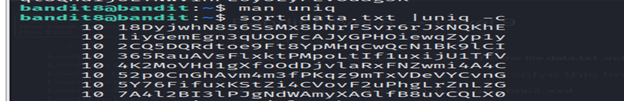
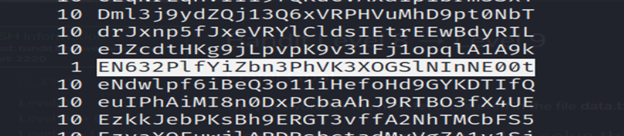
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
- ssh [email protected] .org -p 2220
- Enter the password found.
- We’ll use ls -alps and cat data.txt commands to read the data.txt file.
- The command sort data.txt | uniq -c is used to count the occurrences of each unique line in the file data.txt after sorting the lines.
- you will find the password that occurs only once.
- Exit from the level using exit command.
Level 9-level 10 Bandit
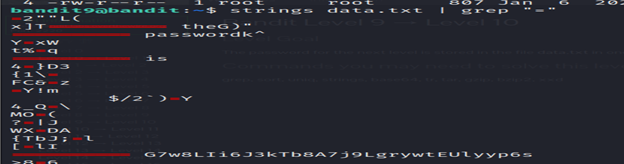
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-We’ll use ls -alps command.
4-The command strings data.txt | grep “=” is used to search for lines containing the equal sign “=” within the contents of the file data.txt.
5- Exit from the level using exit command.
Level 10-level 11 Bandit
The password for the next level is stored in the file data.txt, which contains base64 encoded data
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-Read the file data.txt using cat command.
4-When you run man followed by the name of a command, it shows you the manual page for that command.
5-base64 command to encode or decode data in base64 format.
6-This command (base64 -d data.txt) reads the base64-encoded content from data.txt, decodes it.
7- Exit from the level using exit command.
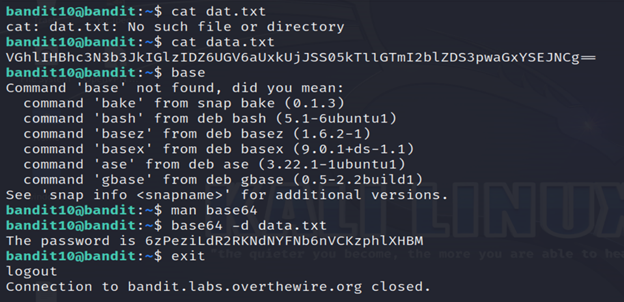
Level 11-level 12 Bandit
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-Read the file data.txt using cat command.
Here, we’ll use ROT 13 and decrypt it using cyberchef.
4- Exit from the level using exit command.
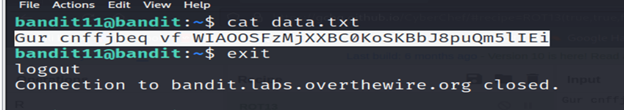
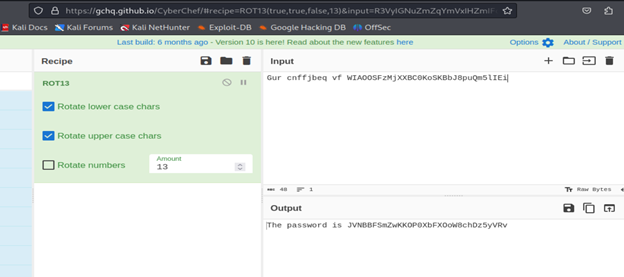
Level 12-level 13 Bandit
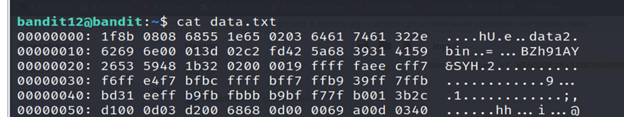
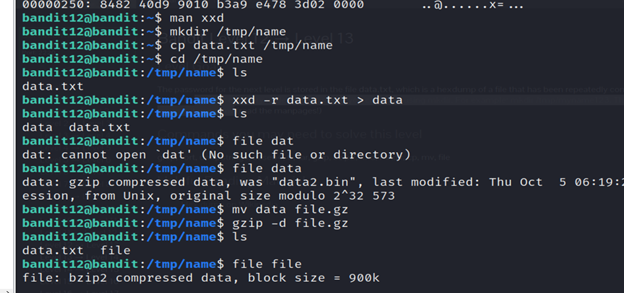
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed. For this level it may be useful to create a directory under /tmp in which you can work using mkdir. For example: mkdir /tmp/myname123. Then copy the datafile using cp, and rename it using mv (read the manpages!)
1-ssh [email protected] .org -p 2220
2-Enter the password found
In a hex dump, each byte (8 bits) is represented as a two-digit hexadecimal number. Hex dumps are commonly organized into rows of 8 or 16 bytes, sometimes separated by whitespaces.
3-Read the file data.txt using cat command.
4-Create a directory of name using mkdir command.
5-Then copy the datafile using cp.
6-The command (xxd -r data.txt > data) reads the hex dump from the file data.txt, reverses it back to binary, and then writes the binary data to a file named data.
7- list the files using ls.
8-The command (file data) will provide information about the type of the file named data.
9-The command (mv data file.gz) renames the file “data” to “file.gz without compressing it.
10-The command (gzip -d file.gz)decompresses the file file.gz. After running this command, the decompressed content will typically be written to a file without the .gz extension.
11-When you run the file command on a file named “file,” it will analyze the contents of that file and attempt to identify its type based on its content, rather than relying on the file extension.
12-The command (mv file file.bz2) renames the file “file” to “file.bz2.”
13-The command (bzip2 -d file.bz2) decompresses the file “file.bz2” and restores it to its original state. After running this command, you will have a file named “file” (without the “.bz2” extension), which contains the content of the decompressed file.
