Takeover is an easy room from Try hack me which is focused on subdomain enumeration and extracting information from SSL certificates. In this THM takeover write up, we are going to see how we can solve this room is a systematic manner.
The room details a simple explanation of what we need to do. A domain is given and we need to find the security vulnerability.
Hello there,
I am the CEO and one of the co-founders of futurevera.thm. In Futurevera, we believe that the future is in space. We do a lot of space research and write blogs about it. We used to help students with space questions, but we are rebuilding our support.Recently blackhat hackers approached us saying they could takeover and are asking us for a big ransom. Please help us to find what they can takeover.
Our website is located at https://futurevera.thmHint: Don’t forget to add the MACHINE_IP in /etc/hosts for futurevera.thm ; )
Table of Contents
Try Hack Me Takeover – Step by Step
1. Download Seclists
We will be using seclists to enumerate directories and subdomain. So, download it.
sudo apt-get install seclists2. Scan the target
Scan the target with Nmap. We get port 80,443 and 22 open.
sudo nmap -sS -T5 -sV -O IPADDRESS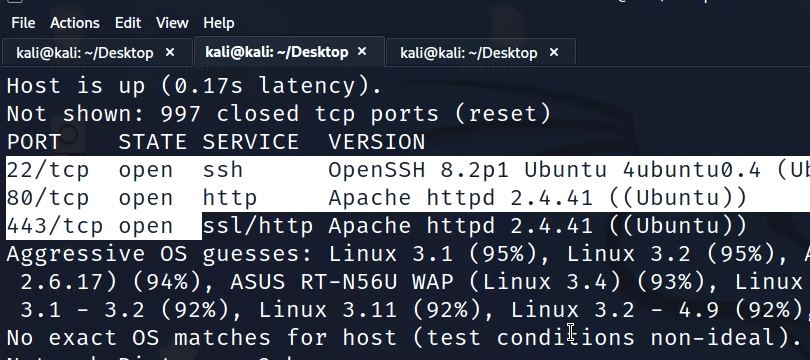
3. Add the website to hosts
As we are already given the domain, add it to hosts file
sudo nano /etc/hosts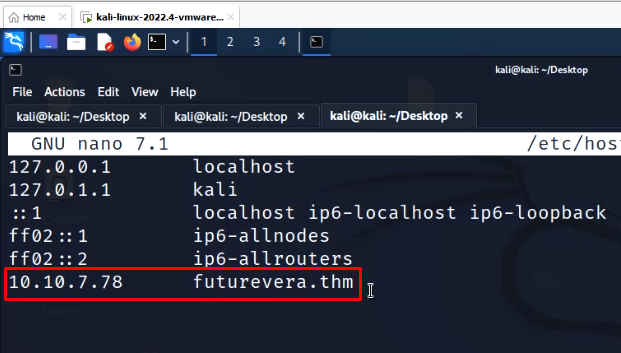
4. Enumerate Subdomain
There is nothing on main website. Lets enumerate the subdomains with Gobuster.
gobuster vhost -u https://futurevera.thm -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -k --append-domain 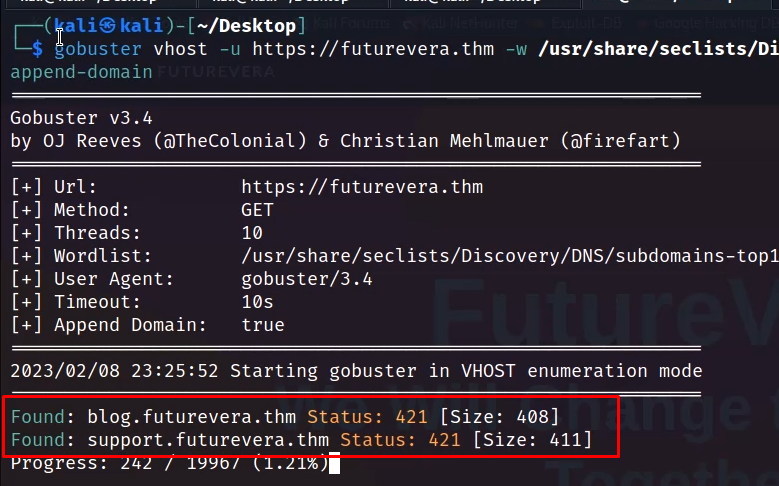
You can also do it with FFUF.
ffuf -u https://futurevera.thm -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -H "HOST:FUZZ.futurevera.thm"If ffuf fails to work, use IP address instead of domain name.