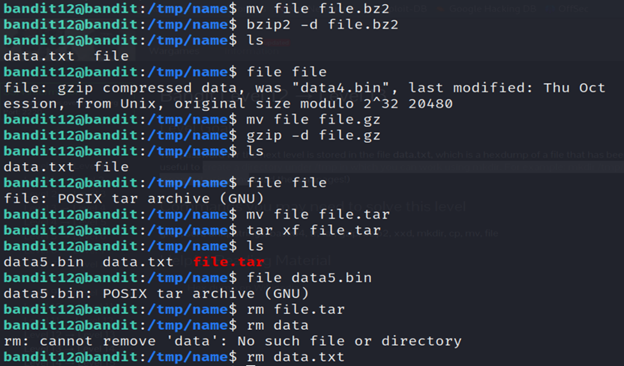
14-list the contents of the file.
15-Run the file command.
16-Run the command (mv file file.gz) renames the file “file” to “file.gz”.
17-Analyze the contents of file using file command.
18- The command (mv file file.tar) renames the file “file” to “file.tar”.
19- After running the command (tar xf file.tar), the contents of the “file.tar” archive will be extracted to the current working directory.
20- Analyze the contents of data5.bin using file command.
21-remove the file.tar file.
22-remove the data.txt file.
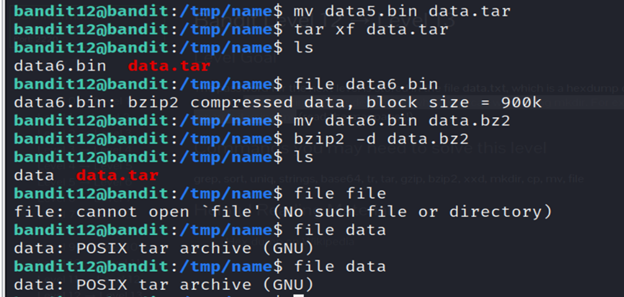
23-Again, we have to change the extension.
24- The command (mv data5.bin data.tar) renames the file “data5.bin” to “data.tar”.
25- After running the command (tar xf fdata.tar), the contents of the “data.tar” archive will be extracted to the current working directory.
26-list the contents.
27- Analyze the contents of data6.bin using file command.
28- The command (mv data6.bin data.bz2) renames the file “data6.bin” to “data.bz2”.
29- The command (bzip2 -d data.bz2) decompresses the file “data.bz2” and restores it to its original state. After running this command, you will have a file named “data” (without the “.bz2” extension), which contains the content of the decompressed file.
30- The command (mv data data.tar) renames the file “data” to “data.tar”.
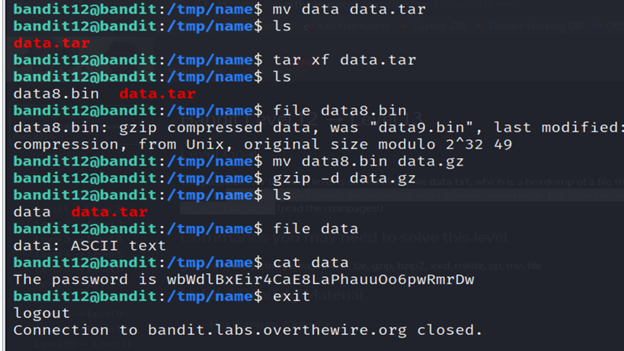
31-list the contents using ls.
32- After running the command (tar xf fdata.tar), the contents of the “data.tar” archive will be extracted to the current working directory.
33- list the contents using ls.
34- The command (mv data8.bin data.gz) renames the file “data8.bin” to “data.gz”.
35- The command (gzip -d data.gz)decompresses the file data.gz. After running this command, the decompressed content will typically be written to a file without the .gz extension.
36-list the contents using ls.
37- Analyze the contents of data file using file command.
38-Read the data file using cat.
39-And you got the password.
40-Exit from the level using exit command.
Level 13-level 14 Bandit
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-List the contents using ls command.
4-You will get the private ssh key.
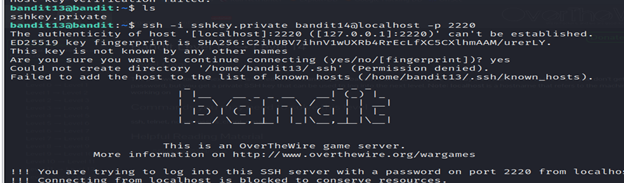
5- This command is trying to establish an SSH connection to the local machine (localhost) as the user bandit14, using the private key file sshkey.private for authentication, and connecting to port 220.
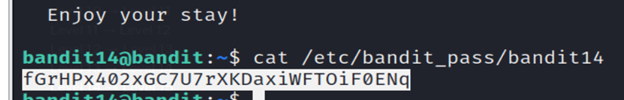
6- The password for the next level is stored in /etc/bandit_pass/bandit14 which can be found by using cat command.
Level 14-level 15 Bandit
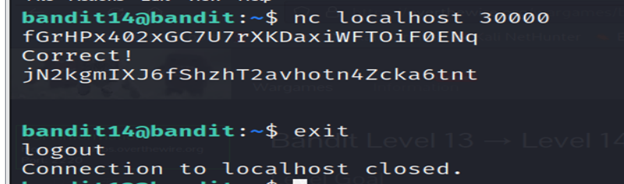
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3- This command attempts to open a network connection to the localhost on port 30000 using the nc (netcat) utility and we got the password.
4-Exit from the level.
Level 15-level 16 Bandit
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
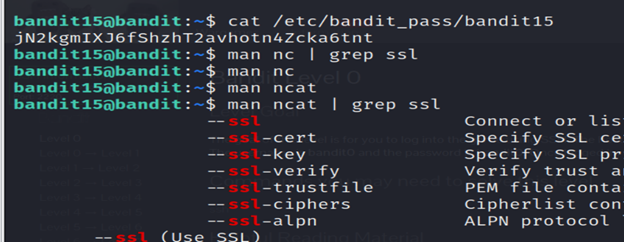
3- grep command is used to search for specific patterns or strings within files or the output of other commands.
4-ncat command is used for networking tasks, including port scanning, service probing, and creating network connections.
5- The command (man ncat | grep ssl) pipes the output of the man ncat command to grep, which searches for lines containing the string “ssl” in the manual page.
6- The command (ncat –ssl localhost 30001) attempts to establish a secure connection to localhost on port 30001 using SSL/TLS. The –ssl option signals to ncat that the connection should be secured with SSL.
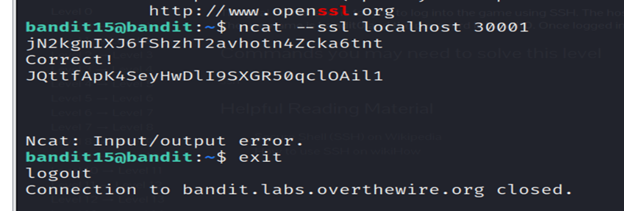
Level 16-level 17 Bandit
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
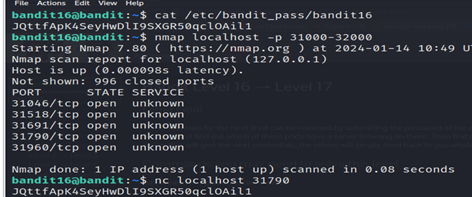
3- The nmap command is a powerful network scanning tool. The command is scanning the localhost (127.0.0.1) for open ports in the range from 31000 to 32000.
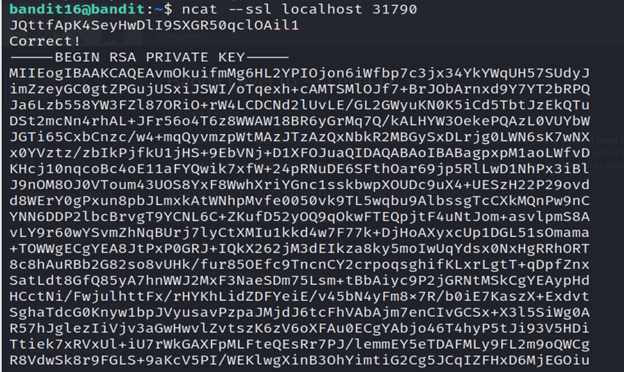
4- From the result of aggressive scanning using nmap, we can retrieve the credentials for the next level by submitting the password of the current level to port 31790.
5- Save the RSA PRIVATE KEY as the filebandit17.key .
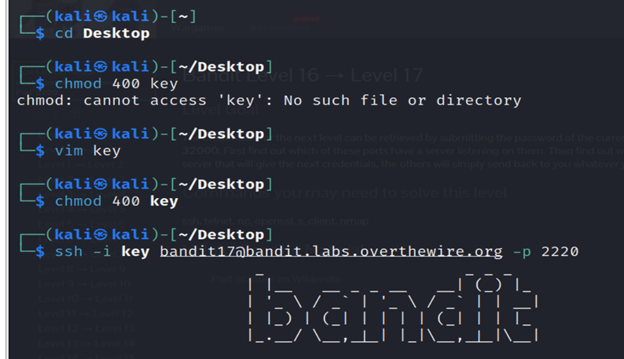
Level 17-level 18 Bandit
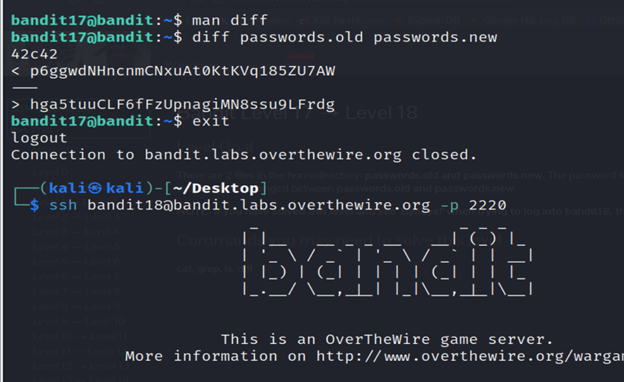
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-We’ll use diff command to compare two files (passwords.old and passwords.new) line by line.
4-exit the level.
Level 18-level 19 Bandit
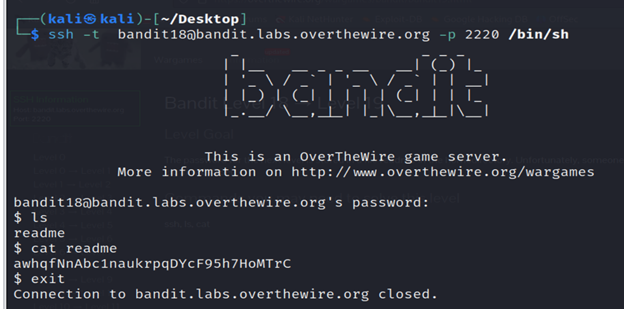
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
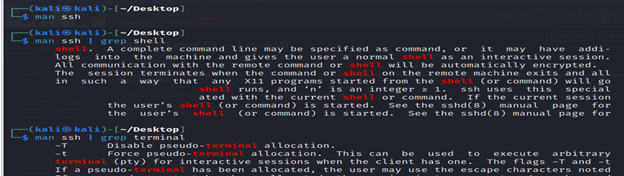
1- man ssh | grep terminal command searches the manual page for the ssh command for lines containing the string “terminal.” This can help you find information related to terminal-related features or settings in the context of using ssh.
2- It is an SSH command used to connect to the “bandit12” user on the OverTheWire Bandit server.
3- List the contents using ls where you’ll find readme file and in that readme file, you’ll get the password.
Level 19-level 20 Bandit
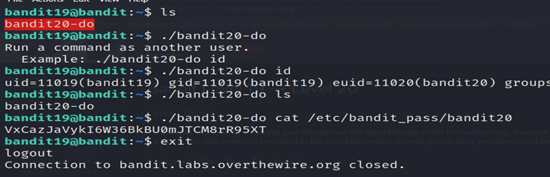
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it. The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-list the contents using ls.
4-: This is the command that is being executed with elevated privileges using the “bandit20-do” program. The id command typically displays information about the current user and group.
- ./bandit20-do: Executes the binary or script named “bandit20-do” in the current directory. This is a custom program provided in the Bandit game.
- id: This is the first command that will be executed using “bandit20-do”. The id command typically displays information about the current user and group.
- cat /etc/bandit_pass/bandit20: This is the second command that will be executed using “bandit20-do”. It tries to concatenate and display the contents of the “/etc/bandit_pass/bandit20” file.