So we get two subdomain.
- blog
- support
Now add both these to hosts file.
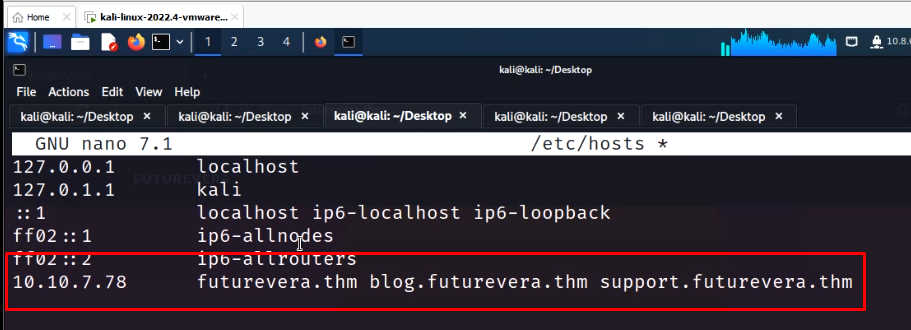
5. Get the flag
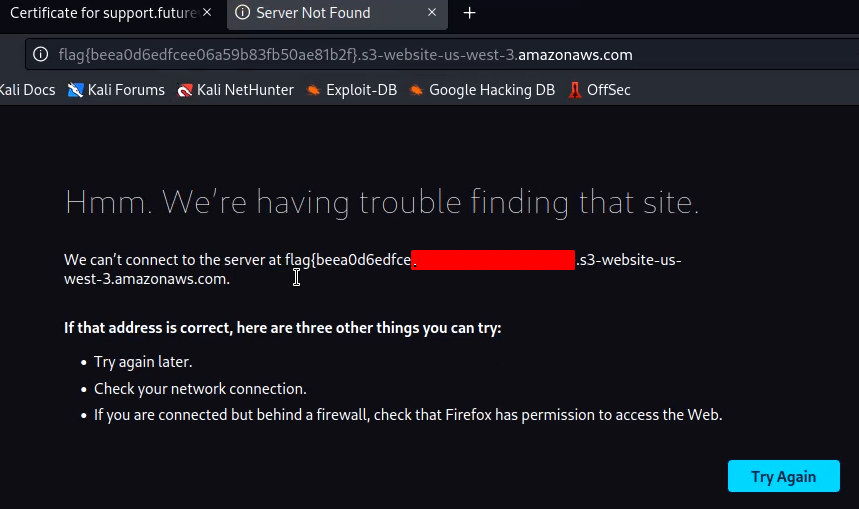
Visit the support page and view the certificate. We will get a new subdomain in DNS names.
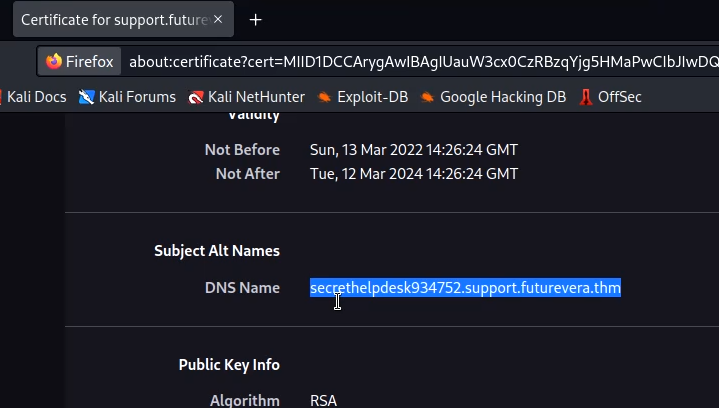
Add this subdomain to hosts file. Visit it on Http and we will get the flag displayed as error.