5-exit the level.
level 20-level 21 Bandit
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
1-ssh [email protected] .org -p 2220
2-Enter the password found.
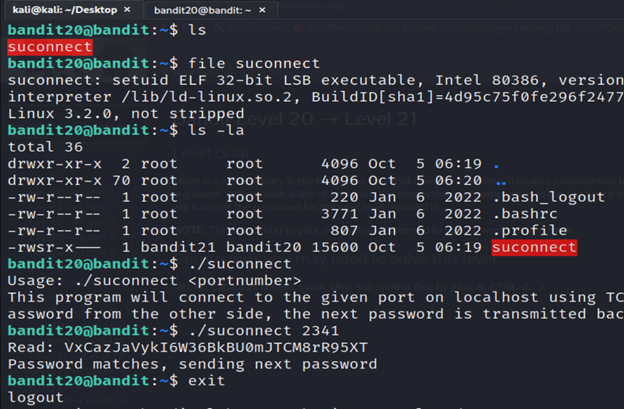
3-list the contents using ls.
4- Analyze the contents of suconnect using file command.
5- Now, we execute the setuid binary to connect localhost by 2341 port.
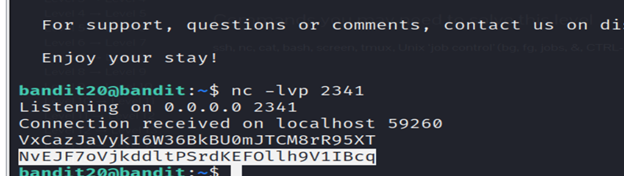
6-open another terminal and connect the previous one to that and that new terminal will give the password for level 21 using ssh.
- 7-l: Indicates that nc should listen for incoming connections.
- -v: Enables verbose mode, providing more information about the connections.
- -p 2341: Specifies the port number to listen on. In this case, it’s port 2341.
So, this command sets up a netcat listener on port 2341, waiting for incoming connections.
Level 21- level 22 Bandit
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
“Cron” in Kali Linux, as well as in other Linux distributions, refers to a time-based job scheduler. It allows users to schedule jobs (commands or scripts) to run periodically at specified intervals. These scheduled jobs are often referred to as “cron jobs.”
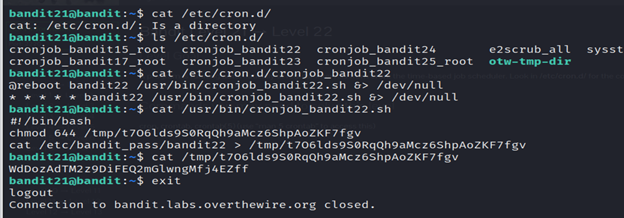
3-List the contents of cron.d using ls.
4- cat /etc/cron.d/cronjob_bandit22.sh is used to display the contents of the /etc/cron.d/cronjob_bandit22.sh file.
5-Read the file in the tmp folder using cat and you got the password.
Level 22-level23 Bandit
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
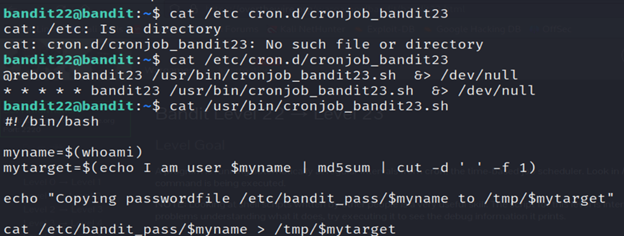
3-List the contents of cron.d using ls.
4- cat /etc/cron.d/cronjob_bandit23.sh is used to display the contents of the /etc/cron.d/cronjob_bandit23.sh file.
The md5sum command in Kali Linux (and other Linux distributions) is used to calculate and display the MD5 checksum of a file. The MD5 checksum is a fixed-size hexadecimal number generated from the content of the file. It is commonly used to verify the integrity of files by comparing the checksums before and after file transfers or downloads.
5-Read the file in the tmp folder using cat and you got the password.
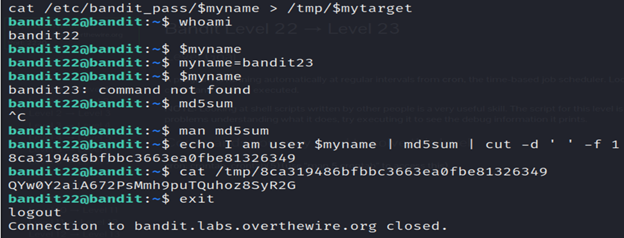
Level 23-level 24 Bandit
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-Make a directory and go yo that directory using cd.
4-List the contents of cron.d using ls.
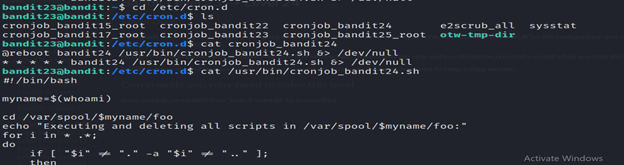
5- cat /etc/cron.d/cronjob_bandit24.sh is used to display the contents of the /etc/cron.d/cronjob_bandit24.sh file.
6-This command changes the current working directory to /var/spool/bandit24/foo.
- echo “cat /etc/bandit_pass/bandit24 > /tmp/certa_test.tst”: This echoes the specified command to the standard output.
- > certa6.sh: This redirects the standard output of the echo command to a file named certa6.sh.
7-cat /tmp/certa_test.txt is used to display the contents of the file named certa_test.txt located in the /tmp directory in Kali Linux.
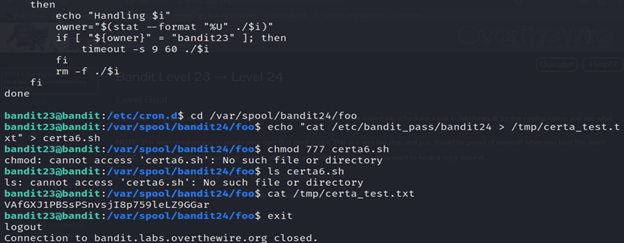
Level 24-level 25 Bandit
A daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
You do not need to create new connections each time
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3-make a directory tube and perform the commands in that directory.
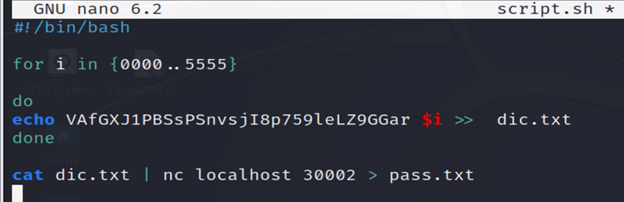
4-use the command nano script.sh to write code in the script.sh file.
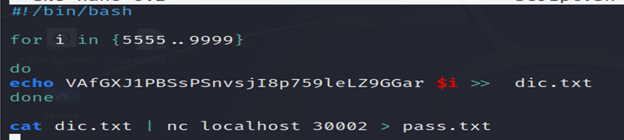
5-You’ll not get the password bcz the pincode is not between the 0000 to 5555 .Try again and make some changes in the nano script.sh file.
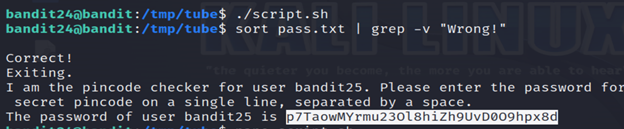
- sort pass.txt: Reads the content of the file pass.txt and sorts it alphabetically.
- |: Pipes the sorted output to the next command.
- grep -v “wrong”: Searches for lines that do not contain the string “wrong.” The -v option in grep inverts the match, meaning it selects all lines that do not match the specified pattern.
Level 25-26 Bandit
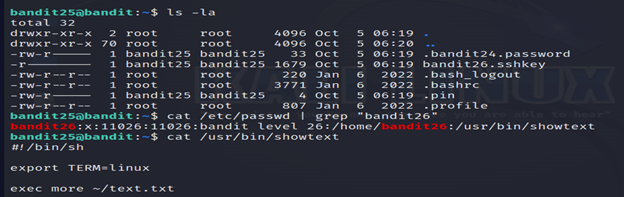
Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
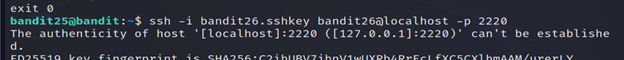
1-ssh [email protected] .org -p 2220
2-enter the password found.
3-The connection with the server will be closed automatically. That’s because the shell for user bandit26 is not /bin/bash.
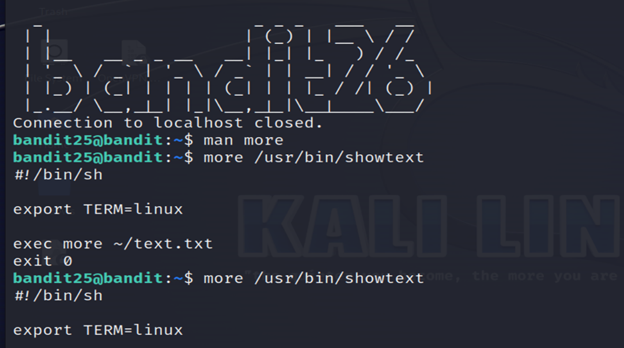
4-The script calls more on a file to show the ASCII art then exits directly. So, the more command may be the entry point which could be exploited by us to gain the normal shell. Now, we need to resize our terminal to trigger the more command having effects and go into the command view.
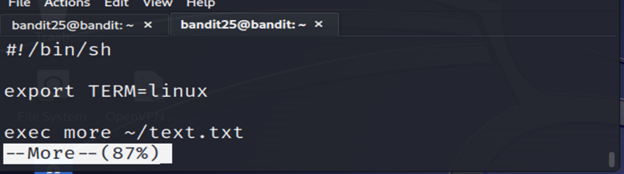
5-To edit a file being viewed with more press v. This will launch the text editor that is set in the $EDITOR shell variable at the line being viewed.
6-Input :e /etc/bandit_pass/bandit26 and enter the edited mode to check the password for bandit26.
Level 26-27 Bandit
Good job getting a shell! Now hurry and grab the password for bandit27!
1-go back to bandit 25 from where we left off.
2-Using :e we can run some commands in it
:e etc/bandit_pass/bandit26
:qa! To exit
3-To change the shell,run command
:set shell=/bin/bash
Now, we can access the shell of bandit26.
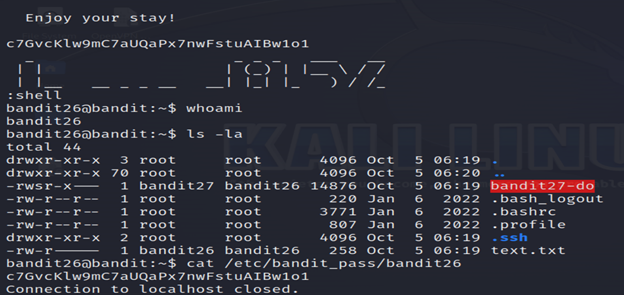
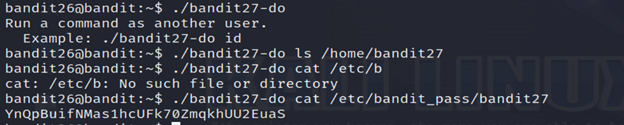
4-list the contents where you will find bandit27-do.
- ./bandit27-do: Executes the script or binary named bandit27-do.
- cat /etc/bandit_pass/bandit27: Uses the cat command to display the content of the file /etc/bandit_pass/bandit27.
And you’ll get the password for the next level.
Level 27-28 Bandit
There is a git repository at ssh://bandit27-git@localhost/home/bandit27-git/repo via the port 2220. The password for the user bandit27-git is the same as for the user bandit27.
1-ssh [email protected] .org -p 2220
2-enter the password found.
A Git repository (often abbreviated as “repo”) is a version control system that tracks changes in the source code during software development. It allows multiple contributors to work on a project simultaneously, facilitating collaboration, code review, and the ability to revert to previous states of the codebase.
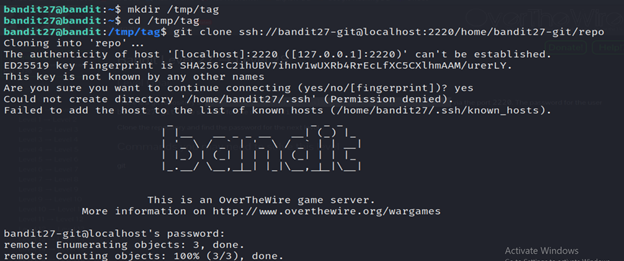
3- Create a new directory named “tag” in the “/tmp” directory.
4- is attempting to clone a Git repository using the SSH protocol. Here’s a breakdown of the command:
- git clone: Initiates the cloning process, creating a copy of the remote repository on your local machine.
- ssh://bandit27-git@localhost:2220/home/bandit27-git/repo: The URL of the Git repository. It specifies the SSH protocol (ssh://), the username (bandit27-git), the host (localhost), the port (2220), and the path to the repository (/home/bandit27-git/repo).
5-list the contents using ls.
6- cd repo/ changes the current working directory to the “repo” directory.
7- The ls -la command is used to list detailed information about files and directories in the current directory.
8-Read the README file using the cat command.
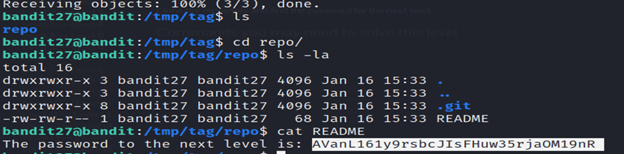
Level 28-29 Bandit
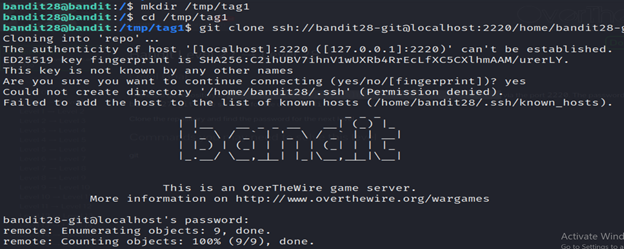
There is a git repository at ssh://bandit28-git@localhost/home/bandit28-git/repo via the port 2220. The password for the user bandit28-git is the same as for the user bandit28.
1-ssh [email protected] .org -p 2220
2-Enter the password found.
3- Create a new directory named “tag1” in the “/tmp” directory.
4- It is attempting to clone a Git repository using the SSH protocol. Here’s a breakdown of the command:
- git clone: Initiates the cloning process, creating a copy of the remote repository on your local machine.
- ssh://bandit28-git@localhost:2220/home/bandit28-git/repo: The URL of the Git repository. It specifies the SSH protocol (ssh://), the username (bandit28-git), the host (localhost), the port (2220), and the path to the repository (/home/bandit28-git/repo).
5- The ls -la command is used to list detailed information about files and directories in the current directory.
6- Read the README.md file using the cat command.
7- The git log command in Kali Linux is used to display a log of commit history in a Git repository. When executed in a Git repository, it provides information about the commit history, including details such as commit IDs, authors, dates, and commit messages.
8- The git show command in Kali Linux is used to display information about a specific Git object, such as a commit, tag, or tree. When you run git show, it provides detailed information about the latest commit by default.
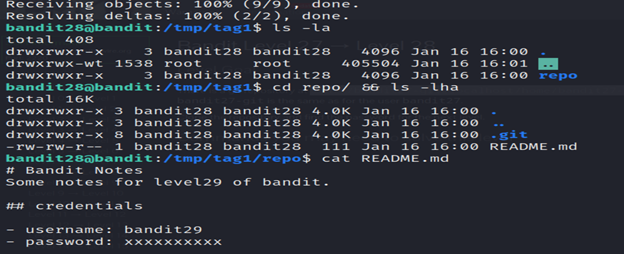
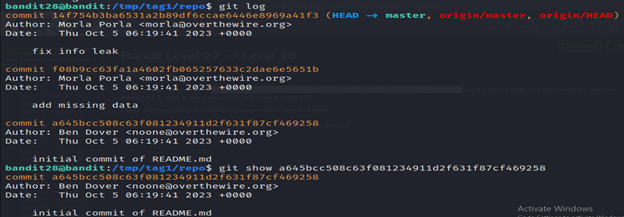
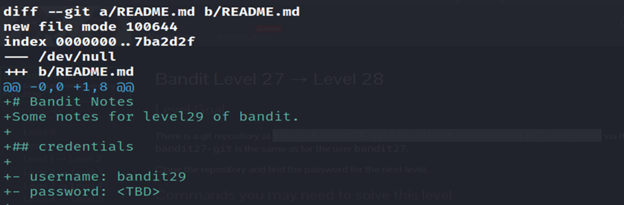
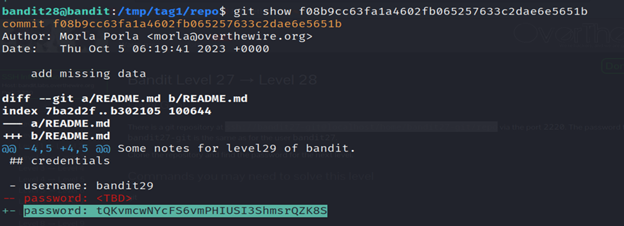
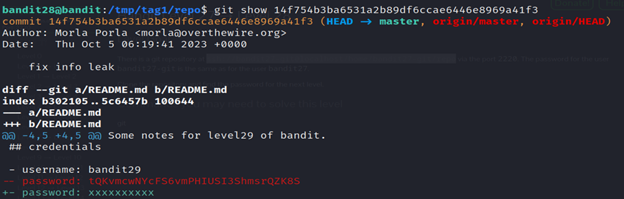
Level 29-30 Bandit
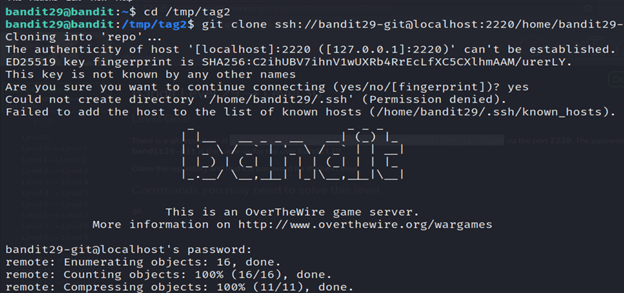
There is a git repository at ssh://bandit29-git@localhost/home/bandit29-git/repo via the port 2220. The password for the user bandit29-git is the same as for the user bandit29.
1-ssh [email protected] .org -p 2220
2-enter the password found.
3- Create a new directory named “tag2” in the “/tmp” directory.
4- It is attempting to clone a Git repository using the SSH protocol. Here’s a breakdown of the command:
- git clone: Initiates the cloning process, creating a copy of the remote repository on your local machine.
- ssh://bandit29-git@localhost:2220/home/bandit29-git/repo: The URL of the Git repository. It specifies the SSH protocol (ssh://), the username (bandit29-git), the host (localhost), the port (2220), and the path to the repository (/home/bandit29-git/repo).
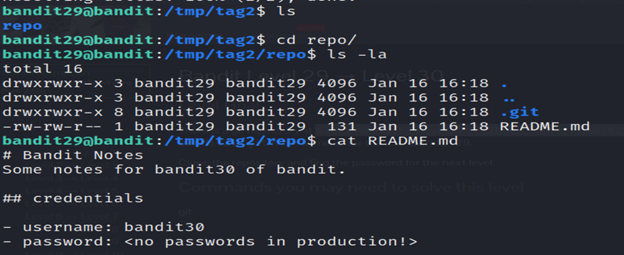
5- The ls -la command is used to list detailed information about files and directories in the current directory.
6- Read the README.md file using the cat command.
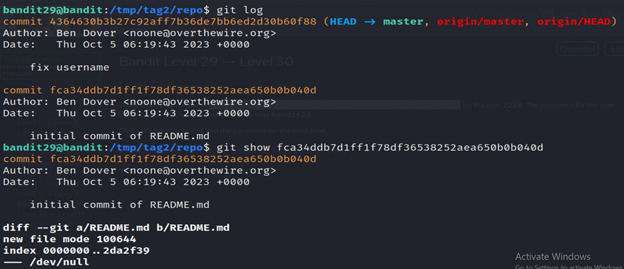
Run the git log and git show command. We’ll get no password.
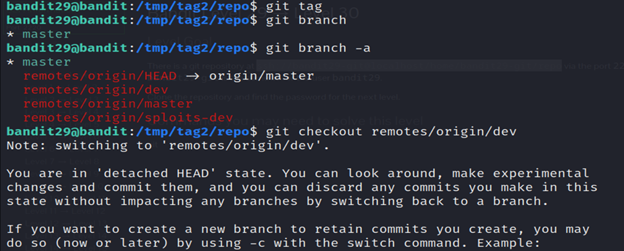
7- The git tag command in Kali Linux is used to create, list, delete, or verify tags in a Git repository.
8- The git branch command in Kali Linux is used to manage branches in a Git repository. It allows you to create, list, rename, and delete branches.
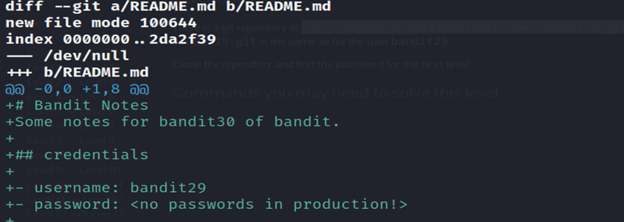
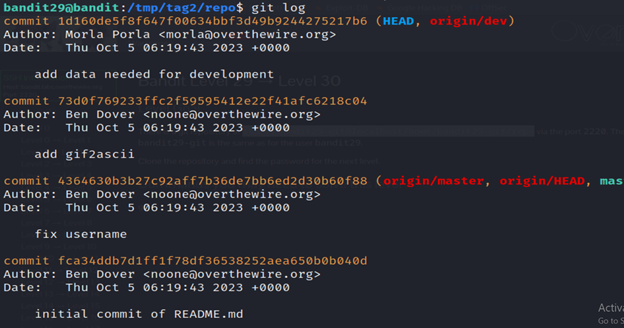
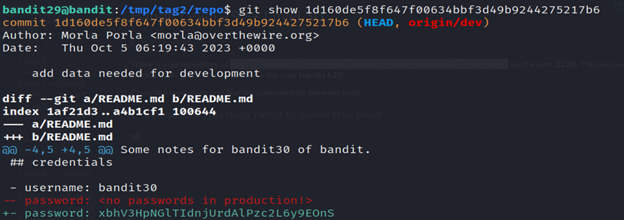
Then run the git log command and git show command and you’ll get the password.
Level 30-31 Bandit
There is a git repository ssh://bandit30-git@localhost/home/bandit30-git/repo via the port 2220. The password for the user bandit30-git is the same as for the user bandit30.
1-ssh [email protected] .org -p 2220
2-enter the password found.
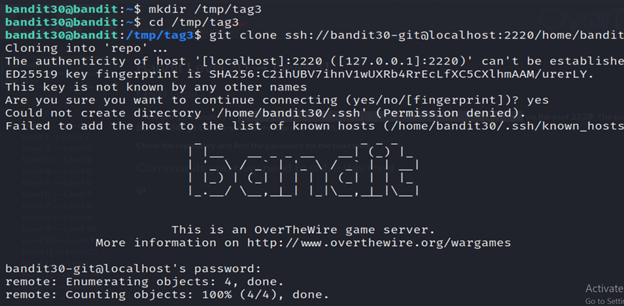
3- Create a new directory named “tag3” in the “/tmp” directory.
4- It is attempting to clone a Git repository using the SSH protocol. Here’s a breakdown of the command:
- git clone: Initiates the cloning process, creating a copy of the remote repository on your local machine.
- ssh://bandit30-git@localhost:2220/home/bandit30-git/repo: The URL of the Git repository. It specifies the SSH protocol (ssh://), the username (bandit30-git), the host (localhost), the port (2220), and the path to the repository (/home/bandit30-git/repo).
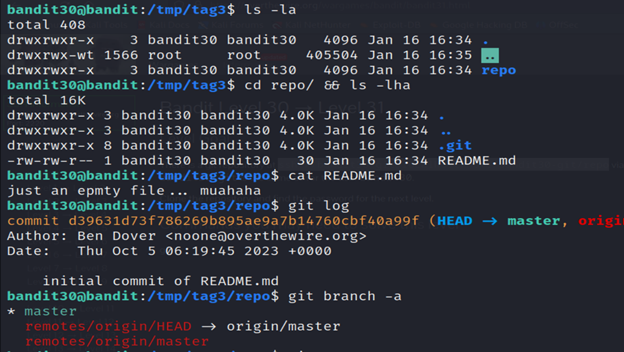
5-List the contents using ls.
6-Read the README.md file using cat.
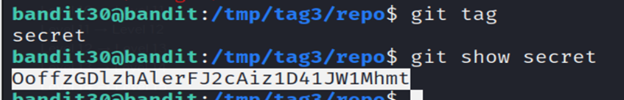
7-Run the git tag command and you’ll find a secret file.
If “secret” is a branch, tag, or commit in your repository, the git show command can provide information about that specific object.
And you’ll get the password.
Level 31-32 Bandit
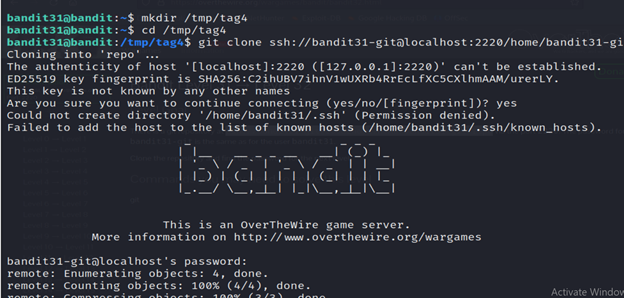
There is a git repository at ssh://bandit31-git@localhost/home/bandit31-git/repo via the port 2220. The password for the user bandit31-git is the same as for the user bandit31.
1-ssh [email protected] .org -p 2220
2-enter the password found.
3- Create a new directory named “tag4” in the “/tmp” directory.
4- It is attempting to clone a Git repository using the SSH protocol. Here’s a breakdown of the command:
- git clone: Initiates the cloning process, creating a copy of the remote repository on your local machine.
- ssh://bandit31-git@localhost:2220/home/bandit31-git/repo: The URL of the Git repository. It specifies the SSH protocol (ssh://), the username (bandit31-git), the host (localhost), the port (2220), and the path to the repository (/home/bandit31-git/repo).
5- The ls -la command is used to list detailed information about files and directories in the current directory.
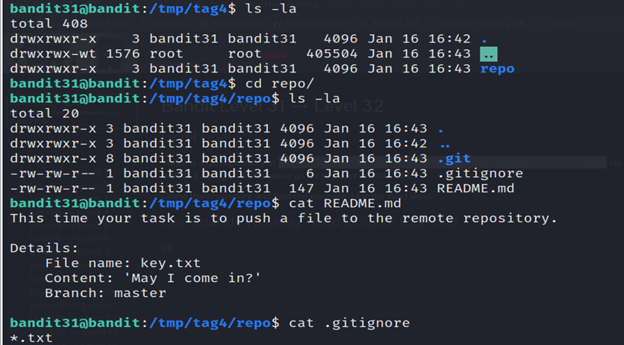
6- Read the README.md file using the cat command.
7- The .gitignore file specified intentionally untracked files to ignore. We can remove the .gitignore file first and then push the file to the repository again.
The cat .gitignore command in Kali Linux is used to display the contents of the .gitignore file. The .gitignore file is commonly used in Git repositories to specify files and directories that should be ignored and not tracked by version control.
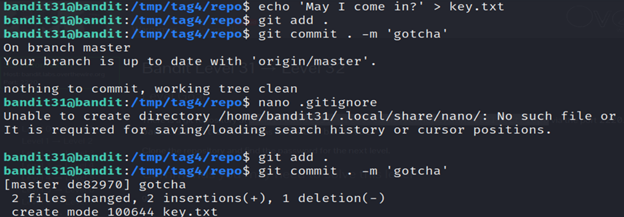
8- git add . will add all changes, including potentially unwanted files.
9- git commit. -m ‘gotcha’ is used to commit changes to the Git repository with a commit message
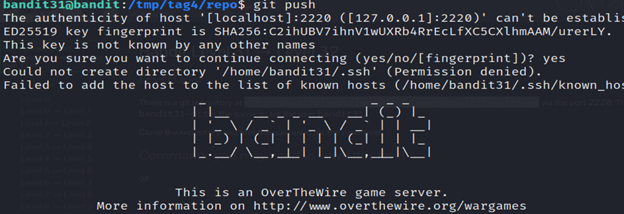
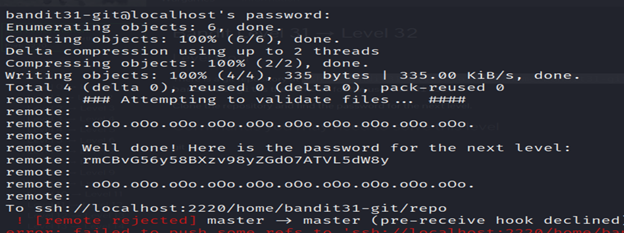
10- The git push command in Kali Linux is used to update a remote repository with local commits. It sends the committed changes from your local repository to the remote repository.
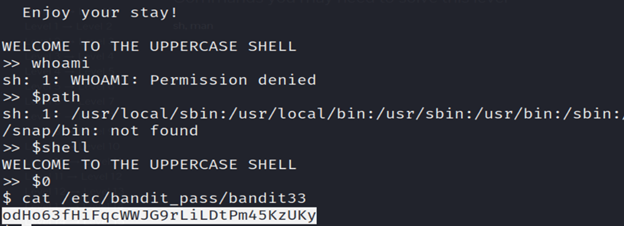
Level 32-33 Bandit
After all this git stuff it’s time for another escape. Good luck! The shell converts every command into uppercase. We need to fix it and gain the normal shell again. Since this is an interactive shell, we have the chance to execute it again using the variable $0.